
“Let no crisis go to waste.” This is the new mantra of every cyber criminal in the age of COVID-19. Around the globe, organizations are seeing an increase in phishing attempts that exploit our fear and desire for coronavirus information, including email traffic and malicious websites and images.
This blog post will review tips IT can give to their workforce as well as what IT can do directly to protect your organization from these exploits.
COVID-19 phishing and malware scams
COVID-19 is putting a strain on IT and infrastructure support teams around the globe. There’s no doubt you’re swamped supporting increased volumes of remote workers and ensuring that your back-end systems remain secure and available during this time.
This is also a time where security and infrastructure teams alike need to have a heightened awareness of cyber security attacks. It’s unfortunate, but cyber criminals are opportunistic and will look to exploit people’s fears, using the virus as a means for email phishing attempts. Bad actors are sending phishing emails containing links or attachments that claim to contain legitimate updates or information about the virus. Once opened, these infect the PC with malware that can be used to exploit the infected victim.
Many of these phishing scams appear like they are coming from the U.S. Centers for Disease Control or FROM YOUR VERY OWN ORGANIZATION (see below, example from U.S. Health and Human Services website).
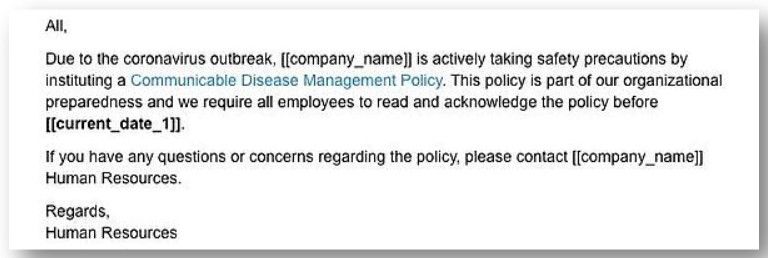
Refresher tips for your workforce
This is a good time to educate your employees about email phishing and remind them to be extra vigilant.
The first tip is vital: If you receive an email from a business or organization regarding updates on the COVID-19 virus, avoid clicking on any links and access the website directly.
Additionally, when reviewing emails remember to look for the following indicators of phishing attempts:
- Fake e-mail addresses: Be cautious when you see an email from a domain that isn’t familiar.
- Requests for personal information: Such as your Social Security number, credit card, or bank account number.
- Asking for payment: Solicitations that include a request for payment as part of an initial e-mail greeting, especially a request for Bitcoin, are likely phishing attempts.
- Prompts to download documents or files: Files may contain malware that captures keystrokes or mouse movements. Never download documents from any location unless you are certain the source is legitimate
Examples:
- A COVID-19 dashboard posing as if it were from Johns Hopkins but sends you elsewhere
- An email from your local bank with a link to activate a 0% financing loan (Don’t click the link, call or visit the merchant’s website)
- A government agency requesting personal information
Tips for IT to protect against coronavirus phishing attempts
Training and security awareness alone won’t completely address and block phishing attempts, but they will go far in lessening the organization’s overall susceptibility to these schemes.
I did a review of the Osterman Research whitepaper: Best practices for protecting against phishing, ransomware and other email fraud (sponsored by Quest) and pulled out some of the highlights.
- Remind—regularly–all employees, but especially senior executives who are more likely to be the target of a CEO Fraud/BEC attack, about the risks associated with oversharing information on social media, giving cybercriminals the opportunity to successfully target their prey.
- Establish “backchannels”, or out-of-band communication methods for any employee who deals with finances or sensitive data so that they can verify sensitive requests (e.g. a money transfer request from a CEO). This might be a number that can be used to send a text message or make a phone call even if the CEO is on vacation, or it could be a designated person in the office who can verify the CEO’s request.
- Keep software and operating systems up-to-date to reduce the potential for a known exploit to infect a system with malware. IT can help through management and enforcement on behalf of employees.
- Ensure that every employee maintains good endpoint defenses on their personal devices if there is any chance that these devices will access corporate resources like corporate email or databases with sensitive information. That includes employees’ personally owned computers and devices if they access corporate resources while traveling or at home.
- Use historical and real-time threat auditing and detection to reduce the potential for infection by protecting against access to domains that are known to have a poor reputation and so are more likely to be used by cybercriminals for phishing, ransomware, spear-phishing and other types of attack.
- Employ behavior analytics solutions to examine the normal behavior patterns of employees across an organization and, when a divergence is noted an exception is raised for further investigation or access is immediately blocked.
Michael Osterman lists many more details for the points above as well as additional approaches to reducing an organization’s susceptibility to phishing attempts in his whitepaper, which you can download here.



