Endpoint security risks affect all endpoints, from laptops and tablets to smart speakers and wearables. Even network connected printers can pose an endpoint security risk to your organization.
The variety of endpoint devices has increased with the rise in flexible work arrangements. Work-from-home options have become the norm and organizations rely more on software tools for collaboration with external partners. However, endpoints have also become a prime target for cybercriminals due to their vulnerabilities. Endpoint security risks have risen fast on the list of items that IT teams must monitor and mitigate.
This post explores the most common types of endpoint security risks and how you can keep them under control in your organization.
What are endpoint security risks?
In the past, endpoint security was relatively straightforward. Companies would build a secure network perimeter, issue and track devices and maintain a patching program to ensure they were up to date. But organizations deal now with an explosion of connected devices—company issued or employee personal devices—which comes with its own unique security risks.
On top of device proliferation, IT environments are now constantly under attack. Hundreds of thousands of new malware variants are discovered each day – far more than even the largest human team could ever monitor and neutralize.
IoT and BYOD devices grow ever more pervasive, creating even more complexity for IT teams. The transition to a remote work model has further complicated the situation, making it difficult to protect endpoints from threats. The result is an IT landscape in which almost every technology advantage of an endpoint is matched or outmatched by attendant security risk.
The importance of endpoint security
Because any device linked to your business could be an avenue of attack, your organization faces widespread endpoint security challenges. The overall security imperative is to identify and protect any device that has access to your system, regardless of where the device is located.
As remote work has gained popularity employees are no longer limited to using desktop computers in the corporate office. Endpoint security is a must-have for devices like cell phones, tablets and even smartwatches, with their potential to access to sensitive company information.
Printers, fax machines, point-of-sale systems and IoT devices also have access to your network, which translates into more potential points of entry for hackers. The following is a list of common endpoint security risks facing almost every organization.
1. Phishing
Phishing is a method of hacking wherein malicious actors send out email messages that appear to be from trustworthy sources, like people or organizations the recipient knows. The goal is to trick unknowing recipients into downloading viruses or other malicious content.
Phishing is enormously popular as a technique because it is enormously successful. It plays to the natural curiosity of every user and, if the email message succeeds in landing in a target’s — any target’s — inbox, it has a chance of succeeding.
The most common best practices are security training, email filtering and antivirus software, and no organization with users connected to company networks and resources should be without those. Unified endpoint management (UEM) can add an extra level of security through insight into and control over all endpoints the network.
2. Inadequate patch management
Of course, patching per se is not an endpoint security risk. But if you fail to manage patching and updates, you’re going to introduce huge risks. Patch management is essential to help prevent compromised devices, yet many organizations lack a formal patching process.
Keeping your endpoints updated is how you address the vulnerabilities that can leave you with infected devices. It used to be relatively easy to push out monthly updates to computers connected to the corporate network using Group Policy. However, with so many more endpoints to manage, and with an ever-growing share of devices not connecting directly to the network, the process is no longer so easy.
With the prevalence of remote and hybrid work models, it is more difficult to keep up with the various types of hardware, software, operating systems and mobile devices in use. It’s also harder to count on users being connected to the corporate network regularly to receive necessary updates, especially without a well-defined patching process.
3. Loss and theft: Devices
It’s a sad fact of life that mobile devices go missing. They’re small, powerful and valuable, so whether users are lamenting the loss of a device or thieves are enjoying the quick profit, it’s a big deal.
Each year, millions of smartphones are stolen or go missing, with only a small percentage recovered. Whether the company or the user owns the device, if it has ever contained any company data, the risk of misuse can be high. There is, of course, the cost of the device itself to consider, but also the value of any information stored on it that could be accessed by any malicious user who can bypass the PIN. That includes unencrypted texts and email.
4. Loss and theft: Data
As the costs and risks of data breaches continue to climb, endpoints are often the source of these attacks. Consequently, it is important to ensure that users have access to only the business systems and information that are pertinent to their job duties. To lower the risk of potential data loss, users should be provided with least-privilege access to necessary systems and administrator privileges should be reserved for those with special authority. Taking these steps will not only protect your business but also help maintain your brand and reputation in the event of a data breach.
5. Software vulnerability exploits and outdated patches
Software vulnerability exploits may not be as common as phishing attacks, but the harm they cause can be just as serious. Improper configuration, outdated software and inconsistent patching are all major sources of flaws that hackers may try to take advantage of. Organizations typically take 97 days to fully install updates, making software vulnerability exploitation one of the top means of ransomware attack.
Attackers usually have two strategies for exploiting unpatched software security flaws. In the first strategy, they have prior knowledge of the vulnerability and use a scanning tool to search for environments operating with that vulnerability. In the second, they choose an organization, scan its network for any security vulnerabilities and then find a way to exploit them. Either way, once hackers gain access, they look for ways to spread ransomware around the environment as far as possible.
A high-profile example of an exploited software vulnerability is CVE-2021-43035, the Kaseya software hack. Two unauthenticated SQL injection vulnerabilities allowed the execution of arbitrary SQL queries under the superuser account in Postgres. Attackers could execute code remotely, resulting in full access to the Postgres user account. More than 1,500 organizations were affected by the exploit, often through their managed service provider (MSP).
6. Malware ads
Also known as malvertising, malware ads are like adware in that they rely on online ads to do most of their damage. The difference is that a malware ad usually comes from a compromised ad on a legitimate website. The company that owns the site is likely to find the malware ad only if they use some sort of endpoint scanning.
The industry recommendation, of course, is to not click on or interact with anything you don’t recognize. But some malware ads capture user information entered on the page, without any suspicious interaction at all. These are the three main ways your organization can prevent infection from malware ads:
- Use and update antivirus software on your endpoints, whether it’s the one that ships with the operating system or a program licensed separately.
- Configure the browser to disable Auto-play and enable Click to Play. That keeps content like ads and video from playing without the user’s consent.
- Use an ad-blocking extension to minimize users’ exposure to ads, both legitimate and malicious. Ad blockers affect the user experience in other ways, too, so some users may complain that certain websites don’t function properly because of ad blocking.
7. Drive-by downloads
Drive-by downloads introduce endpoint security risks by installing essentially a wolf in sheep’s clothing. One example is for a threat actor to introduce malware to a patch or update that goes out as a trusted download to thousands or millions of users. The nefarious thing about a drive-by download is that a vast population relies on trusted software to maintain their systems and protect them from just such exploits.
Industry voices often call for enforcing strong passwords, and for ensuring that users aren’t local administrators on their own systems. But it’s even more important to adopt a layer of protection at both the endpoint and the network gateway.
To keep the drive-by download itself from taking advantage of a vulnerability, your software vendor must ensure that the delivery service is maintained and secured properly. That extends to audits and evaluations of the systems, and to reporting on alerts and notifications about unauthorized activity on release servers. The goal is to establish an inventory of hardware, software, services and components against which to compare each newly installed update.
8. RDP compromises
In Remote Desktop Protocol (RDP) compromises, hackers use penetration testing software to scan for open ports in RDP intrusions. After identifying the open ports, the attackers then attempt to compromise the systems by using brute-force password hacks. In September 2020, Universal Healthcare Services with its 400 care sites suffered a Ryuk ransomware attack after a successful brute-force attack on RDP. This attack led to a hefty recovery cost of $67 million and three weeks of downtime for their Electronic Healthcare Record system.
9. Distributed denial of service (DDos) attacks
A DDoS is a digital traffic jam, in which users’ requests are trying to merge into traffic, but the roads are too congested. Millions of compromised computers are instructed to send requests to a given website at a given time, and that site will buckle under the load. DDoS attacks can also be launched against a specific device or a network segment, dealing a heavy blow both financially and operationally.
DDoS attacks are more common than most users realize. Something as innocent as an interruption in Wi-Fi can in fact be a threat actor trying to gain access to a home network. Non-malicious DDoS often happens in the minutes after tickets go on sale for certain concerts and athletic events, or when breaking news compels users to flock to a particular website. On the malicious side, consider a DDoS attack against a military operation in a conflict zone. Think about the damage an enemy can inflict when troops in the field can’t use their computers to communicate with one another or with commanders.
It’s difficult to respond to a DDoS attack because first you have to determine what’s happening, and then reroute the traffic away from the interruption. Following the road analogy, can you send the traffic ten miles down the road to merge? Can you send it in the other direction? It’s an exercise in modifying IP addresses and blocking the onramps that the attackers are using. That’s hard when they’re masking their source by coming from millions of places at once.
In all cases of recovering from a DDoS attack, there are four main stages: find the jam, figure out how to get around it, implement that remedy, and adapt to keep up with the attacker. Security is a constant game of cat and mouse.
10. Botnet attacks
Botnet attacks come from bots running on large numbers of compromised endpoints that have been linked together. They run a routine that executes a task like a DDoS attack, or an infection of yet more endpoints. Once the population of compromised endpoints reaches critical mass, the threat actor directs a concerted attack at a high-value target.
Again, some such attacks have non-malicious origins, as in the case of crypto mining for digital currencies, or grid computing for sharing unused compute power. But most of the time, miscreants are commanding and controlling zombie devices, inducting them to a vast botnet army. Common attack scenarios include DDoS, phishing and taking over online accounts.
You may not be able to prevent a botnet attack from happening, but you can prevent yourself from being a part of it. The defensive strategy is to address the malware infection in the first place by enforcing protection on the perimeter and endpoints and keeping patches updated. Attackers can always find plenty of unsecured endpoints, so they go after the easiest targets first, as a way of eventually going after bigger ones.
11. Macro and script attacks
Macro attacks, often called script attacks, perform the same task over and over again. Macros can be embedded in innocent-looking files like PDFs, spreadsheets or word-processing documents. They’re easily hidden and, like all software, they can be benign, or they can be used for malicious ends.
Application policies are an effective strategy for reducing the endpoint security risk from macro and script attacks. Endpoint management tools allow you to set and enforce policies at the endpoint. Then, when users try to launch a macro, the local operating system prohibits it from running; the data in the document remains accessible, but the scripted functions are blocked.
The downside, of course, is that the legitimate macros don’t work either, but the trade-off between convenience and security is necessary. Macro attacks rely on human intervention: users need to click something or open a file. Their distribution and execution depend on human vulnerability, which is infinite. Antimalware goes only so far, and defending against macro and script attacks comes down to education and vigilance. Endpoint security risk and vectors are constantly changing, and IT can reasonably expect only so much of users.
It’s always good advice to change passwords often, keep things close to the vest and avoid clicking on dodgy links and attachments. But it’s not fair for IT departments to rely heavily on users, because users are meant to be the last line of defense, not the first.
12. Access controls
Having too many individuals and systems with access to confidential corporate information can heighten endpoint security risk. It is important that users have access to only the systems required for them to complete their tasks when and where necessary. However, administrators often don’t know who is accessing which systems due to a lack of insight into endpoints. The lack of knowledge about user access makes it hard to prevent unapproved users from accessing sensitive data, with the attendant risk of infecting the data with malware.
13. Application control
With application control you can allow or block specific applications from running on endpoints. Allowing only secure, trusted, business-oriented applications and blocking spurious, non-essential applications is the best way to establish a safe environment. Smart IT teams enforce an allow/block dichotomy and deal with other applications as they arise.
It’s a fact of business life that the software landscape constantly changes, and new titles continually emerge. Some IT professionals address that by erring on the side of caution and blocking unknown applications, while others allow everything until it’s been proven bad. Neither approach is necessarily right or wrong; both reflect different mentalities.
Other classification criteria include the purpose for or use case of the application, its priority, the traffic it generates, the risk levels or the overall usage. Some applications belong in a particular department but not in others; for example, you would expect Adobe Photoshop to be able to run in Marketing, but not in Finance. Once you settle on categories, organizations will set standards for allowing and blocking applications.
14. Legacy and proprietary systems
Systems that can no longer be patched or upgraded introduce endpoint security risks. But if they’re considered essential, then those risks become a cost of doing business.
Especially in established businesses, certain older business applications can obstruct progress towards digital transformation. These outdated applications run on hardware such as mainframes and use programming languages like FORTRAN and COBOL, which are not light or modular in nature. Additionally, they are not compatible with modern databases or built for open APIs that allow access to other applications. Furthermore, they have been around since long before the age of cloud computing. When evaluating the advantages and disadvantages of legacy application modernization for your organization, focus on how it will help the business progress. Metrics to consider include higher customer satisfaction levels, decreased maintenance costs, greater scalability and more agility.
15. IT skills and knowledge
Finally, the human factor within IT introduces endpoint security risk. Gartner reports that nearly two-thirds of IT executives consider talent shortages the most significant barrier to adoption of emerging technologies. That dearth of talent extends to endpoint security.
The industry is still emerging from two big aftershocks of the pandemic. During the Great Resignation, employees throughout organizations began re-examining ideas about their careers, their work-life balance and their longevity. The effects in IT were felt in the loss of admins qualified to manage platforms like Active Directory and of cloud-savvy IT pros qualified to manage Microsoft 365.
Then, during the Great Resistance, employees pushed back on organizations that wanted to hire or retain them. They wanted more flexibility and autonomy in work and lifestyle, along with higher pay and benefits. They were more inclined to change jobs or careers to adjust for work-life balance.
The combination of those factors has prompted organizations to invest in the cloud and in automated solutions designed to ease the burden of IT management.
Conclusion
The variety of endpoint security risks amounts to a storm of IT worries: viruses, ransomware, botnets, rootkits, malvertising, adware and more. It’s impossible to keep up with so many different outsider and insider threats.
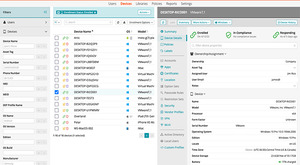
Patch, secure, and manage every endpoint.
Worse yet, all it takes is one person getting lucky one time. That person doesn’t need to be especially clever or talented; just lucky one time. IT, on the other hand, has to implement endpoint security right every time, all day, every day, to stay ahead of attacks.
The groups behind these attacks are well-funded and well-organized. They may be backed by criminals or governments. In the Bring Your Own Device (BYOD) era, when corporate endpoints are on home networks, the network perimeter is a thing of the past. Compromised devices on the home networks of remote users can compromise other devices or other software services.
So, IT professionals rest on a few standby principles for network defense:
- Zero trust
- Identity and access management (IAM)
- Single sign-on with authenticated providers
- Endpoint patching
- Endpoint encryption
- Least-privilege access
- Device configuration maintenance
- Enforcement of settings and security protocols
Will all of those measures affect application performance and affect user convenience? Almost certainly. But nobody wants to risk going out of business because the boss wouldn’t tolerate a slow computer. Mitigating endpoint security risks is an exercise in striking the trade-offs with users to get them to do what makes sense for the business. However at the end of the day, if you’re not keeping your endpoints up to date because it’s inconvenient or difficult, then you’ve already lost the battle.