Endpoint security used to be fairly easy. You enclosed all your desktops in a secured network perimeter and were confident that your domains were secure. IT kept an inventory of all organization-owned devices and kept them patched. Today, organizations are managing an ever-increasing number and types of connected devices – amid ever-increasing endpoint security challenges and risks.
IT environments are now constantly under attack, with upwards of 360,000 new malware variants discovered each day. As endpoints continue to grow in volume and diversity, managing and securing them becomes more complex and time consuming.
The increase of IoT and BYOD devices is expected to continue, and shows no sign of slowing anytime soon. Add in the shift toward remote work and the risks that presents, it’s clear that companies are facing serious endpoint security challenges.
Endpoint security has become a major undertaking
But understanding what you’re up against can help. So, let’s explore the most prevalent endpoint security challenges organizations are facing today.
1. Tracking all network-connected devices
Device proliferation increases overall endpoint security risks. The number of network-connected devices is skyrocketing. Beyond just needing to properly track and secure corporate-owned devices, companies also need to secure personal devices accessing company resources under BYOD programs.
This makes it extremely difficult to secure an enterprise, as administrators struggle to implement appropriate access controls to corporate resources. Among companies that have suffered a breach related to BYOD, the majority were required to conduct an audit. If an audit by a regulatory agency reveals a business doesn’t have proper security controls in place, the company may have to pay costly fines.
As the number of devices grows, tracking and securing them gets harder, especially in a BYOD environment.
Physical security of corporate devices and BYOD
Tracking and managing both traditional and mobile devices is critical for endpoint security, but it’s also difficult. Regardless of platform, operating system or location, you must be aware of and able to monitor every device that connects to your environment. This includes company-owned computers, printers and IoT devices, as well as personal laptops, tablets and phones used by employees as part of BYOD programs.
Proper access permissions should help limit the amount of damage an unauthorized individual can do if a device is compromised. On top of that, determining what unusual behavior looks like on devices accessing your network and identifying if other devices have become infected is crucial for endpoint security.
If a mobile device goes physically missing, you must be able to remotely lock, wipe or factory reset it to prevent company data from being accessed, corrupted or stolen. If an endpoint has been infected with malware, you may have to reimage the device immediately..
Even if you don’t have a unified endpoint management system in place and are forced to manage several, disparate management systems, this degree of visibility and control is critical to guaranteeing the security of your endpoints.
2. Mitigating the endpoint security risks of a remote workforce
The massive shift toward remote work has further complicated endpoint security. You’re now confronted with endless questions related to endpoint security risks. How safe are the homes of your remote employees? What are they downloading? Are they using their work computer to access malicious sites? Are they using personal devices to access sensitive company information? Are they patched? Are they in an apartment building broadcasting their WiFi SSIDs and using old security protocols? Is their router username “admin” and is their password easy to guess? Are you able to handle having every employee on your VPN?
This increasing transition to remote work puts a tremendous amount of stress on admins. Additionally, this transition has greatly increased attack vectors, and the bad guys will take advantage of the lack of control caused by this big flood of unknown devices hitting IT environments from pretty much anywhere. It’s not so much adding new problems, but compounding existing known problems. Admins with good IT security practices will have less exposure to endpoint security risks. By automating vulnerability assessments and patching, it’s possible to stay ahead of things. Which brings us to our next endpoint security challenge.
3. Managing updates and patching
Endpoint updates are necessary to address vulnerabilities that can lead to infected devices. But device proliferation has complicated this. And as critical as patching is, organizations often fail to formalize patch management, leading to serious consequences.
Patching
Patching was once straightforward. You could push out updates monthly with Group Policy to desktops and laptops that were connected to the corporate network. That has changed significantly. While patch management is critical for reducing organizational risk, it has become increasingly complex.
Today’s workforce has shifted many employees to remote or hybrid work models, and adopted a diverse range of hardware, software, operating systems and mobile devices. Users might not even connect directly to the corporate network often. This creates a problem for those responsible for keeping devices up to date before attackers can exploit unpatched software.
4. Controlling user access
Giving access to too many users and systems with sensitive corporate data can lead to security breaches. Users should get access to only the systems they need to do their work when and where they need it. However, administrators often can’t even keep track of who’s accessing what because they lack visibility into all endpoints. This lack of visibility into user access makes it difficult to prevent unauthorized users from accessing sensitive data and possibly spreading malware that could infect that data.
5. Ensuring regulatory compliance
Regulatory compliance is unavoidable in business and keeping up with new and changing laws can be difficult. But knowing the laws, understanding their requirements, and ensuring they are met is necessary. Each law has different mandates and goals, but most require limiting user access and local admin privileges to prevent non-compliance and security risks.
Organizations must frequently reevaluate and update their compliance strategies or risk regulatory fines, legal action, security breaches and the loss of trust of partners and customers. Anyone affected by a breach, including customers and partners, may sue. And class action suits are becoming more and more common.
6. Preventing data loss
The risks and costs of data breaches are rising, and endpoints are frequently the entry point for these attacks. Users should only have access to business systems and data that they require to perform their duties. Users should have least-privilege access to the systems they need by default, with administrator privileges reserved for specialized users. Ensuring users have proper access will help reduce the risk of data loss. Data breaches can badly damage your brand and reputation.
7. Securing USB ports
When it comes to configuring, managing and securing unique user workspaces, securing USB ports is another endpoint security challenge.
To ensure that malware does not infiltrate a corporate network, you must lock down USB ports. Unsecured workstation USB ports could be used to steal company data or introduce malware into the network.
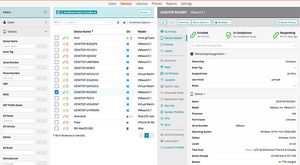
Patch, secure, and manage every endpoint
Administrators should use a least-privilege strategy to granularly limit who has access to which USB ports and where to prevent malware, avoid data theft and maintain zero trust security standards.
It’s important to remember that endpoints also include printers, cameras, external drives and other devices that have USB ports in various locations. Left unattended, any of the USB ports in these devices could be exploited to introduce malware into an IT environment.
Summary
With so many devices tapping into corporate networks from so many locations, endpoint security challenges have become common. But so have cyberattacks, making it more critical than ever that you find ways to reduce endpoint security risks.
While managing and securing an ever-increasing range of devices amid ever-increasing outsider and insider threats, can get overwhelming, you can take control. Implementing best practices for endpoint security will help keep your network safe.