Privilege escalation attacks are a critical element of most cyber threats today. Let’s explore what these attacks are, how adversaries perform them and effective strategies for defending against them.
What are privilege escalation attacks?
Privilege escalation attacks are attempts by adversaries already inside a network to gain additional access rights. In particular, these attacks are often aimed at gaining control of administrative accounts, which have significantly more power than regular user accounts.
It’s common to think of privilege escalation attacks as a tool used by external threat actors who have gained a foothold in the network. But they are also launched by malicious insiders, such as disgruntled employees who want to damage the organization or contractors looking to steal intellectual property (IP) or personally identifiable information (PII) for personal gain.
What is privilege escalation?
More precisely, privilege escalation is one tactic that adversaries can use in the course of a cyberattack. The MITRE ATT&CK matrix details 14 tactics that form what’s known as the cyber kill chain. At a high level, these tactics can be grouped into three categories (with privilege escalation falling into the second one):
- Get in — First, an adversary needs to get inside the victim’s network. Using tactics like reconnaissance and initial access, they might use social media to identify individuals who work at a potential target company and craft effective phishing or spear-phishing campaigns to steal their credentials. Or they can use simpler methods, like brute-force password-guessing attacks or even offering employees a share of an eventual ransom payment in exchange for providing their corporate credentials. (Of course, malicious insiders can skip this phase altogether, since they’re already inside the network.)
- Move around — Once inside, cybercriminals have a few key goals: Maintain their access, expand their reach, locate valuable resources and remain undetected. Privilege escalation attacks are a valuable part of this phase. But adversaries have many other tactics at their disposal, including persistence, lateral movement, discovery and defense evasion.
- Complete the mission — Once the adversary has located valuable assets and has the rights to access them, they can complete their mission. If their ultimate goal is to steal data, they use exfiltration techniques such as transferring data to a physical USB device or to a cloud account they control. If it’s to manipulate, interrupt, or destroy your systems and data, they can choose from a variety of impact techniques, from encrypting data to wiping entire disks to shutting down systems. They may take steps to erase their footprints, as well as leave behind back doors (such as user accounts, Trojans, rootkits and hardware devices) to enable them to reenter the network later.
Examples of privilege escalation attacks
One particularly relevant example of privilege escalation attacks is ransomware. It’s a common misconception that ransomware runs as soon as it is deployed in a network. Today, many ransomware attacks are human-operated, and privilege escalation plays a key role. Let’s map such an attack on to the framework we just described:
- Get in — A ransomware attack often begins with a phishing campaign: The criminals send emails to users inside an organization that entice them to visit a malicious site where they are tricked into supplying their login credentials. By logging in with those credentials, the criminals now have a foothold in the network.
- Move around — However, any ransomware they run can encrypt only the files that the compromised user account has access to. While that might inconvenience the target organization, it’s not likely to result in the hefty ransom payout that the cybercriminals are seeking. Therefore, the ransomware operators conduct privilege escalation attacks to steadily gain higher levels of access to additional (and more valuable) data across the IT ecosystem.
- Complete the mission — Once they become capable of doing the serious damage that maximizes their chances of extorting a payout, the adversaries unleash the ransomware and demand payment.
Privilege escalations attacks are by no means limited to ransomware campaigns. Indeed, they are a key element of most cyberattacks, whether the goal is to encrypt data, steal content or disrupt business operations. Adversaries typically start with relatively limited permissions, so they need to perform privilege escalation to be able to locate and access the victim organization’s most sensitive systems and data.
Horizontal vs vertical privilege escalation
Sometimes privilege escalation is described as horizontal or vertical:
- Horizontal privilege escalationis an attempt to gain control of another account with a similar level of access that they already have. However, it’s more precise to call this lateral movement rather than privilege escalation, since the attackers aren’t escalating their rights to a higher level.
- Vertical privilege escalation is when an adversary attempts to increase their access to a higher level than they currently have. These are true privilege escalation attacks.
How do privilege escalation attacks work?
One of the primary techniques used for privilege escalation is abuse of legitimate accounts. Malicious actors have two primary options:
Take over a different account that has higher permissions.
Some privilege escalation attacks are aimed at compromising more powerful accounts than the adversary currently controls. Targets for takeover include:
- User accounts with access to more valuable data or systems — Example include the accounts belonging to executives, legal teams or financial officers.
- Local administrator accounts — These accounts have full control on a particular machine.
- Service accounts — Service accounts are used to run services and applications, including essential workloads like Exchange, SharePoint, SQL Server and Internet Information Services (IIS).
- Admin accounts — The holy grail for adversaries is compromising accounts that are members of highly privileged groups like Domain Admins or Enterprise Admins.
Unfortunately, compromising accounts can be surprisingly easy. Especially valuable and vulnerable are the default accounts built into systems (such as the Guest and Administrator accounts on Windows), service accounts, and the root user account in cloud services like AWS. All too often, these accounts retain the default usernames and passwords established during system deployment, so it’s a snap for adversaries to take control of them.
Also at high risk are user accounts with weak passwords or passwords that their owners have reused across sites, especially if they are secured with only single-factor authentication. Adversaries can also harvest hashed passwords from the LSASS memory of a machine and use them to perform pass the hash attacks in which they authenticate as an Active Directory account without ever knowing the account’s cleartext password (the actual string of characters that the user types to log in). Indeed, if IT pros use their admin accounts to log on to workstations, LSASS memory can be a goldmine for malicious actors.
Increase the access rights of an account they already control.
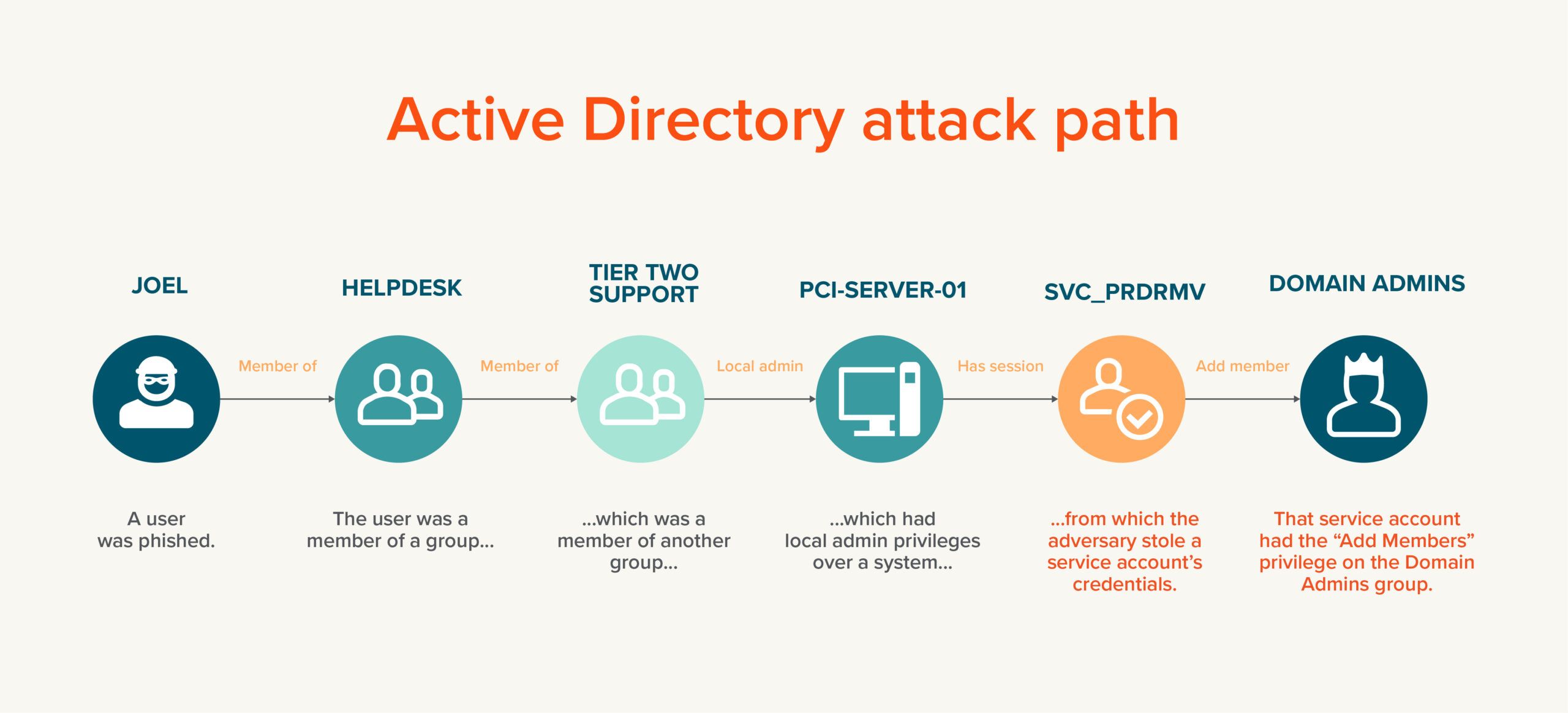
Adversaries can also perform privilege escalation attacks to increase the rights of accounts they have already compromised. Unfortunately, this can also be surprisingly easy. Using an open-source tool called BloodHound, adversaries can quickly map out all the attack paths in the Active Directory environment. An attack path is a chain of actions that could enable an attacker to gain administrative privileges, or even full control of the IT environment. These steps can involve abusing things like concealed permissions, nested group membership and inherent security gaps in AD architecture.
Organizations often have literally hundreds or even thousands of these attack paths, many of which may involve only a handful of steps. BloodHound will lay them out in detail.
Other techniques used in privilege escalation attacks
Beyond abuse of valid accounts, there are many other privilege escalation techniques. Often, they rely on taking advantage of weaknesses and vulnerabilities in the target network, such as software bugs, misconfigurations and incorrect access controls. In fact, the MITRE knowledgebase lists a whole host of techniques that can be used in privilege escalation attacks. Here are just a few of them.
Abuse of elevation control mechanisms
Most systems today include mechanisms designed to limit what a user can do and to require authorization for riskier tasks. But adversaries can use various techniques to abuse or bypass these built-in control mechanisms.
For instance, Windows User Account Control (UAC) can prompt a user for confirmation before allowing a program to elevate its privileges. But an adversary can use privilege escalation attacks to essentially click through the prompt to complete the desired action.
Access token manipulation
Windows uses access tokens to determine the owner of a running process and check whether that user has sufficient permissions to perform the requested action. By manipulating these tokens, malicious actors can trick the system into believing that the process belongs to a different user and therefore granting it the permissions of that user.
Domain policy modification
Another technique used in privilege escalation attacks is to modify the configuration settings of the domain. In particular, adversaries can escalate their privileges by modifying Group Policy objects (GPOs). For instance, they might disable a GPO in order to gain the privilege of running a certain application.
Supply chains and privilege escalation attacks
Privilege escalation attacks offer multiple reasons to pay close attention to your supply chain. Adversaries can abuse the software, hardware and services provided by third parties to gain a foothold in your network that they can use to elevate their privileges. Organizations should verify that every element in their supply chain is trusted, since a change that a supplier sends out could be used to establish a foothold through proxy.
Remember that computer chips, IoT devices and other hardware can also contain vulnerabilities that facilitate privilege escalation. For instance, Meltdown and Spectre exploit vulnerabilities in modern processors to steal data that could be used for privilege escalation, such as passwords stored in a browser or password manager. While some of these flaws are unintentional, others can be deliberately planted by nation-states or other organized malicious actors. For example, Chinese telecommunications company Huawei faces accusations that Beijing could use its 5G infrastructure for espionage.
How to prevent and block privilege escalation attacks
Prerequisite: Understand your Tier 0 assets.
Because privilege escalation attacks can enable malicious actors to gain higher levels of access to more valuable IT assets, blocking these attacks is vital. A wide range of tools can be helpful in this effort, including identity and access management (IAM) and privileged access management (PAM) solutions.
While it can be tempting to simply start implementing solutions, it’s smart to step back and think strategically. The first order of business must be to understand that the goal of cyberattacks is to reach your critical systems and data, often by compromising the most powerful accounts in your environment. These are called your Tier 0 assets, and understanding them is the critical first step in defending against privilege escalation attacks.
In an Active Directory environment, Tier 0 assets include domain controllers (DCs) and other powerful servers, as well as all accounts that have direct or indirect administrative control over the AD forest, domains or DCs. The accounts that probably leap to mind are those belonging to your IT pros. But all too often, powerful security groups like Domain Admins and Enterprise Admins have a boatload of members. One common example is service accounts because vendors often claim their applications require these elevated privileges.
Notice that I said “direct or indirect control.” It’s vital to also uncover accounts that could gain elevated privileges, such as membership in Domain Admins. As noted earlier, the steps involved in this process are called an attack path. Accordingly, mapping out the attack paths in your environment is essential to getting an accurate picture of your Tier 0 assets.
Enforce least privilege.
Once you’ve gotten a full inventory of your Tier 0 assets, the next job is minimizing them to reduce your attack surface area. The goal is to enforce the principle of least privilege, which dictate that each account be granted only the access it requires for the tasks it needs to perform.
Minimizing the membership of your privileged security groups is fairly straightforward (though not necessarily easy!). In addition to removing user accounts for your employees and contractors, you may need to push back on vendors that demand excessive privileges for service accounts.
Reducing your Tier 0 assets helps prevent privilege escalation attacks — and it also facilitates detecting those attacks. I’ll talk about incident detection in a moment, but it’s worth mentioning that the fewer Tier 0 assets you have to monitor, the easier it is to keep a close eye on them and spot true threats.
Choke off attack paths.
It’s important to extend your least-privilege mission to accounts that have indirect administrative rights. Through attack path management, you can map out these indirect routes to control of your environment and pinpoint the choke points that they share. By mitigating those choke points, you can dramatically reduce the opportunity for privilege escalation. For more information, check out the e‑book, “Level up your Active Directory security with attack path management.”
Manage the identity lifecycle.
Managing the identity lifecycle involves controlling account provisioning, re-provisioning and deprovisioning. Make sure that you grant new users exactly the access they need, and that as users change roles within the organization and projects are completed, accounts don’t end up with legacy privileges.
Deprovisioning is also critical. One key target of privilege escalation attacks is orphaned accounts — they have no owner to notice they’ve been hijacked, but they already exist in the system so using them is unlikely to raise alarms.
Establish strong credential management.
As we’ve seen, privilege escalation attacks often involve compromising credentials. Strategies that help prevent adversaries from taking over accounts include implementing strong password policies and eliminating default and hardcoded credentials. And multifactor authentication (MFA) can render compromised credentials useless, so be sure to require it for privileged accounts.
Use managed service accounts (MSAs).
To reduce the risk of service accounts being taken over as part of privilege escalation is to use standalone managed service accounts (sMSAs) or group managed service accounts (gMSAs). MSAs provide automatic password management to ensure that service account passwords (and their hashes) change on a regular basis, and gMSAs are restricted from being used interactively.
Harden systems and applications.
Adversaries often exploit misconfigurations and vulnerabilities to elevate their access rights. Be sure to configure your systems and applications in accordance with best practices, proactively look for and mitigate vulnerabilities, and stay current on updates and patching management.
In addition, you can use change management solutions to proactively block changes to critical accounts, security groups and Group Policy objects — thwarting many privilege escalation attacks.
Implement supply chain risk management.
Be sure to carefully vet all your business partners, suppliers and other third parties that play a role in your IT ecosystem, whether they offer services, hardware, on-premises software, IoT devices, cloud applications or other components. Your goal should be to implement a robust supply chain risk management strategy yourself — and, as much as possible, do business only with organizations that have one as well.
Why prevention measures are not enough
It’s vital to keep in mind that even the best prevention measures cannot block all privilege escalation attacks. Accordingly, it’s important to implement a defense-in-depth strategy that also addresses threat detection and response, as well as enterprise backup and recovery.
Audit activity in the IT environment.
Be sure to continually monitor for suspicious activity that might indicate an attempt at privilege escalation or an account that has already been compromised. As noted earlier, minimizing your Tier 0 assets helps you zero in (if you’ll pardon the pun) on activity related to your most critical assets.
If there are attack paths that you’ve identified but have not yet been able to mitigate, be sure to watch them especially closely (this is called attack path monitoring).
Build (and test) a comprehensive enterprise backup and recovery strategy.
In case worst comes to worst, you also need to be able to restore your IT environment quickly. Remember that Active Directory backup and recovery is a critical ingredient; if your Active Directory is down, authorization and authentication cannot happen, so your business will be at a standstill. Consider the right Active Directory backup methodology for your organization, and be sure your Active Directory recovery solution doesn’t restore malware and backdoors along with your systems!
Conclusion
Privilege escalation is a key tactic used by adversaries during the course of a cyberattack. In order to achieve their goal — whether that’s to steal data, unleash ransomware or bring down systems — they need to gain high levels of access to your most vital systems and data. Defending against privilege escalation attacks requires a defense-in-depth strategy that emphasizes identifying, reducing and locking down your Tier 0 assets, as well as implementing effective auditing and disaster recovery strategies.