In the early days of Active Directory, a decision had to be made as to whether you were going to do an in-place upgrade of your existing Windows NT 4.0 environment, or if you were going to do a “greenfield” migration. Some organizations had multiple domains and did a combination of both. As Active Directory (AD) grew in popularity, there were less greenfield migrations and more AD forest-level consolidations (especially with mergers and acquisitions increasing rapidly). In today’s world, there are AD migrations occurring with the intent to be more secure.
“Red Forest”
Most organizations have invested heavily in perimeter defense, but the reality is that 90 percent of organizations feel vulnerable to insider attacks. An employee stealing intellectual property to take to a new job or a fat-fingered administrator making a critical configuration error are examples of breaches caused by someone inside the network. Often, an outside attacker takes over a legitimate account: Microsoft has reported that, every day, 95 million Active Directory accounts and 10 million Azure AD accounts are the target of cyberattacks.
The primary vector has now shifted from direct attack on a compute resource to theft of user credentials, often by means of a phishing attack. Once a user’s credentials are obtained, the attacker has access to a workstation on which to run software that captures the credentials of other accounts. Preferred targets are service accounts and Domain Administrator accounts, allowing the attacker to traverse the infrastructure horizontally and vertically.
To thwart attackers pursuing horizontal kill chains with pass-the-hash and related methods, Microsoft has delivered a reference architecture and other best practices that seek to isolate privileged credentials. Microsoft recommends a new security model, the Enhanced Security Admin Environment (ESAE), for holding the accounts that require additional security due to their privileged access to the production forest. ESAE is a special administrative forest, also known as a Red Forest, used to manage all privileged identities in AD, making it more secure.
A key principle of the Active Directory Red Forest model is that admin accounts are divided into three levels of security:
- Tier 0 — Domain Controllers (DCs), identity management resources, administrator user accounts and service accounts
- Tier 1 — Server, application and cloud admin authority
- Tier 2 — Standard user accounts, workstations, printers and devices
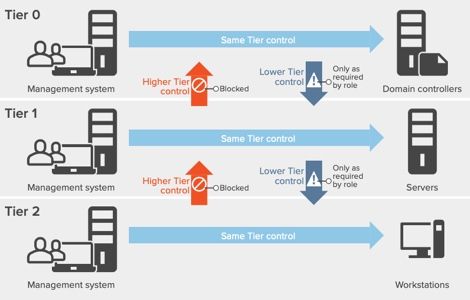
Figure 1: Control restrictions in the Active Directory administrative tier model
The recommendations only include Microsoft products (this makes sense as it would be hard to recommend other products that they have no control over). When using this architecture, one component that may not work for most organizations is disabling NTLM authentication. With that said, this may not be practical for all organizations (although I’d highly recommend this model if possible, but you many need to re-architect legacy applications).
Another guiding principle of Microsoft’s security strategy is to “assume breach”. With that said, you may need to also consider doing a full migration of your existing environment to another environment as a risk mitigation. In most organizations, this can be a costly and time-consuming project. Although Microsoft makes recommendations for only Microsoft products, I still believe Quest has some offerings that can complement this model.
For more information, watch a recorded webcast where security expert Randy Franklin Smith explains the reasons why you might go to this extra trouble — as well as the limitations of this structure.
“Orange Forest”
Before you start Googling or searching TechNet, please note that this is NOT a well-known industry term (yet).
A customer of mine used the phrase “Orange Forest” when describing their implementation of the Active Directory Red Forest. Due to the high cost of performing an AD migration, they were planning on deploying a separate administrative forest as the Red Forest suggests, but not do a migration. So, they called this “Orange Forest”, as they were not quite fully red.
Reflecting on this term, I realized that the Quest portfolio has been allowing customers to act in the Orange Forest scenario for quite some time. By removing admins’ native rights to the directory and connecting to Active Directory via proxy, we added additional capabilities that can be useful in both the Red and Orange Forest scenarios. Here are a few examples:
- Workflow approval prior to a change happening in Active Directory
- Workflow approval prior to a change happening in Group Policy
- Least privilege access of Active Directory and GPO’s
By having this proxy approach to your Active Directory, you can ensure nobody has more rights than they need to do their job and can eliminate users from having to be in privileged groups. Creating the least privileged access model can be difficult. However, Quest not only has AD tools that can help you, but also professional services offerings to provide you data to make a decision as to who should be able to do what in your environment.
“Greenfield”
If you have experienced a security breach and have made the decision to move to the Red Forest design, a migration may soon be in your future. Quest has been doing AD migrations for decades and has also been helping customers migrate to a new greenfield forest connected to your new Red Forest design. There are many challenges in doing a migration that you should consider.
- Application remediation
- User downtime and experience
- Server migration
“Blue Team”
Blue refers to the Blue Team which is usually part of the security team tasked with the defense of the network. Quest has products that can help you regardless of if you choose to go to the Red Forest or Orange Forest model, and also have people that can help you in this transition. If you would like to discuss how we can help, please feel free to reach out!