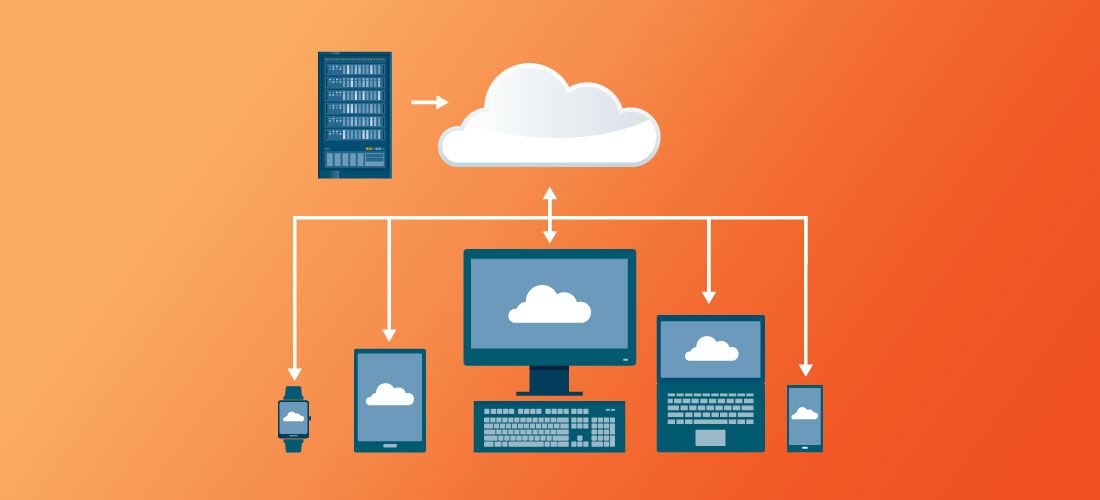
Endpoints are always the entry point for data breaches. Given the impact a breach can have on your organization, applying endpoint security best practices is of paramount importance. The risks to your organization are growing higher every year. According to the Identity Theft Resource Center (ITRC), the number of data breaches grew by 17% in 2021 versus 2020 with 1,291 breaches through the first three quarters of the year.
And the average cost of a data breach is escalating as well. Based on research from IBM and the Ponemon Institute, the average cost of a data breach reached $4.24 million USD in 2021, the highest it has been in the last 17 years. They also found that the average cost was $1.07 million USD higher in breaches where remote work was a factor in causing the breach, which shows just how vulnerable endpoints can be to cybersecurity threats with our current remote and hybrid working models in place.
What is endpoint security?
Endpoint security is the process of identifying and protecting every device that accesses your network, because any device is a potential attack vector. This approach moves away from the traditional model of endpoint security, which focuses on placing all computers and servers within a protected perimeter—typically a firewall—and managing everything within that contained space. The perimeter has expanded to include every endpoint that accesses your network and data, regardless of its location.
The importance of endpoint security
Organizations are facing many endpoint security challenges as every device connected to your business could be a possible attack vector. Therefore, identifying and safeguarding every device that accesses your network, regardless of where they are is critical.
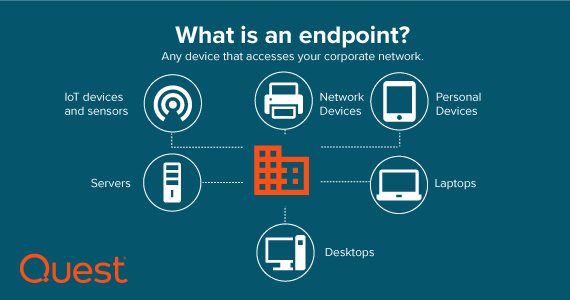
Employees are no longer relying on just their desktop PCs at the office. The explosion of remote work in the last few years has increased the use of laptops, iPads, iPhones, smartwatches, you name it, to access essential company information 24 hours a day, seven days a week – hopefully encrypted – from wherever and whenever they want to work. It’s also not confined to user devices. Printers, fax machines, point-of-sale systems, and an ever-growing list of Internet of Things (IoT) devices now accessing your network are all examples of endpoints and possible areas of entry for bad actors. That’s where policies and processes come in to play. In this blog you will find a list of endpoint security best practices that your organization can implement to increase protection.
Common endpoint security risks
1. Phishing
Phishing is a hacking technique in which malicious individuals send deceptive emails that appear to be from trusted sources, like known individuals or organizations, with the goal of tricking recipients into downloading viruses or harmful content.
This technique is extremely popular due to its high success rate, exploiting the inherent curiosity of users. If the phishing email reaches any recipient’s inbox, it stands a chance of achieving its nefarious goals.
To counter phishing attacks, essential best practices include security training, email filtering, and antivirus software. Any organization with users connected to their company networks should prioritize implementing these measures. Additionally, Unified Endpoint Management (UEM) offers an extra layer of security by providing insights into and control over all network endpoints.
2. Inadequate patch management
Patching itself is not a security risk for endpoints, but failing to manage patching and updates can lead to significant risks. Proper patch management is crucial to prevent compromised devices, yet many organizations lack a formal patching process.
Ensuring that your endpoints are updated is essential to address vulnerabilities that could result in infected devices. In the past, pushing monthly updates to computers on the corporate network was relatively straightforward using Group Policy. However, as the number of endpoints to manage has increased, and with a growing number of devices not directly connected to the network, the process has become more challenging.
With the rise of remote and hybrid work models, keeping track of various types of hardware, software, operating systems, and mobile devices in use has become more difficult. Additionally, relying on users to be regularly connected to the corporate network for necessary updates is no longer a reliable approach, especially in the absence of a well-defined patching process.
3. Loss and theft: Devices
It’s a sad fact of life that mobile devices go missing. They’re small, powerful and valuable, so whether users are lamenting the loss of a device or thieves are enjoying the quick profit, it’s a big deal.
Every year, millions of smartphones are reported stolen or lost, and only a small percentage of them are recovered. Whether the device belongs to the company or the user, if it has ever contained any company data, there is a considerable risk of misuse. Apart from the cost of the device itself, there’s also the concern about the value of any information stored on it that could be accessed by malicious users who can bypass the PIN. This includes unencrypted texts and emails.
4. Software vulnerability exploits and outdated patches
Software vulnerability exploits might not be as common as phishing attacks, but their potential harm can be just as severe. Flaws arising from improper configuration, outdated software, and inconsistent patching are prime targets for hackers seeking to take advantage of them. Surprisingly, organizations typically take around 97 days to fully install updates, making software vulnerability exploitation one of the leading methods for ransomware attacks.
Attackers generally pursue two strategies to exploit unpatched software security flaws. In the first approach, they possess prior knowledge of the vulnerability and employ scanning tools to identify environments susceptible to it. In the second approach, they select a target organization, scan its network for security vulnerabilities, and then exploit them. Once they gain access, hackers strive to spread ransomware throughout the environment as extensively as possible.
Applying 7 endpoint security best practices
The good news is that safeguarding your endpoints with a well-thought-out strategy isn’t difficult. A lot of it boils down to some essential IT practices. The idea is to automate as much as possible to stay ahead of it. Below are seven fundamental endpoint security best practices every organization should follow.
1. Educate your users
Proper endpoint security starts with educating the users of the endpoints that access your network and data. You can make your IT and endpoint environment as safe and strong as possible, but if a user reads an email and clicks on an attachment they shouldn’t have opened and clicked, it can create an opening in your perimeter for hackers to attack your company.
Making sure your organization provides security and compliance training to your users and confirming that they finish it successfully on a regular basis is a critical but partial answer. Another action the IT or security staff should do is send out alerts to users whenever a questionable email is circulated, with advice on how to properly delete or quarantine it.
2. Find and track all devices that connect to your network
Regardless of platform, operating system, or location, you must be aware of and able to track and monitor every device that connects to your network. This includes company-owned computers, printers, and IoT devices, as well as laptops, tablets, and phones used by your employees as part of your BYOD program.
Go beyond making sure that unauthorized individuals do not gain access to any of these devices and also determine what is not meant to be accessing your network, such as who has more access permissions than they require, and which devices have become infected. Even if you don’t have a unified endpoint management system in place and are forced to manage several, disparate management systems, this degree of visibility and control is critical to guaranteeing the security of your endpoints.
3. Install and maintain the latest operating systems, security software and patches
After gaining visibility into every device connecting to your network, now you need to identify the endpoints that require updates and patches made to the operating systems, applications, and security software they have installed or need to have installed.
Having the most up-to-date security software installed on all your devices will aid in the blocking and removal of malware from your endpoints. In addition to the security software, the makers of the operating systems and apps your company relies on regularly invest a pretty penny to patch vulnerabilities in their software, but those updates and patches are only effective if your endpoints are kept up-to-date on a regular basis.
4. Employ a zero trust security approach to user privileges
A zero trust security approach to user privileges aims to prohibit unauthorized users from accessing sensitive data and from spreading malware that could infect it. As referenced above, this approach is proven to be effective for significantly lowering the cost of a data breach at organizations with a mature zero trust approach.
Administrators must keep track of which systems the users access from their endpoints and whether the access rights granted to each user are acceptable for their role. Users should only have access to business systems and data that they require to perform their duties. Users should have least-privilege access to the systems they need by default, with administrator privileges reserved for specialized users.
Patch, secure, and manage every endpoint
5. Regulate USB port access
Unattended workstation USB ports, as well as devices such as printers, cameras, and external drives, could be used to steal company data or introduce malware into the network. Administrators should use a least-privilege strategy to granularly limit who has access to which USB ports and where in order to prevent malware, avoid data theft, and maintain your zero trust security standards.
6. Discover and fix vulnerabilities
You must identify software versions, settings, or device configurations that may expose your system to vulnerabilities. Conduct frequent IT security audits by scanning all Windows, Mac, and Linux systems with the Open Vulnerability Assessment Language (OVAL). This will enable you to identify and fix vulnerabilities in your environment as well as systems that do not adhere to your security and configuration policies.
7. Rapidly remediate missing and infected devices
Track and monitor your traditional and mobile devices at all times. Remotely lock, wipe, or factory reset a mobile device or its password if it goes missing to prevent company data from being accessed, corrupted, or stolen. If you believe an endpoint has been infected with malware, reimage the device immediately using a gold master image.

Summary
The risks and costs of data breaches are rising, and endpoints are frequently the entry point for these attacks. Having a fundamentally sound approach to endpoint security is essential to protecting your organization from cybercriminals and it can be implemented by following these seven endpoint security best practices.