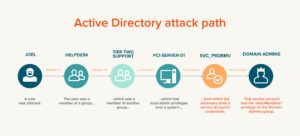
A quick search for “DCSync” returns 83,500 pages. There is a lot of information out there to absorb. Don’t let the first result fool you, DCSync is more than just a McDonald’s employee portal. You could sift through the other 83,499 results or just continue reading here. This article explains what a DCSync attack is and why it’s used. The results of a successful DCSync attack may be devastating but there are defense and detection strategies that can better protect enterprises.
A quick search for “DCSync” returns 83,500 pages. There is a lot of information out there to absorb. Don’t let the first result fool you, DCSync is more than just a McDonald’s employee portal. You could sift through the other 83,499 results or just continue reading here. This article explains what a DCSync attack is and why it’s used. The results of a successful DCSync attack may be devastating but there are defense and detection strategies that can better protect enterprises.
What is a DCSync attack?
DCSync is a technique used to abuse domain controller (DC) synchronization. Hence the name, DCSync. A key functionality of DCs is the replication process where all DCs in a domain share information about Active Directory (AD). Similar to DCShadow, a DCSync attack simulates this replication process to trick AD into sharing sensitive information. Most notably, password data. During a DCSync attack, current and historical password hashes are extracted and may be used in numerous different ways.
How common are DCSync attacks?
MITRE ATT&CK references recent well-known groups and campaigns in its explanation of DCSync. The threat group known as LAPSUS$ utilized DCSync attacks to perform privilege escalation in its recent attacks. The infamous Solar Winds compromise also involved DCSync attacks.
DCSync is categorized as a credential dumping technique that is most commonly utilized to maintain persistence or elevate privileges. Because DCSync requires an AD account with elevated privileges, it is not involved in every campaign. In many cases, an attacker must first gain access to an account with membership in the Administrators, Domain Admins, or Enterprise Admin group. With access to such a highly privileged account, an attacker may already have what they came for.
A more common scenario involves accounts delegated “Replicating Directory Changes” permissions instead of membership in privileged groups. This type of permission is common for applications that integrate with AD, specifically the Azure AD DS Connector account requires these permissions. In this case, an attacker can leverage this account to perform a DCSync attack.
How does a DCSync attack work?
A DCSync attack is typically referenced when using the mimikatz toolkit but other tools such as Impacket’s secretsdump and DSInternals Get-ADReplAccount perform the same attack. Regardless of the method, this attack first requires credentials of an account granted the permissions mentioned above.
DCSync does not require interactive logon of a DC. Using a remote DC is a configuration option in each tool and is simply ran from any machine on the network. Depending on the goal, an attacker could simply target a specific user account or dump the entirety of AD to a file.
What are the implications of these types of attacks?
Once AD data has been extracted, there are multiple pathways for additional attack. The password hashes may first be used in attacks that require no knowledge of the clear-text password. Pass-the-hash, NTLM Relay, and Pass the Ticket are all options to authenticate as any AD user. An attacker may also attempt to crack the password hashes. Knowledge of a clear-text password offers more opportunities such as the ability to login to other applications. Some examples may be a human resources or financial application but it also allows attackers to pivot into the cloud, logging into Azure AD or Office 365. If an attacker is able to crack even a small percentage of current or historic passwords it gives them insight into password trends of the organization or may identify default passwords that could be used elsewhere.
Even more dangerous is storing passwords using reversible-encryption. Accounts marked this way via configuration policy store their password in AD in clear-text. A DCSync attack pulls these account passwords and an attacker could immediately authenticate using those account credentials.
Another common technique that results from a DCSync attack is to obtain a Golden Ticket. A Golden Ticket attack is possible when an attacker obtains the password hash of the KRBTGT account. This allows an attacker to forge Kerberos tickets that would allow them to authenticate as any account in AD.
Several other attacks are possible but the moral of the story is; if an attacker performs a DCSync attack against an environment, it’s going to be a bad day.
How to protect AD against DCSync attacks
Pulling off a DCSync attack requires elevated permissions. Properly protecting these accounts is the best way to defend against attacks. Scrutinizing account membership in the Administrators, Domain Admins, and Enterprise Admins groups is the first step. Accounts that remain in these groups must be dedicated admin accounts with good passwords and account protections in place. Accounts granted “Replicating Directory Changes” at the domain root must also be identified and protected in a similar manner.
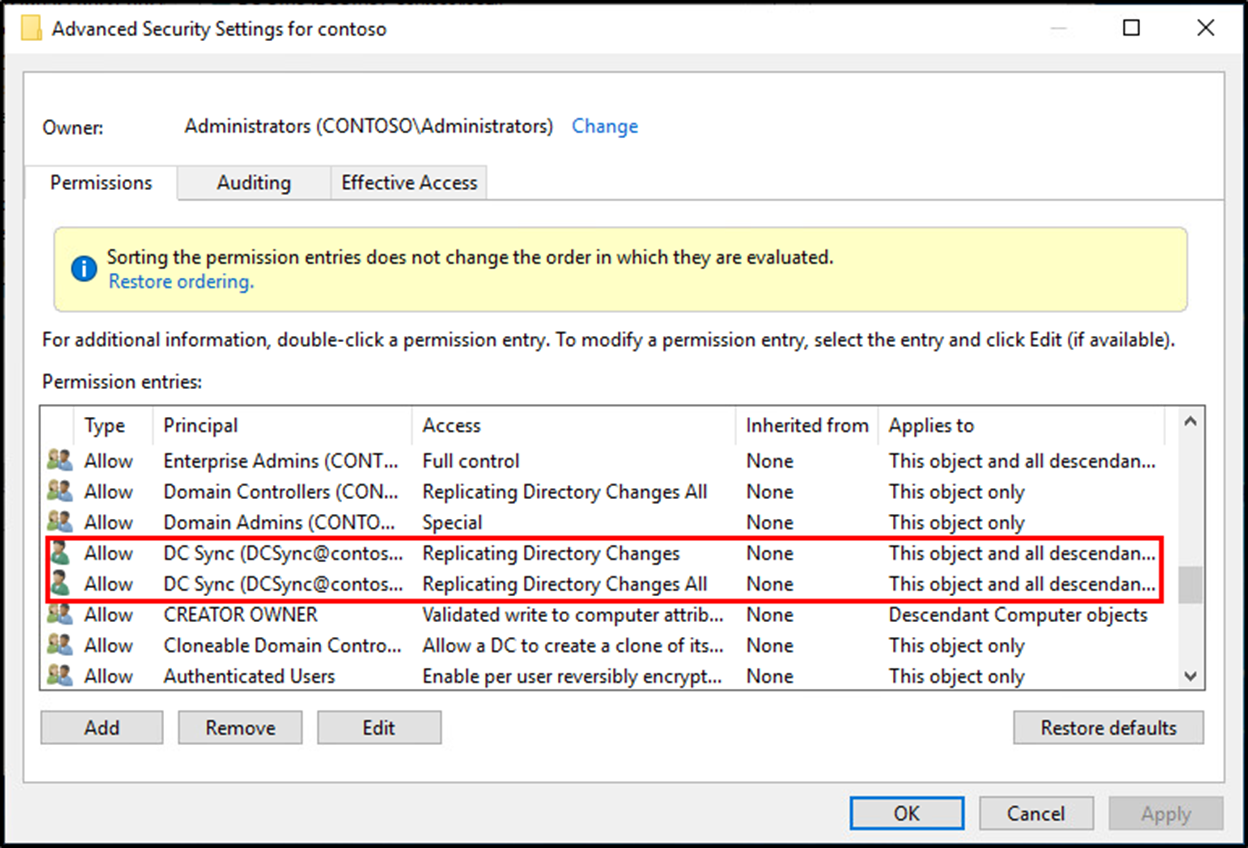
Another group I failed to mention earlier that has rights to perform DCSync are the domain controllers themselves. This seems obvious but it’s worth noting in the defense section because one DC can be used to attack another, pulling off a DCSync with only a regular user account. Protecting DCs from this attack includes enforcing NTLMv2, applying monthly security patches, and running the most up-to-date OS. Here is a detailed walkthrough of this attack.
Detecting a DCSync attack includes monitoring network traffic for replication events originating from a non-DC IP address. The traffic of interest uses the DRSUAPI protocol to request a DsGetNCChanges operation. More details for this detection can be found here.
The windows event logs may also provide insight into a DCSync attack. Event ID 4662 on DCs indicates a replication event occurred. Filtering on the GUIDs associated with DS-Replication-Get-Changes (1131f6aa-9c07-11d1-f79f-00c04fc2dcd2) and DS-Replication-Get-Changes-All (1131f6ad-9c07-11d1-f79f-00c04fc2dcd2) will display information regarding the replication event and may help identify the account(s) being targeted.
Conclusion
As with any attack, prevention and detection are key. Preventing a DCSync attack involves protecting privileged AD accounts, a process that shouldn’t require a breach before it begins. The second half of a defense strategy is responding to events. A good detection strategy could quickly identify suspicious replication and initiate a response before too much damage is done.
A solid understanding of DCSync helps to combat the attackers trying to use it. Arm yourself with knowledge and harden your environments. Doing so may send those attackers to that McDonalds portal looking for a new job.