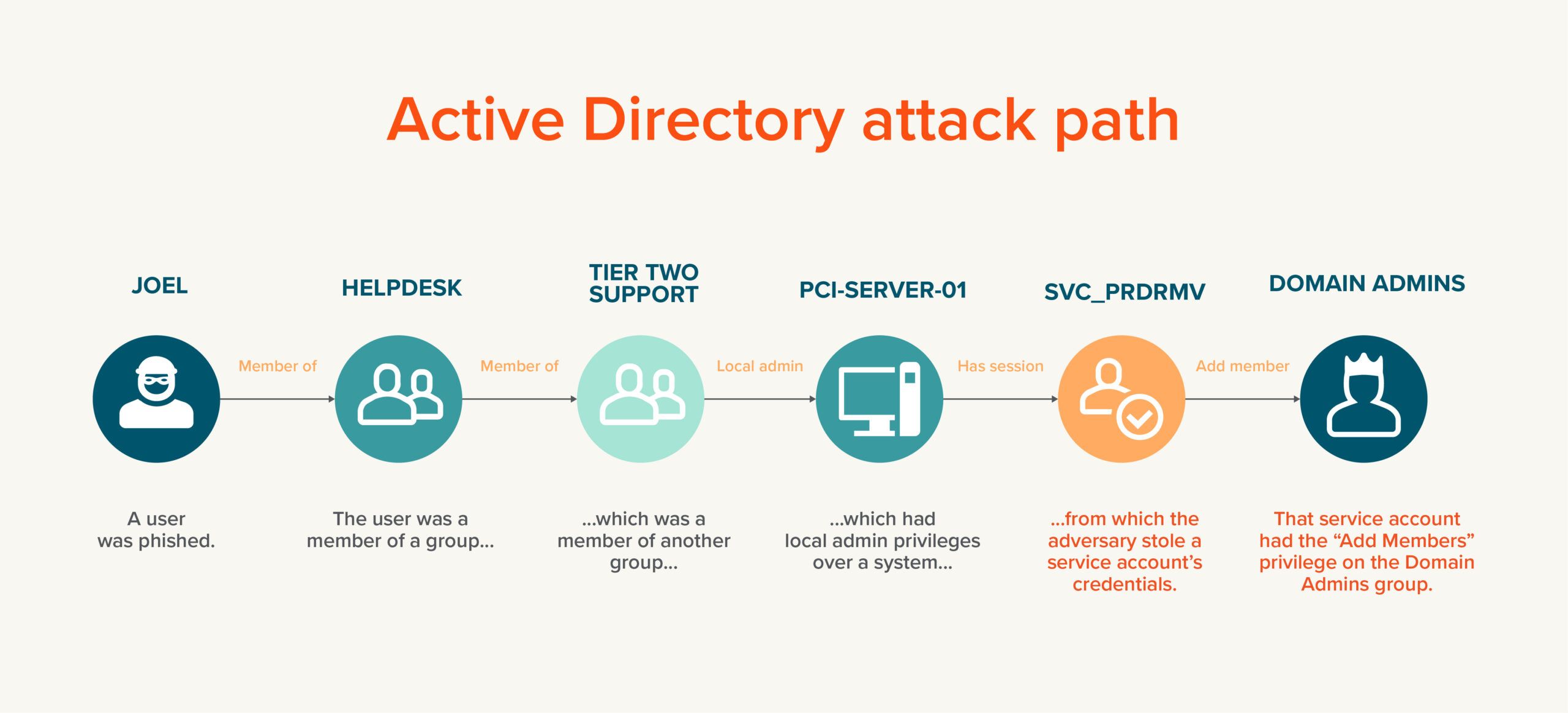
Attack paths are at the forefront of cybersecurity discussions today. But exactly what is an attack path? Why is Active Directory (AD) particularly vulnerable? And what can you do to protect your organization? This blog post covers all these questions and more.
What is an attack path?
The best way to understand what an attack path is involves understanding what it is not. IT pros are very familiar with two vital best practices for securing Active Directory: patching and vulnerability management. Patching is the process of applying updates to fix code-based vulnerabilities that could be exploited by adversaries, such as flaws in the Microsoft Windows Server operating system. Vulnerability management adds another layer of security by identifying and remediating misconfigurations in Active Directory that adversaries could exploit, such as allowing them unlimited attempts to guess a user’s password.
An attack path is not a code-based vulnerability or a single misconfiguration. Rather, an attack path is a chain of abusable privileges and actions that could enable an attacker who compromises a user account to gain administrative privileges, or even full control of the IT environment.
Why is Active Directory particularly vulnerable?
Attack paths are an issue for any identity and access management (IAM) system, because taking control of the identity platform gives an adversary full control of all of the organization’s users, systems and data.
But the problem is most acute for Active Directory, for several reasons. First, Active Directory is by far the most widely used directory service: It’s widely reported that 95 percent of Fortune 1000 companies use Active Directory. Therefore, adversaries who focus on understanding and exploiting attack paths in Active Directory have a huge number of targets to pick from. Moreover, they have a variety of tools at their disposal, including BloodHound, Mimikatz and Responder, that have been specifically designed to abuse features of Active Directory and Windows.
Another factor that makes Active Directory vulnerable to having attack paths is its complexity and lack of transparency. AD administrators have a wide range of options for granting permissions to accounts, including both directly and through Active Directory security groups, and Group Policy offers literally thousands of settings that also affect access control. At the same time, it’s nearly impossible to accurately audit permissions to determine, for example, who has permissions on a particular AD object or what effective rights have been granted to a security group.
Similarly, it can be hard to properly manage permissions to Group Policy objects (GPOs); you need to consider not only permissions the GPO itself, but to the Group Policy Creator Owners group, the System/Policies folder in AD, the sysvol folder on domain controllers (DCs), and the gpLink and gpOptions attributes on the domain root and organizational units (OUs). Furthermore, it’s a real challenge to uncover and overcome issues like inheritance blocking, improper link priority and failure to place computers in the correct OU.
Finally, there’s the inexorable march of time. Active Directory has been around for more than two decades — plenty of time for many organizations to build considerable technical debt in the form of convoluted policies, deeply nested privileges and more. Together, these factors make attack paths virtually inevitable in any Active Directory environment — and a very pressing cybersecurity concern.
The five stages of a cyberattack
As we’ve seen, attack paths enable an attacker to take control of Active Directory. And taking control of AD enables them to achieve their true goal: to steal data, unleash ransomware, cause downtime and so on.
This process generally takes time; indeed, the average dwell time of an intruder in an IT ecosystem is now a staggering 287 days, or more than 9 months. To understand how this all works, let’s review the five stages of a cyberattack.
1. Reconnaissance
Adversaries start by identifying target organizations and collecting information about them. Key focuses include what valuable data they might be able to steal, how big a payoff they could get from a ransomware attack, and how difficult the mission is likely to be. Reconnaissance can be passive, which involves using public sources such as tax records, job postings and social media to discover what systems and applications the organization uses, the names of its employees, and so on. Reconnaissance can also involve active techniques like network and port scanning to understand the target organization’s network architecture, firewalls and intrusion detection programs, operating systems and applications, and the services hosted on its ports.
2. Planning
Next, the attacker determines which attack vector to use for infiltration. Examples include exploiting a zero-day vulnerability, launching a phishing campaign, or bribing an employee to provide credentials or deploy malware.
3. Intrusion
The adversary then uses the chosen attack vector to attempt to breach the organization’s network perimeter. For instance, the adversary might succeed in guessing an employee’s user ID and password, gain entry through an unpatched or misconfigured system, or trick an employee into launching malware hidden in a malicious attachment to a phishing email.
4. Lateral movement and privilege escalation
Once inside the network, the adversary will seek to escalate their privileges and compromise additional systems in order to locate sensitive data or reach other critical resources. They also want to maintain their access. To achieve this persistence, they might create new user accounts, modify settings or even install backdoors.
This is where attack paths come into play. By leveraging an attack path, an adversary can escalate their privileges from ordinary user to administrator and even to Domain Admin, which gives them unlimited power in the domain.
Moreover, by compromising authorized user and admin accounts, adversaries can make their activity difficult to spot. And once they have claimed sufficient privileges, they can further evade detection by causing systems to falsely report that everything is working normally.
5. Exfiltration and cleanup
Last, the adversary exfiltrates or encrypts the organization’s data, or perhaps corrupts systems to disrupt business operations. In addition, they often also try to cover their tracks in order to thwart investigations and keep the organization from enhancing their defenses against future attacks. Techniques include uninstalling programs or scripts used in the attack, deleting any folders or accounts that they created, and modifying, corrupting or deleting audit logs.
What are some common attack paths?
An attack path often involves a combination of concealed permissions, nested group membership and inherent security gaps in AD architecture. Let’s look at a couple of examples.
Example 1
First, suppose an attacker compromises the credentials for the account of the user Alex. That gives the attacker all the privileges assigned to Alex, whether through direct permission assignment, direct group membership or nested group membership. In this case, the Alex account is a member of the HelpDesk group, which is in turn a member of the Workstation Admins group, as illustrated here:
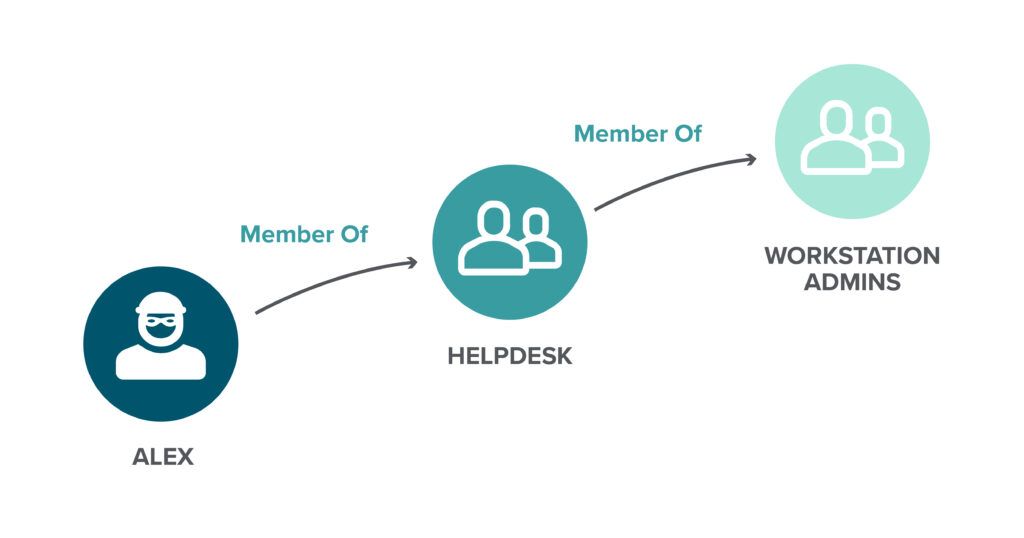
Such nesting of security groups is quite common, and it can give an ordinary user account more privileges than it should have — and far more that anyone realizes it has. In this case, the Workstation Admins group has local Administrator permissions for the PCI-Server-01 machine, which has a logon session from an AD service account, SVC_PRDRMV:
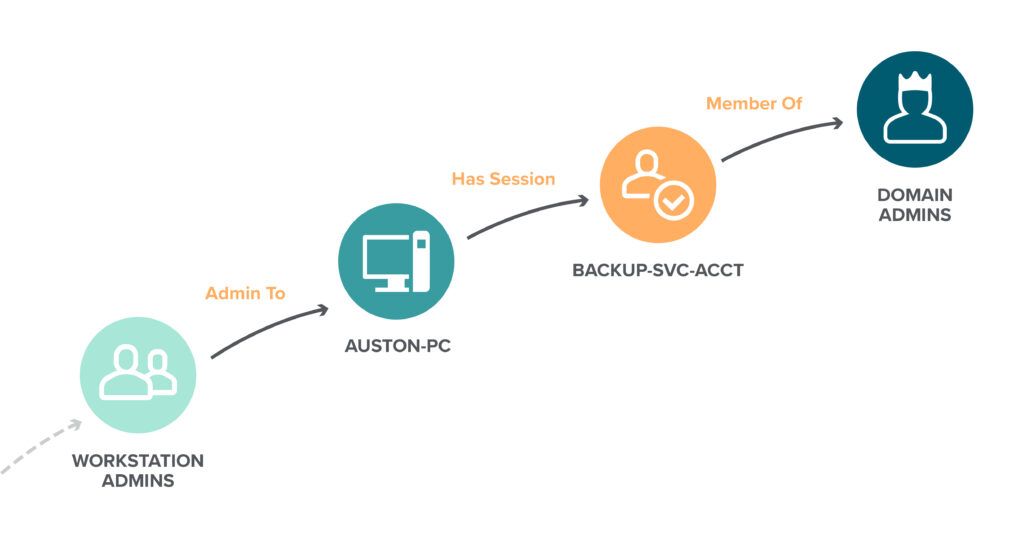
It’s trivial for the adversary to abuse the Windows token model and harvest the credentials of this service account — which gives them the Add Member permission over the Domain Admins group. Once they add their account to that group, the attacker has completed exploiting the attack path, and they now have full control over Active Directory.
Example 2
Additional examples are shared in the on-demand webcast How Insecure GPOs Create Real Attack Paths in AD. You should watch the webcast for a full explanation of how GPOs can play a role in attack paths, but here’s a brief description of one attack path: Consider a user account that was delegated permissions to edit a GPO. By compromising that user’s credentials, an attacker has an attack path to control of the AD domain. By modifying the GPO, they can cause another user account to execute a malicious PowerShell script the next time it logs on. The script will give the attacker control of that account — which has generic rights on the Domain Admins group. As a result, the attacker can add any account they like to Domain Admins, which is game over: They have control of Active Directory.
How to find and shut down attack paths: attack path management
Notice that there was no unpatched system or simple misconfiguration to be found in either of the examples above. Therefore, neither patch management nor vulnerability management could block the attack, and by the time a threat management solution spotted the attack, the adversary would be a Domain Admin.
For strong Active Directory security, attack path management is needed. Instead of looking at vulnerabilities or configuration errors in isolation, attack path management analyzes the relationships between objects in Active Directory and the complex permissions that are applied between them to identify the sequences of steps an adversary can take from compromising an ordinary user account to gaining control over critical assets or even Active Directory itself.
Of course, merely identifying attack paths is not enough; you also want to be able to remediate them to prevent adversaries from taking over your AD. But the reality is, in most organizations, there are thousands or even millions of attack paths. Blocking them one by one is simply not feasible. Instead, you need an attack path management tool that will identify the choke points that are shared by multiple attack paths. A choke point is the last segment in the chain of events for many attack paths. By remediating a choke point, you eliminate all the attack paths that rely on it.

Reduce your AD attack surface.
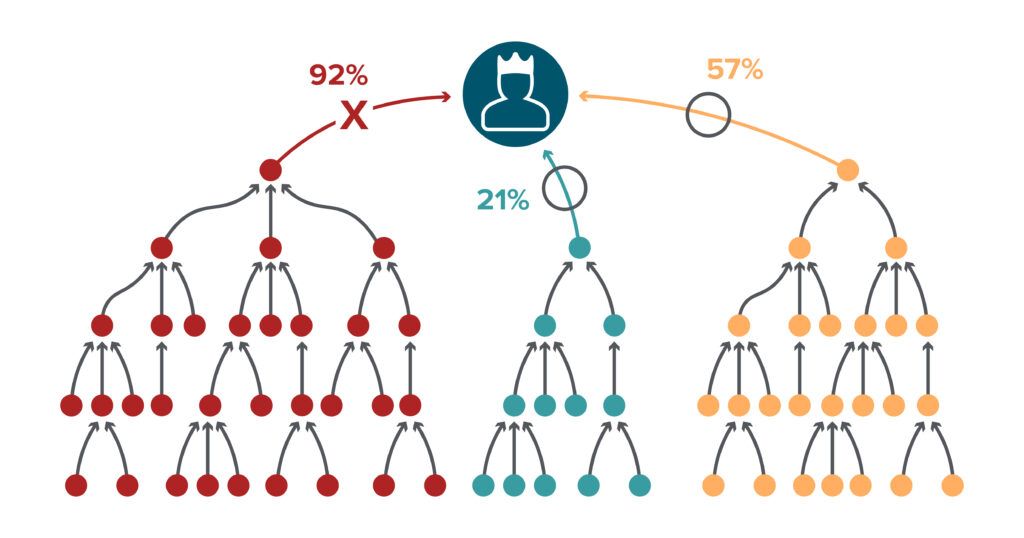
For example, suppose 92 percent of your user accounts could be used to abuse one particular attack path, 21 percent could serve as a possible starting point for another, and 57 percent could be used to launch a third one (the total is over 100 percent because any particular account could be the first step in multiple attack paths). By remediating the choke point for the first attack path, you eliminate the attack paths through all the user accounts below it, which can reduce your attack surface area dramatically.
Another vital component: attack path monitoring
While remediating choke points is the ideal solution to the attack path problem, doing so promptly is not always practical. The fact is, many organizations cannot quickly address all their choke points because there’s so much technical debt in their Active Directory. Relationships between objects in Active Directory and the permissions that are applied between them are so complex that making changes introduces the risk of breaking things, such as a critical application that relies on a particular permission.
Accordingly, it’s crucial to combine attack path identification with attack path monitoring — continuously watching to see if any attack paths are actually being leveraged so you can take action promptly instead of allowing the intruder the luxury of extended dwell time to advance along the attack path toward your critical IT assets. In particular, look for a real-time threat monitoring and change management solution that will:
- Monitor Active Directory in real time for active attacks and indicators of compromise (IOCs), such as AD database exfiltration attempts, Golden Ticket exploits and DCSync attacks.
- Block attackers from leveraging attack vectors by preventing changes and access to critical assets like privileged groups, GPOs and the NTDS.dit file.
- Audit security changes across your Active Directory and Azure AD environments.
Conclusion
It’s vital to remember that attack path management is not a “once and done” task. Modern computing environments are complex and highly dynamic, with continual changes to accounts, permissions, applications and GPOs. As a result, new attack paths are emerging all the time, so you need to actively look for them on a regular basis and promptly take steps to remediate or at least monitor them.



