Kerberos has been the default authentication protocol in Active Directory (AD) environments since Windows Server 2000. While Kerberos is far more secure than the older NTLM protocol, it is not bulletproof. Indeed, because Kerberos controls access to so many IT environments around the world, adversaries are constantly looking for — and finding — ways to abuse it. Accordingly, IT pros need to stay on top of known exploits and mitigation measures that can reduce the risk of security breaches.
Right now, that means paying attention to the Windows updates from November 8, 2022, which address critical Kerberos vulnerabilities (CVE-2022-37966 and CVE-2022-37967) that could allow an attacker to elevate their privileges. Microsoft recommends installing these updates to all devices, including domain controllers, as described in KB5021131 and KB5020805.
However, installing the November updates has caused authentication issues, user sign-in failure, the inability of users to access shared folders and other problems. Moreover, fully mitigating the vulnerabilities will break Kerberos authentication unless an organization takes steps to address the side effects. Accordingly, Microsoft is planning a series of security updates in the coming months that will help you secure Kerberos authentication without disrupting your business.
This blog post offers guidance on deploying the November 8 updates to address these Kerberos vulnerabilities and how to plan for the upcoming updates that complete the Kerberos hardening process.
Mitigating CVE-2022-37966
KB5021131 details how to manage the Kerberos protocol changes related to CVE-2022-37966. I recommend taking all the steps detailed there. Let’s look deeper into two of them.
Identifying impacted systems
After installing the November security updates on your domain controllers, you may find that you suffer from authentication errors. They are also triggered if you have specifically set the encryption level on user accounts to DES/RC4 rather than AES.
To identify systems that might be impacted, run the following PowerShell script:
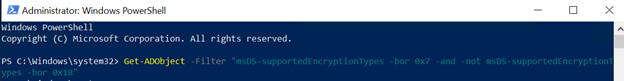
Get-ADObject -Filter “msDS-supportedEncryptionTypes -bor 0x7 -and -not msDS-supportedEncryptionTypes -bor 0x18”
Resetting the KRBTGT account’s password
Another step involves resetting the password of the KRBTGT account. You probably know that Golden Ticket attacks take advantage of a vulnerability in the Kerberos protocol — the assumption that any ticket granting ticket (TGT) encrypted with the password hash of the KRBTGT account is legitimate. As a result, an attacker who steals your KRBTGT account’s password hash can then grant themselves full access to your network.
Therefore, if you have had an intrusion, or even suspect that you’ve had one, you will want to change that password immediately after the network has been stabilized. Even if you have not suffered an attack, you should change it at least twice a year.
But once you have installed the November security update, you have another reason to change the KRBTGT account’s password: If you have not reset that password since upgrading the AD Domain Functional Level (DFL) to Windows Server 2008 or higher, or your DFL still runs Windows Server 2003, you will see Event ID 42 errors in your system logs.
Microsoft provides a PowerShell script that resets the KRBTGT password. But to run that script, you need to be on a DFL of Server 2008 or higher. To check what DFL you are on, run the following command from an elevated PowerShell prompt:
Get-ADDomain | fl Name,DomainMode
If you are still on an older level, it would be wise to investigate whether you can move to at least Server 2008. In addition, if you haven’t moved your domain controllers Windows Server 2019 or 2022, you need to review what is keeping you from upgrading.
Mitigating CVE-2022-37967
November 8, 2022 updates
The November updates also include a patch for CVE-2022-37967. KB5020805 details how to manage Kerberos protocol changes related to this vulnerability, and I strongly recommend that you review the steps provided there.
The patch adds Privileged Attribute Certificate (PAC) signatures to the Kerberos PAC buffer. A PAC is an extension to a Kerberos ticket that contains information about a user’s privileges. This information is added to Kerberos tickets by a domain controller when a user authenticates in an Active Directory domain. When the user then uses their Kerberos ticket to authenticate to other systems, the PAC can be read and used to determine their level of privileges without reaching out to the domain controller to query for that information.
PACs contain very sensitive information and therefore have been the target of multiple Active Directory attack techniques over the years. As a result, Microsoft is specifically adding additional protection and verification.
Sander Berkouwer recommends that after applying these updates on all your domain controllers, you work to identify areas that either are missing PAC signatures or have PAC signatures that fail validation through. To do so, enable Audit mode by running the following PowerShell command:
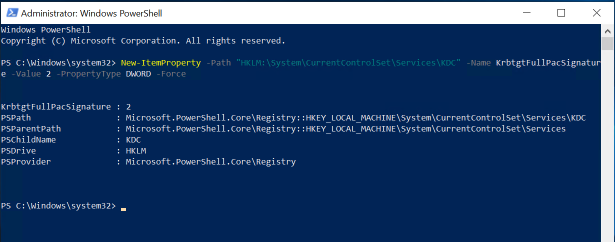
New-ItemProperty -Path “HKLM:\System\CurrentControlSet\Services\KDC” -Name KrbtgtFullPacSignature -Value 2 -PropertyType DWORD –Force
Then, he says, “monitor the System logs on the domain controllers to identify any issues with the Kerberos and Netlogon protocol changes.”
The November update is the first step in the process of rolling out enforcement of the additional security measures for Kerberos. It adds signatures to the Kerberos PAC buffer but does not check for signatures during authentication. Thus, secure mode is disabled for this initial period, because Microsoft knows that authentication will break unless organizations take steps to mitigate the side effects.
Accordingly, Microsoft will be rolling out updates over the next few months to provide additional Kerberos hardening. Let’s go through the timeline of planned changes and how they will impact you.
December 13, 2022 updates
The December security releases will move all domain controllers to Audit mode so that you can review the impact of enabling PAC enforcement.
Before moving to Enforcement mode, make sure that the domain functional level is set to 2008 or greater. The KB warns: “Moving to Enforcement mode with domains in the 2003 domain functional level may result in authentication failures.”
Be sure to note the following:
- Audit events will appear if your domain is not fully updated or if outstanding previously issued service tickets still exist in your domain.
- Continue to monitor for events that indicate either missing PAC signatures or validation failures of existing PAC signatures.
- After the entire domain is updated and all outstanding tickets have expired, the audit events should no longer appear. Then, you should be able to move to Enforcement mode with no failures.
April 11, 2023 updates
These updates will remove the ability to disable PAC signatures and add the KrbtgtFullPacSignature registry key.
July 11, 2023 updates
Next July’s update will modify the KrbtgtFullPacSignature registry key: It will remove the ability to set the value to 1 and move to Enforcement mode (value of 3). However, you will still be able to override that value.
October 10, 2023 updates
The October updates will remove the ability to disable PAC signature enforcement. All service tickets without PAC signatures will be denied authentication.
Conclusion
The security of Kerberos authentication is vital to any Active Directory environment. By being proactive about the mitigation measures described here, you can address critical Kerberos vulnerabilities that put your domain, and your business, at risk.



