
VPN. VPN. VPN. This pushed-aside and closely guarded technology has suddenly seen a resurgence during the COVID-19 work-from-home directives; but instead of just your executives receiving access, IT organizations are opening up access to all remote employees. VPNs are now a major priority for remote user productivity.
Cyber criminals see your VPN priority as their priority too as a means to steal those same credentials and access.
Homeland Security CISA guidance on VPNs (AA20-073A)?
VPN security is such a concern that the U.S. Department of Homeland Security CISA put out an Alert on March 13, 2020 to educate organizations to the dangers of vulnerable, unpatched and unmonitored VPNs.
You can read the full alert here, but here’s the gist: As more organizations rely on VPNs during this pandemic
- IT personnel are distracted trying to support these newly remote employees
- This impacts their ability to perform cyber security tasks
- And the 24/7 nature of a VPN and the importance of maintaining user productivity means those VPNs go without the latest security updates and patches.
Oh, and the malicious attackers who are also hunkered down at home are targeting those connections and exploiting the vulnerabilities and distractions.
VPN attacks
Access to a network’s resources through a remote service like a VPN is not new. Exploiting vulnerabilities or stealing credentials has always been in their tool bag. The concern is that a VPN, which everyone is now accessing, gives an adversary the ability to persist within a network, and, especially while everyone is distracted in today’s crisis.
Numerous known threat groups have used remote services to gain a foothold in organizations, including:
- APT18: known for targeting technology, manufacturing, human rights groups, government and medical1
- Dragonfly 2.0: known for targeting government and U.S. critical infrastructure1
- Ke3chang: known for targeting oil, military and more1
Most of these organizations used stole credentials, most likely gained through phishing campaigns.
And even when it’s possible to evict someone from the corporate VPN, they can regain access with a stolen VPN certificate extracted from the original compromised workstation!
Furthermore, with so many users connecting via VPN, adversaries are also using DDoS attacks on VPN services to crash their servers or limit availability, like the failed DDoS attack on a Paris hospital treating Coronavirus patients.
VPN attack mitigation

Some VPN security best practices recommend removing unnecessary user or program access and limiting domain resource access over VPN; all good recommendations in normal times. But these aren’t normal times, so infrastructure and operations teams must maintain a careful balance of ensuring remote access to resources and maintaining proper security, monitoring and patching practices.
One solution. Many workloads.
Here’s a list of recommendations to help you secure your network.
6 quick VPN security wins
- Give your users a refresher in phishing hygiene and continually alert them to the active phishing scams targeting your organization
- Enable multi-factor authentication (MFA) to impede an adversary’s ability to leverage stolen credentials if the phishing scams are successful
- Patch. Patch. Patch. If you don’t know why this is important yet, read this CISA Security Tip (ST04-006)
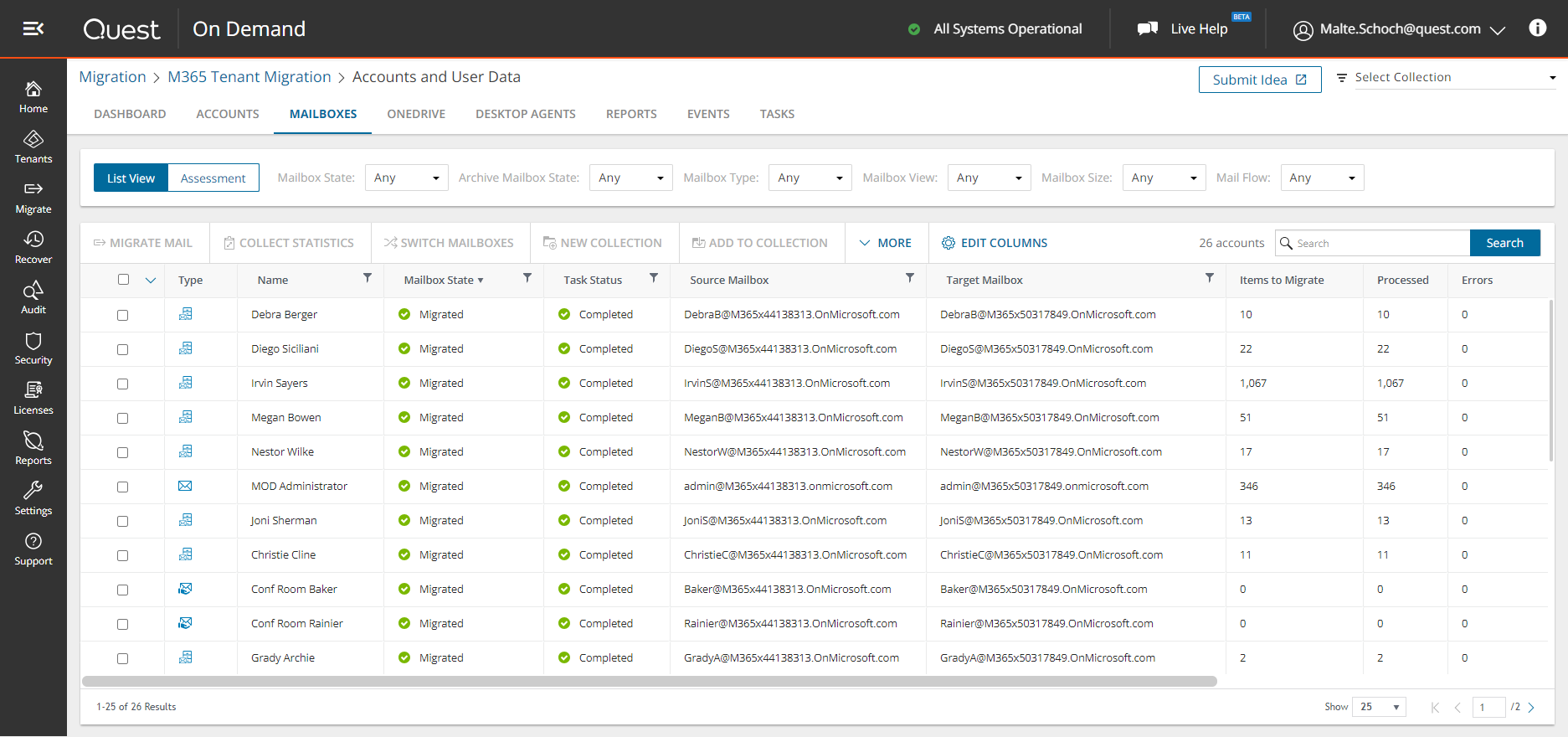
- Monitor VPN logon, user activity and volume of transferred data with an event log management solution like Quest InTrust, which enables you to collect, store, search and analyze massive amounts of data from numerous sources, systems and devices
- Automate response actions for suspicious activities such as kicking off unauthorized users or blocking VPN access until a forensic investigation can be performed, such as found within Quest InTrust.
- Remind users regularly that a VPN isn’t always necessary to access the services and applications they need, such as Office 365 email and cloud storage and collaboration platforms (you can name the user notification: To VPN or not to VPN).
Longer-term VPN security considerations
- Isolate critical systems through network segmentation to reduce access to sensitive systems and information. You’ll need an infrastructure reporting solution to help in this process, like Enterprise Reporter
- Migrate critical file shares and services into Office 365 services like One Drive, SharePoint or Teams, thus removing the need for VPN access to those resources and instead leveraging the infrastructure security investment of Microsoft.
As you evaluate your VPN security, consider a solution that monitors all of those remote devices (official workstations or BYOs) connecting to the VPN. Quest InTrust enables you to monitor these connected remote devices for malicious processes and activities; and InTrust can also kill those processes and activities for VPN connected devices AND suspicious PowerShell commands for non-VPNed devices.
Most cyber attacks today start on the user workstation. I encourage you to learn more in this ebook: Top 3 workstation logs to monitor: Improve endpoint security with Sysmon, PowerShell and security logs.
SOURCES:
- https://attack.mitre.org/techniques/T1133/



