Bring Your Own Device (BYOD) security risks arise from the give-and-take between employees who want maximum productivity and IT administrators who need to establish and enforce control over the devices that access network resources. The various risks are further complicated as enterprise computing evolves from the model of working inside the corporate security perimeter to working from home and working remotely.
From the perspective of IT system administrators and decision makers, BYOD policies should be carefully thought through, and all security risks, challenges and best practices of BYOD endpoint management should be considered.
What exactly is BYOD?
BYOD refers to Bring Your Own Device. It describes a company policy of allowing employees to use their personal devices, such as smartphones, tablets and computers, for work purposes. With BYOD, employees access business-related systems, applications and data on software and hardware that the employee owns and the company does not manage.
Why is BYOD coming to the forefront of endpoint security?
As more employees work from home, the trend toward performing work on personally owned devices has grown. For many workers, the option of conducting personal and professional business on the same device amounts to a boost in productivity.
However, most workers don’t realize the BYOD security risks involved with using their own devices. Permitting unmanaged devices to access corporate information opens more potential attack vectors to the business — attack vectors that IT teams need to manage. Even long before IT was aware of the risks, many employees embraced the use of personal devices — whether approved by IT or not — for work purposes.
BYOD security risks faced by organizations
Those risks include the following:
Unsecure networks
The traditional network perimeter is dissolving. Endpoints (devices) access corporate data from both inside and outside the corporate firewall. That means it is unwise to assume the same level of protection and security as in years past. The realistic model is to assume “zero trust” and that no network is secure.
No entity’s attempt to access company information should be blindly trusted. Secure authentication is paramount.
Device loss or theft
Data from Kensington shows that 70 million smartphones are lost or stolen each year, with a typical recovery rate of about seven percent. Whether those devices are company-managed or not, each one represents a potential data breach if it has ever accessed or stored corporate information. Therefore, the risk extends far beyond the replacement value of the device, to the value of whatever information or data is on the device. After getting past the PIN, a bad actor would likely have easy access to any stored and unprotected text and email messages.
Malicious apps
Only 40 percent of organizations restrict their users to installing apps from recognized app stores (e.g., App Store, Google Play), according to a report by Verizon. The less reputable the source, the more likely that the app contains malicious code. Many organizations are simply unaware of the sources from which employees download apps to their devices.
Legal problems and damage to reputation
In an era of data breaches and privacy regulations, the refrain in most boardrooms is “Let’s just stay out of the news.” BYOD security risks lead to the kind of business interruption that, unfortunately, puts a company in the news, resulting in vastly higher costs than reimbursement for a lost device. IBM reports that the average cost of a data breach exceeds $4 million USD, taking into account such costs as ransom, investigation, containment, regulatory fines and lost sales.
Recovering from a breach used to involve spending currency denominated only in banknotes. Now that currency is denominated in reputation, trade secrets and intellectual property.
Shadow IT
BYOD brings about an inevitable discrepancy between work practices that are convenient for the employee and those that are secure for the company. Storing files on sharing sites, using unauthorized cloud applications and sending documents as attachments in unencrypted email messages are examples of time-saving measures unsanctioned by IT. It’s no surprise that employees will take the path of least resistance to accomplish their tasks, especially when IT is scrambling to keep up with the pace of BYOD adoption.
Departing employees
When a device is personally owned, naturally the employee keeps it upon leaving the company. But how much company information remains on it after the employee’s departure? Without endpoint management, this represents a much higher risk than a physical device walking out the door. The risk lies in what is still on that device, and what the device can still access.
How can IT teams address BYOD security risks?
With the genie out of the lamp, IT admins know that they must accommodate personally-owned devices even as they try to mitigate BYOD security risks and challenges. Here are some common ways of addressing those risks:
Secure the network and apps
Ensure that the business apps being used can secure data both at rest and in transit. Instead of relying on a virtual private network (VPN), make sure that the applications in question can handle secure data transactions.
Keep in mind that, in general, the network should be considered unsecure. To the extent that a company’s network depends on the internet, it is an inherently untrusted, unsecured network. Focus on the route that the application takes to transmit and receive data, ensuring that the business application has proper authentication in place and is using enterprise-strength encryption.
Encryption at rest means that an attacker cannot simply open a file and read its data. Encryption in transit means that transmission occurs over HTTPS or some kind of secure channel so nobody can simply inspect traffic.
Device locating services
Since the primary concern is the loss or theft of a personally-owned device, what if the organization offers to help recover it? As part of the organization’s BYOD policy, consider including an agreement that allows IT to work with the employee to relocate a personal device. Not all users are technically savvy enough to know what technology is available to help recover a lost smartphone, tablet or computer. Such an agreement positions IT favorably if allowed to help with recovery efforts.
Reconsider BYOD
In some industries and use cases, allowing personal devices to access corporate data is not a security-conscious approach to driving business productivity. IT and the company in general assume considerable liability so that users can work conveniently; no organization should take that lightly or without proper reflection.
The case for avoiding BYOD altogether by using only company-owned, company-managed devices can be compelling. It embodies the tradeoff in costs for buying and managing devices against the potential costs of recovering from a data breach. While expensive, the practice of procuring and issuing devices removes IT from the unpleasant business of establishing policies and mitigating BYOD security risks. It also clearly separates company-owned equipment and information from employee-owned equipment and information.
Strategies and best practices for mitigating BYOD security risks
There are ways to combine user convenience with a tight security posture, even in the BYOD landscape. For example:
Define BYOD policies carefully and thoughtfully
Well-defined BYOD policies make it explicitly clear what expectations are for every team member. For example, a well-defined BYOD policy could dictate that the ability to access company applications and files on their own devices is contingent on employees using select applications managed by the company. Additionally, there would be spelled-out consequences for employees who do not comply with the policy.
The ideal complement to such a policy is to get written agreement from the employee and to put periodic training in place to reinforce it.
Implement Zero Trust
A company-wide Zero Trust approach to endpoint security is the way to address BYOD security risks introduced. Zero Trust assumes that all business systems must prove confidence in the user identity, the device and the communication channel being used to consume the data.
Deploy endpoint management
Implement a unified endpoint management (UEM) system that can accommodate both personal and company-owned devices.
This is the most comprehensive way of managing apps, whether on smartphones, tablets or computers. With fully managed devices, IT can exert control at a sufficiently deep level to prevent the installation of and access to apps from untrusted sources. If that level of control is in place and the employee clicks on or taps a dodgy link, then the device should be able to block it. At a minimum, it will warn the employee through a dialogue box that the link is suspicious and untrusted.
Get ahead of shadow IT
Regardless of how hard teams work to get ahead of shadow IT, employees will take the path of least resistance and use unsanctioned applications and software when IT is unable to keep up with their drive for productivity. If the organization’s IT team cannot offer the applications employees need to be productive, then employees will find their own way to make it happen.
But if policies, workflow and apps are in place for must-have functions like single sign-on, multifactor authentication (MFA) and file sharing, then employees don’t need shadow IT. And so much the better if the organization is willing to manage those functions and keep them separate from the personal data on the employee’s device. The objective is to make it more attractive to the employee to adhere to policy than to disobey it.
Conduct regular training in BYOD security risks
Regularly conduct security training with employees to ensure they know how to use their personal device within a business environment. This training complements standard training on security topics by emphasizing how to live in two worlds — business and personal — on one device. It reminds employees how to spot suspicious behavior and when to have that red flag go off in their head so they can respond promptly.
Provide authentication methods
As part of a Zero Trust approach, ensure that proper sign-on and authentication methods are in place to verify users. Companies considering BYOD find themselves on a journey towards modern management — the ability to allow team members to work outside the corporate office as easily and efficiently as inside.
That used to mean being inside the perimeter, logged in and joined to the domain. In the era of work-from-home and remote-work-from-anywhere, it usually means connecting to company resources over a VPN. But when running across the corporate firewall, proper authentication needs to run deeper because it’s a matter of being able to verify users. That calls for authentication through a solid identity provider, and possibly an additional layer of MFA.
Classify employees and grant proper privileges/employee lifecycle process
Another huge advantage of using a solid identity provider is the ease with which IT can on and off-board employees. Instead of having to create accounts for each of the applications and network resources that new users will access, IT creates a single identity that all apps and resources trust. Then, at the end of the employee lifecycle, when users depart, IT disables their identity in one place, which disables their access to all apps and resources.
It’s a smart, thorough approach to on- and off-boarding because it enables IT to zoom out and manages dozens of systems uniformly, rather than as a collection of one-offs.
What can an organization do if a BYOD device is compromised?
As noted above, if the device is not properly managed, and it contains both personal and business-related data, the company runs the risk of having proprietary information exposed. If the device is properly managed, and the device is lost or stolen, implementing a wipe command should remotely remove all of the company-managed data from that device. In either case, the user should observe whatever security protocols the device vendor provides to locate or reset the device, if possible.
If a BYOD device is infected by malware and demonstrates suspicious behavior, the usual steps apply: isolating the device from the network, running anti-malware and conducting forensics to determine collateral damage. Given the point of diminishing returns, however, many IT teams will specify a threshold past in which it is more efficient to simply factory-reset the device. Naturally, that will purge it of all personal and business-related data, but it is a valid risk-mitigation tactic.
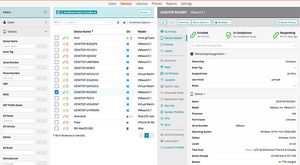
Patch, secure, and manage every endpoint
The biggest mistakes organizations make when implementing BYOD
Companies that ignore the need for clear user communication do so at their own peril. From clearly spelling out policies on BYOD to regular security training and countermeasures, the burden lies with the company to set the tone for BYOD behavior. However, the biggest mistake is poor infrastructure: the absence of groundwork needed to ensure the success of any BYOD strategy.
That’s why smart companies avoid mistakes by starting with a security assessment. By embarking on BYOD, the organization opens its doors to a new way of doing business with its employees: cloud-based, internet-based and software-as-a-service-based. A preliminary assessment is the key to discovering coverage gaps and holes before the journey even begins.
Smart companies also line up an identity provider whose solutions allow them to put in place the authentication needed for secure access to company applications and data.
Summary
Though team members may not understand the security vulnerabilities involved with using personal devices to access work resources, IT teams are acutely aware of the extra responsibility and security risks that those unsecured endpoints create. Whether an organization decides to formalize a BYOD policy, or exclude the use of personal devices for work purposes, organizations and their IT teams will need to carefully consider how they want to best secure their endpoints and how they want to mitigate potential BYOD security risks.