The Active Directory forest is a critical — but often underappreciated — element of the IT infrastructure for many organizations. Let’s explore exactly what an Active Directory forest is and why having a solid Active Directory forest recovery strategy is vital for protecting your business.
What is an Active Directory forest?
As you may know, Active Directory (AD) is a database and set of services that help users get their work done in a Microsoft IT environment. The database (or directory) contains critical information about your environment, including what users and computers there are and who’s allowed to do what. The services control much of the activity that goes on; in particular, they make sure each person is who they claim to be (authentication) and allow them to access only the data they’re allowed to use (authorization).
Active Directory has three main tiers: domains, domain trees and forests:
- A domain is a group of users, computers and other Active Directory objects that share the same AD database, such as all the AD objects for your company’s Chicago office.
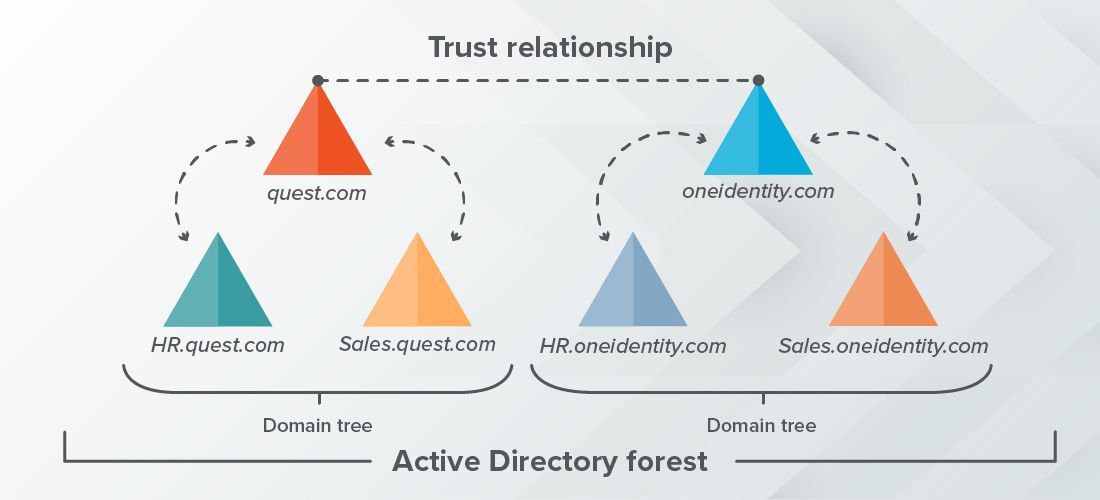
- A domain tree is a collection of one or multiple domains grouped together in a hierarchical parent-child structure with a contiguous namespace and transitive trust relationships between the domains. For example, the domains Quest.com and Sales.Quest.com would be considered part of the Quest.com domain tree.
- A forest is a group of multiple trees with shared directory schemas, catalogs, application information and domain configurations. The schema defines an object’s class and attributes in a forest, and the global catalog servers provide a listing of all the objects in an AD forest.
Beyond the structural differences, it’s important to understand the differences in purpose between an Active Directory domain and an Active Directory forest:
- The domain is a management boundary — The objects for a particular single domain are stored in a single Active Directory database and can be managed together.
- The forest is a security boundary — Objects in different Active Directory forests are not able to interact with each other unless the administrators of each forest create a trust between them.
How many forests are required?
Every Active Directory has at least one forest. Organizations can choose to have two or more Active Directory forests, or they might end up with multiple forests due to merger and acquisition (M&A) deals.
A single forest is the most cost-effective option, primarily because it requires the least amount of administrative overhead. It also enables maximum collaboration among users since all objects in the forest are listed in a single global catalog.
Multiple forests can be desirable or even necessary, depending on the data isolation and data autonomy requirements for the groups in your organization. However, having multiple forests does not in and of itself enhance security; you need to properly manage and secure each forest. Therefore, be sure to balance the costs of having multiple forests against the benefits. In particular, best practices require separate IT management teams for each forest to ensure proper segregation of duties.
Typically, only the largest and most complex organizations have multiple Active Directory forests. Most organizations create a single forest with multiple child domains, each of which has its own Active Directory database with its own resources, permissions, Group Policy objects (GPOs) and so on.
What are the forest design models?
There are three Active Directory forest design models: organizational, resource and restricted access. Large organizations may need to use a combination of models to meet the needs of their various business units or other groups.
Organizational forest model
Every Active Directory design includes at least one organizational forest. In this model, user accounts and resources are contained in the forest and managed independently.
The organization forest model is particularly valuable when you need service autonomy, service isolation or data isolation since the forest can be configured to deny access to anyone outside the forest. Still, trust relationships can be established between an organizational forest and other forests, which makes it possible for administrators in either forest to grant access to resources in the other forest.
Resource forest model
A resource forest, as its name implies, is devoted to resources; resource forests do not contain user accounts (other than those required for service administration and other specific purposes). Forest trusts are used to enable users from other forests to access the resources in a resource forest.
This model is no longer common, but it can be useful when service isolation is required to protect areas of the network that need to maintain a state of high availability, such manufacturing or other mission-critical resources.
Restricted access forest model
A restricted access forest is a separate forest that contains user accounts and data that must be isolated from the rest of the organization. Users have a separate account and a separate workstation for accessing data in a restricted access forest. No trusts exist, so users from other forests cannot be granted access to the restricted data.
This model is used in situations that require utmost security, such as classified government projects. For additional security, the restricted access forest can be on a separate physical network.
What is a Red Forest?
Red Forest is the common nickname for Microsoft’s Enhanced Security Administrative Environment (ESAE). Basically, ESAE is a layered security approach that involves creating a special administrative forest (called a Red Forest) to manage all privileged identities in Active Directory and better protect them against compromise.
The ESAE model promises valuable benefits, but it is not practical for most organizations because it requires an extremely complex and costly architecture, and the implementation process is cumbersome and can increase the risk of downtime.
Microsoft is retiring the Red Forest model for most scenarios in favor of a modern Enterprise Access model, which incorporates a cloud-based privileged access strategy that offers the same or better security and which can be implemented using Microsoft’s rapid modernization plan (RAMP).
Active Directory forest best practices
Strategies for designing, managing, and securing your Active Directory forests could easily be multiple separate blog posts. But here are some of the top best practices:
- If possible, use just one forest. This approach simplifies management tasks while reducing costs and complexity.
- If you have multiple forests, pay particular attention to the trusts you establish between them.
- Following Microsoft guidance for selecting the root domain of your Active Directory forest. The forest root domain contains the Enterprise Admins and Schema Admins groups, which are used to manage critical forest-level operations such as adding and removing domains and changing the schema.
- Set the domain and forest functional levels to the highest values that your environment can support (by default, they are both set to Windows Server 2012 since Windows Server 2008 reached its end of support in 2020). Functional levels determine the available Active Directory Domain Services (AD DS) capabilities, as well as which Windows Server operating systems you can run on domain controllers in the domain or forest. Note that the functional level cannot be downgraded, but it can be raised.
- For high availability in distributed environments, configure all domain controllers to provide DNS and global catalog services.
Creating an Active Directory forest recovery plan
One final best practice merits fuller discussion. As we have seen, your Active Directory forest is a dynamic, complex, and sophisticated ecosystem that provides vital authentication and authorization services for your organization. Indeed, a healthy, functioning forest is essential for just about any core business process today.

Accelerate Active Directory recovery
At the same time, your Active Directory forest is also a top target of cyberattacks and is vulnerable to natural disasters, failures, and human mistakes. For example, a ransomware attack can bring down your Active Directory forest in minutes or even seconds. And the longer your Active Directory remains down, the longer your business is down. Indeed, every second counts: 40% of enterprises say that a single hour of downtime costs $1 million to over $5 million, and in worst-case scenarios, losses can reach millions of dollars per minute.
The best way to minimize this downtime — and the inevitable damage to your business — is to have a comprehensive Active Directory forest recovery strategy backed by the right tools. Native approaches are not enough. Indeed, when performed manually with Microsoft tools, AD forest recovery is a difficult, time-consuming, and error-prone process. Microsoft’s Active Directory Forest Recovery Guide outlines 18 high-level steps (each comprising myriad sub-steps) that must be performed correctly and in the proper sequence — on each DC and coordinated across all DCs you restore from backup. Moreover, many of the steps aren’t operations that AD administrators are familiar with; they are tedious, often command-line-based actions, so it’s very easy to make mistakes that can re-corrupt your directory and require you to start over.
Therefore, it’s a best practice to look for a backup and recovery solution that offers all the following:
- Reliable AD backups that make the process more efficient and minimize the places where malware can hide
- Phased recovery to enable you to get the business back on its feet quickly
- Flexible restore options, including not just phased recovery but also restoring to a clean OS and bare metal recovery (BMR)
- Clean OS recovery to the cloud so you can quickly recover AD to a readily available, secure and cost-effective virtual machine that you create on the spot
- Malware detection that regularly checks files for viruses after the backup file is created, during storage when updates are added and before a restore is started with integrated Microsoft’s Defender capabilities
- Secure storage — a hardened server that is isolated according to IPSec rules with regular checks to confirm backup integrity
- Operating system recovery to quickly restore a domain controller’s operating system without depending on other DCs
- A virtual test lab where you can demonstrate and validate your Active Directory disaster recovery plan with production data
- Hybrid recovery that restores cloud-only objects and properties like Azure AD groups, Azure B2B and B2C accounts, and Conditional Access policies
Conclusion
Active Directory provides the vital authentication and authorization services required to keep your business running and your data and systems secure. By following the best practices detailed here, you can establish and maintain an effective Active Directory forest structure. Still, no organization is immune to cyberattacks, mistakes and disasters that can take down their entire forest, so it’s also crucial to create a comprehensive forest recovery plan, thoroughly test it, and practice it on a regular basis.



