Sean Metcalf, Microsoft Certified Master, and I took your AD security questions during Microsoft Ignite. Sean kicked off this Q&A with six timeless AD security public service announcements for any hybrid AD environment. I’ll review Sean’s specific PSAs in more detail so you can reference this and add these to your regular AD security reviews.
Patch Domain Controllers against ZeroLogon (CVE-2020-1472)
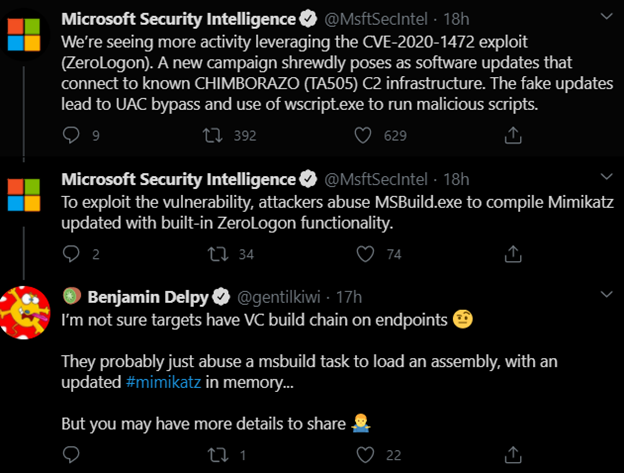
If you haven’t done this already, please DO now. This is actively being exploited and should be prioritized. Below you can see a recent Twitter warning from Microsoft and since then we’ve seen countless articles of groups leveraging this vulnerability, including threat actors TA505 and MERCURY seeking to gain control privileges, and even unidentified APTs seeking to disrupt the 2020 U.S. election.1, 2, 3
The timeless part of this PSA is that your DCs should always have the latest patch. Don’t wait. Don’t let them pile up. Patch. Patch. Patch.
Change your (AD) KRBTGT account password 2x/year
The KRBTGT is a disabled domain account that is used as the Kerberos service count for the domain. This account is highly privileged given that it’s used for Kerberos ticket operations. Once someone obtains this password hash, this person will have the ability to create golden tickets in your environment. A golden ticket gives complete access to your entire domain since Active Directory uses Kerberos, and a Kerberos golden ticket has unlimited access to what it can do. We break down these attacks in detail in this article: Golden Ticket Attacks: How They Work and How to Defend Against Them.
This password needs to change at least twice every year. By rotating KRBTGT at a regular interval, if someone is using a golden ticket, this will stop the usage. Moreover, find a change auditing tool that can detect if a golden ticket is being used in your environment.
Create and test an AD disaster recovery plan
The likelihood of a ransomware attack affecting your organization, INCLUDING Active Directory, is at an all-time high. If you don’t have a plan, it’s critical that you create one. If you do have a plan, it’s critical that you test it. If you’ve recently done a test, consider other scenarios as well. Not all disasters may be from ransomware. Some may just be AD corruption or even downtime when an organization has a good intent (changing an old service account password and not being able to restore the old password and having an application break).
Protect Azure AD Connect Server like a DC
Because Azure AD Connect has the ability to get password hashes and move them to Azure AD, this should be protected just like a domain controller. Azure AD connect service account is highly privileged and it controls other Azure AD integration services. Verify who has rights to this machine. Hopefully you have considered moving to a tiered management approach like ESAE (Enhanced Security Admin Environment), Red Forest or an Orange Forest (Quest’s approach to delegating out who can do what at different layers of your directory). Any kind of tiered management approach would put in policies to restrict Domain Admins and others to logging on locally.
Limit which accounts are in Global Administrator Role
There is a shared responsibility in regards to AD security. Microsoft may be your service provider, but that does not guarantee that your organization can’t hurt itself. Microsoft recommends having fewer than five people with Global Admin rights, which grants full access to Azure AD, Office 365 and can also control Azure. It’s also imperative you layer on multifactor authentication (MFA) for these accounts for added security controls.

Reduce your AD attack surface.
Microsoft does provide for different roles that can be used for least privilege in Azure AD security and this will help protect all of your assets in Office 365.
Use Azure AD PIM for admin accounts in Privileged Roles
Any privileged account, like Global Administrator for Azure AD, should have extra protections. This is why any account that is in a privileged role should be using Azure AD PIM (Privileged Identity Management). Immediately after turning on PIM you will receive notification email messages for Privileged Access Role changes. It is advisable to add extra scrutiny anytime these group membership settings are changed. Doing continuous attestation can help with least privilege access.
Seek a solution that extends out attestations to your hybrid environment and helps with your existing group membership.
Summary
By implementing these timeless solutions, you’ll significantly boost AD security and further solidify your stronghold against ransomware and other threats, both external and internal. And when I say timeless, I mean these AD security essentials should always be followed AND in a timely fashion – meaning don’t wait!



