Ransomware payouts are trending back up. According to Chainalysis, a cryptocurrency tracing firm, 2021 was a record year for ransomware payments, totaling almost $1 billion. In 2022, there was a drop, but in 2023, ransomware payouts returned to that same torrid pace with an estimated $900 million in payments. This rise in ransomware activity can be attributed to the ramping up of ransomware group operations and a surge in extortion efforts. To avoid becoming a victim and defend against ransomware threats, you need a strong backup plan that takes into account the many ways that attackers can infiltrate your network.
Ransomware attack strategies
There are a few main strategies that attackers use to access your data.
Strategy 1: Malware spray attacks
The first strategy involves purchasing malware on the dark web for ransomware as the service operations or brokers of individual components. These tools require very little skill, and attackers can essentially follow Wizards to launch attacks without necessarily targeting any company in particular. In this spray and pray approach, organizations with unpatched vulnerabilities, limited monitoring, inconsistent backups, and other security hygiene problems are the most susceptible, regardless of their size. The hope is that one of many victims provides a payout.
There are some key characteristics to keep in mind for this type of attack. For starters, it doesn’t demand much expertise or capital. Perpetrators don’t need to pay skilled hackers or invest in learning themselves. Plus, prices for tools and compromised credentials on the dark web can be shockingly low.
The dwell time can be somewhat short. As soon as an attacker gains access, encryption may begin automatically, and the ransom note will appear. Because the attacker has little research on you as an organization, the ransom will probably be on the lower side so that you can quickly pay it off.
Defense 1: Protection in layers
The most important thing to remember about this ransomware strategy is attackers are casting a wide net. They are not targeting a specific business and are instead looking for a back door to enter.
The best protection against this kind of attack is a layered defense. Rather than rely on a single solution for cover, having multiple assurances in place helps minimize the threat and the impact of a ransomware attack. These layers of defense can include properly educating and training end-users on ransomware risks, applying automated patches, updating all servers, routine network monitoring, and implementing data protection for your backup. Every organization’s defense plan can look different, depending on their needs and what they would like to protect.
Ideally, you want to stop these spray and pray attacks with your first few protection layers and have your backup as the last line of defense. These types of unsophisticated ransomware attacks are extremely common and are the kinds of attacks that are easiest to protect against once you have a plan in place.
Strategy 2: Targeted recon
The second strategy is highly targeted and entails conducting some reconnaissance on your organization. Attackers will spend some time getting to know you: finding out what software and cloud infrastructure you’re using, picking through social media posts of employees, scanning the network, buying some dark web databases of exposed username and password combinations, researching the CEO for a whaling attack, using ChatGPT variance to refine the English for phishing efforts. Once they’ve gotten into your network, these attackers move laterally and might be around for longer than average conducting more research on your backups, your insurance policy, and any financial information they can get.
The goal is to develop a sophisticated and high ransom demand that takes all the information they’ve learned into account. High skill is required for this type of approach. It involves financial investment in building ransomware skills or hiring people who can do this. These types of attacks will probably choose a victim ahead of time or target a small group of victims. Any organization can be targeted with this strategy, though larger or higher profile organizations are more at risk. Extortion is also likely in addition to, or even instead of, that ransom.
Defense 2: Document a plan
Every successful attack goes back to an entry point, and it’s crucial to understand how attackers get into those entry points. There are numerous lists of security breaches with detailed information about how those breaches happened. Understanding those entry points and how they evolve over time will enable you to refine your approach to defending against ransomware attacks.
Not too long ago, you would never have thought that a key card to get into a building could be used to infiltrate a network. You would never have thought that a manufacturer of a motherboard or an Ethernet card could put firmware into that card that is undetectable by the OS, yet leaking information in some way. There’s a long list of these kinds of threats that you wouldn’t have thought were possible a few years ago, that are now possible.
To protect your organization from sophisticated attacks, it’s critical to document your plan. What you’re trying to achieve is a presentation of what threats exist, what their priorities are and how to defend yourself against them. At this level, it’s necessary to have a measured response that shows consideration of the current threat landscape.
How to start to create your plan
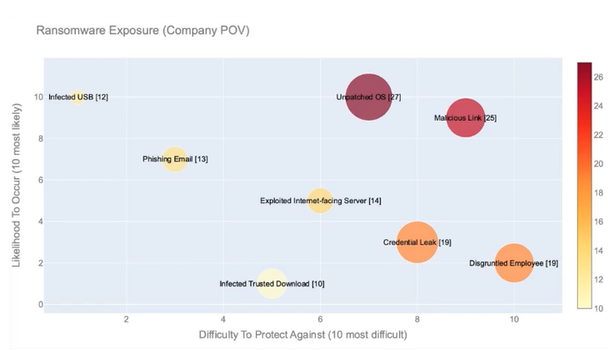
There could be dozens or even hundreds of different kinds of threats to your business. In creating a ransomware defense plan, it’s important to consider the likelihood of different attacks to occur—based on security breaches that are known to have occurred—along with the difficulty of protecting against each kind of attack and the associated costs.
Depending on where your priorities lie, you can begin to build a ransomware protection strategy. If you’re a cost-conscious company, you might start by considering the threats that are most likely to occur. If you have other priorities, you might begin by figuring out how to protect against the most difficult threats. For every possible threat, your plan should lay out a documented strategy on how the attack might affect your business and how to protect against it.
The importance of backup
While prevention is a major part of any ransomware protection plan, an equally essential part is a reliable backup and recovery solution. Despite your best efforts to prevent an attack, with the constant evolution of ransomware threats, it’s reasonable to assume that one will eventually succeed. To ensure your organization is fully protected, your backup solution needs to have data protection capabilities and enable quick and full recovery. While not making up the entire plan, having a 3-2-1 rule for backup is a good start.
Modern, advanced backup technologies provide features like continuous data protection to lower RTOs and RPOs, backup immutability with object storage locking, air-gapped backup to tape, secure data encryption, and instant restore. Having a backup and recovery solution in place with these qualities will serve as a safeguard for the inevitability of a ransomware attack and enable your business to promptly recover and resume operations.
Of course, you want to avoid getting to the point where you need to use your backup, but it does act as your last line of defense. The goal is to make sure that this safety net can nullify a ransomware attack if, and when, other security measures fall short.
Strategy 3: Exfiltration
Exfiltration is another top way that attackers use to bring in money. They start by encrypting data, then exfiltrating it and demanding either a decryption ransom or an extortion payment. A demand for decryption is one of the more classic routes for ransomware, but extortion is becoming more common, especially if there’s personally identifiable information in your data.
There is also no guarantee that one attack is the end. Even though an attacker might claim that they’ll delete your data once they receive payment, they may very well use that data again, either in another attack or by selling it privately.
Defense 3: Encrypt your backups
When you encrypt your data, it is much harder for cybercriminals to read the backup or use that information in an unauthorized way.
Encryption is a big part of backup, but even just a few years ago, it was best practice to only encrypt backups that were going off site. If your backups were being sent to a device locally, the old way of thinking was that those backups didn’t need to be encrypted because the data wasn’t going outside the network. Today, whether your backups live on-premises or in the cloud, whether in flight or at rest, they need to be encrypted.
Dwell times
What is an attacker doing once they’ve gained access to your data? This is the period of time when a bad actor has breached your network but hasn’t yet announced their presence or initiated an attack. Over the years, there has been research about attackers lingering for surprisingly short amounts of time, meaning organizations don’t have that long to detect them and kick them out before they launch an attack. To get an idea of that duration, in 2022, the average dwell time for Sophos and Mandiant was 9 days.
Protect all your systems, applications and data.
When an attacker is dwelling, they can be trying to elevate the privileges they’ve gained and move laterally through the network to do recon for partner connections. They can also be spending time assessing the value of the data, looking for insurance terms, finding a way to corrupt backups and stealing copies of valuable data.
Defending against hidden ransomware
While Sophos and Mandiant showed the average dwell time was measured in days, there is a history of successful hacks occurring when the ransomware itself was planted in the network for months before it began to cause issues. Over the course of a few months, this ransomware can lay dormant while you backup your systems every day, unknowingly putting infected data into your backup. When that ransomware is activated, it’s important to make sure that you’re not reinfecting yourself by restoring backups that have been compromised.
To protect yourself when you’re doing restores, plan and test your disaster recoveries. Frequently document that plan and make sure that you’re accountable for performing those tests. The worst time to find out that your plan falls short is when you need it the most. In the event of a disaster ransomware breach, you should have a plan for what needs to be done and be able to restore it with confidence.
Conclusion
The escalating trend of ransomware payouts underscores the persistent threats that organizations face on a day-to-day basis. Defending against these multifaceted threats demands a robust defense plan with a comprehensive backup solution and a deep understanding of potential entry points. Organizations must be vigilant in planning for, detecting and responding to attacks. As cyber threats continue to evolve, a proactive and adaptive approach is crucial for businesses to defend against ransomware.