A few months ago, while preparing for a presentation on this topic for The Experts Conference (TEC), my 8-year-old asked me what zero trust was. Using a recent trip to Ghana as an analogy, I explained that zero trust is similar to the security measures at home, such as locking doors and verifying someone’s identity at the gate before allowing access. When inside the house, there are certain rooms that guests are allowed in, while there are rooms restricted to close family members. These measures, at home, emphasize the need for organizations to similarly confirm identities and permissions at various stages before granting access. The same holds true when adopting a zero trust strategy.
The Maersk story
Before diving into this topic further, it is prudent to discuss why zero trust is so important. Many of you may remember the infamous NotPetya attack in June 2017. It was a destructive wiper malware targeting Windows systems and was attributed to state-sponsored actors. It caused significant global disruption by rapidly spreading and rendering computers unusable. Maersk, the world’s largest shipping company, suffered severe operational disruption with its IT infrastructure crippled, leading to massive shipping delays and a substantial revenue and recovery loss of $200 to $300 million. This highlighted major corporations’ vulnerability to cyber threats.
Having grown up in Ghana, experiencing disruptive power outages, I find it quite amusing that something that is a major headache to households and local businesses is what helped Maersk recover. According to Wired, during the attack, a lone server in Ghana, which was offline due to a power outage, served as the only clean backup. It was reported that a Ghanaian staffer met an employee in Nigeria to hand over the hard drive, which was then flown to London for restoration. This incident emphasizes the importance of building resilient systems to minimize the impact of cyber-attacks on organizations.
This article on zero trust will dive into core principles and practical strategies that organizations can use to enhance their resilience against cyber threats. It will help you develop a zero trust strategy and framework to avoid the predicament Maersk found itself in.
Understanding zero trust principles
The zero trust security model is a change in mindset which assumes there is a pervasive risk in any environment. Rather than assuming that everything behind the corporate firewall is safe, you need to treat every access attempt as if it is originating from an untrusted network. There is no single product that can be implemented to achieve zero trust. A search online shows that every software vendor has their own way of defining zero trust.
Fundamentally, it all boils down to making sure that the various enterprise resources, identities, endpoints and access paths your environment are all secured, that there are checks in place to make sure the right people are accessing only the information they are allowed to access and that they are doing so from the right devices. Microsoft describes zero trust by these three main principles:
- Verify explicitly – with every access attempt, authorize and authenticate using every data available to ensure the right identity accesses a resource.
- Use least privilege access – limit user access by implementing controls to give them Just-in-Time or Just-Enough (JIT/JEA) access to the resource.
- Assume breach – assume that you have already been compromised, so use network segmentation to reduce the impact and use analytics for visibility into your environment.
The NIST Zero Trust Architecture
The National Institute of Standards and Technology, NIST, has defined certain principles that need to be present to achieve zero trust.
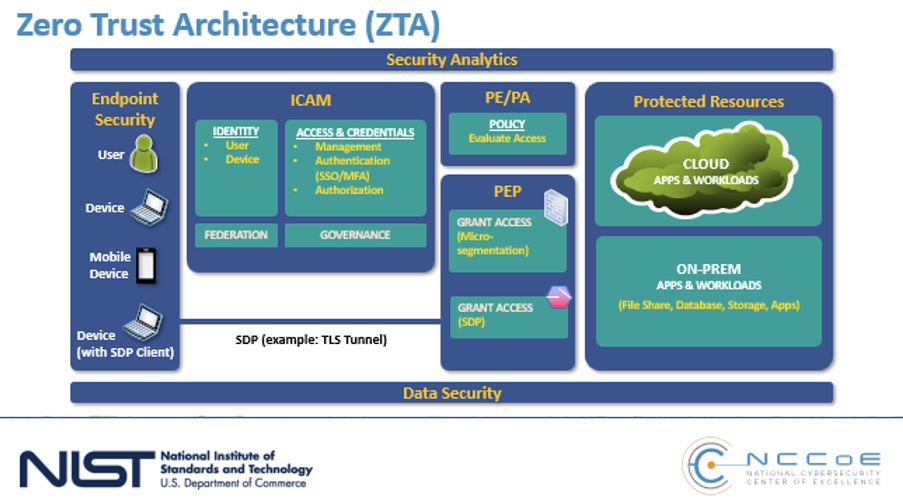
Figure 1: NIST Zero Trust Architecture reference: aka.ms/MCRA
In this graphical representation of the NIST Zero Trust Architecture, when an untrusted endpoint (human or device) needs to access the trusted or protected resource(s) – either on-premises or in the cloud – the following is needed:
- An Identity, Credential and Access Management system to authenticate and authorize the identity.
- A Policy Engine/Policy Administrator to evaluate access. Below that is the Policy Enforcement Point, which should be placed at the access points of each application and data sources to ensure Zero Trust policies are applied.
- Security Analytics and Data Security tools deployed for end-to-end monitoring. Security analytics tools are your SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation and Response) tools for threat intelligence and activity logging, while the data security tools protect the organization’s data and files.
Microsoft’s pillars of a zero trust architecture
Building on the NIST framework, Microsoft classifies zero trust into these six pillars:
- Identities – This is the foundation of zero trust, as it is the primary conduit by which resources in your organization can be accessed. It represents both human and non-human identities such as people, services and IoT devices.
- Devices – These refer to both corporate and personal endpoints. When an identity has access to a resource, any device that identity uses also has access to the data. For example, data from an on-premises resource to cloud environments or from personal devices to corporate devices. This variety in the number of devices increases the attack surface area.
- Applications – These include APIs and could be modern SaaS applications or legacy on-premises applications. This is the interface for consuming data, and thus needs to be monitored.
- Data – This is every organization’s information that needs to be protected through classification, labeling and encryption.
- Infrastructure – These are the on-premises servers or VMs in the cloud, such as IaaS (Infrastructure as a Service) or PaaS (Platform as a Service) resources.
- Network – This is the channel through which data is accessed. Networks should be encrypted and segmented to prevent attackers from intercepting the data over it and from moving laterally across it.
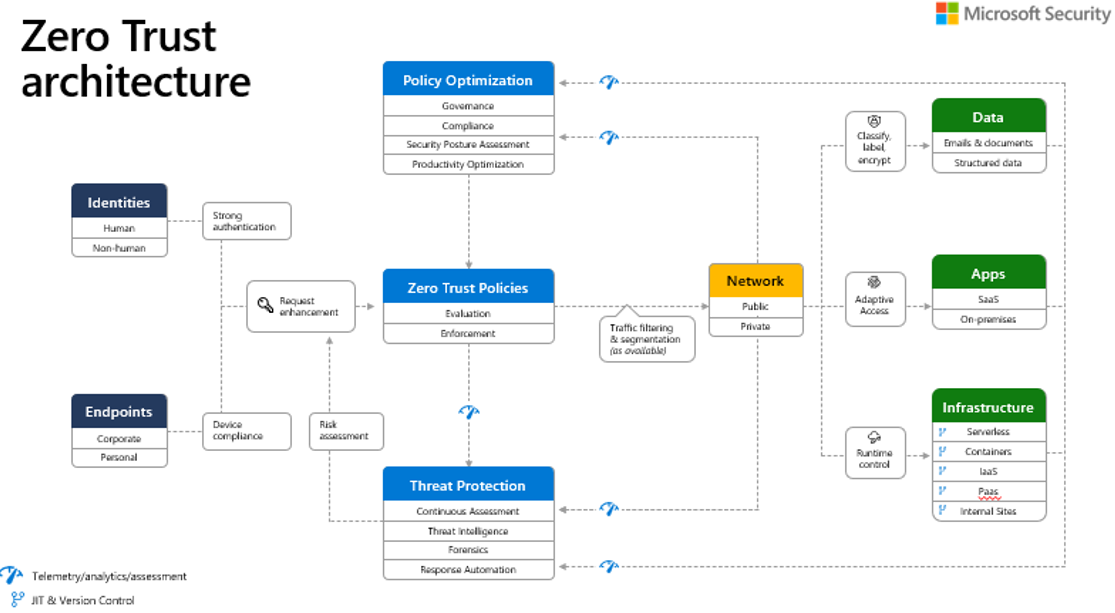
Figure 2: Microsoft’s Zero Trust architecture
This simplified view of Microsoft’s Zero Trust architecture shows the six pillars and, for each of them, what needs to be enforced and collected. For example, for Identities, strong authentication must be ensured, while for endpoints, device compliance with security controls should be verified.
Similar to the NIST architecture, the diagram shows the critical points where you integrate policy enforcement and automation, threat intelligence and threat protection across the pillars. With the data classified, labeled and encrypted, the policy optimization tools consume signals, such as the sensitivity of the data, and sends those signals to the policy engine. As a result, before granting or denying access, the Zero Trust policy engine takes in the request and verifies signals from all the six pillars based on the policy configuration and least privileged access enforcement. The telemetry, analytics and assessment signals from the pillars are then fed back into the policy optimization and threat protection systems to enhance future requests.
Practical steps for creating a zero trust strategy
Having established the foundation of zero trust, we will now break down the strategy into the following simple practical steps:-
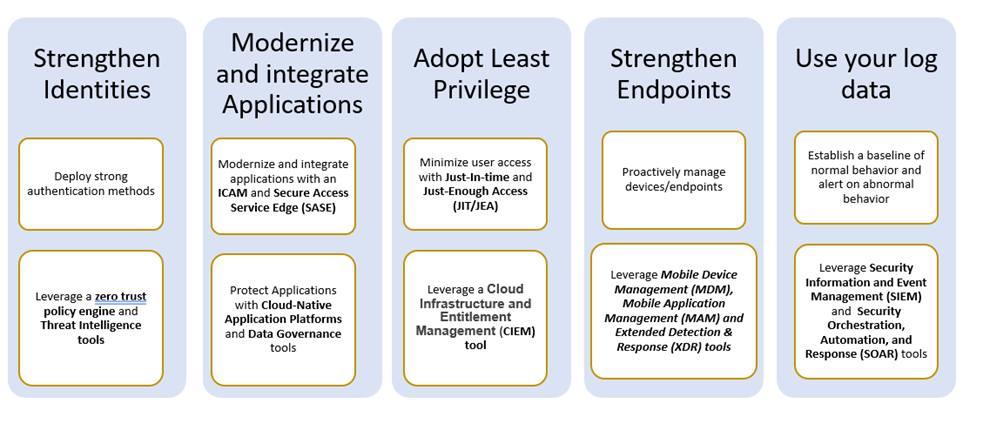
1. Strengthen Identities
For strengthening identities, deploy strong authentication methods that integrate seamlessly with your Identity, Credential and Access Management (ICAM) system, establish policies for the zero-trust engine to enforce and leverage threat intelligence tools.
The human and/or non-human identities are the channel by which resources are accessed in your organization, therefore it is important that they are secured. As we know, passwords alone are bad, so moving towards more secure authentication methods like requiring multi-factor authentication (MFA) or deploying passwordless methods gives users a higher level of security. It also ties into the principle of verifying explicitly, because you now have a greater assurance that your users’ authentications are legitimate. Some of the common factors of MFA are:
- Something the user knows, such as a pin or a password
- Something the user has, which could be a physical device like a smartphone, a security token, FIDO2 key or smart card
- Something the user is, including biometric data such as fingerprints, facial recognition or iris scans
The use of any combination of these factors strengthens the identities accessing resources. The choice of the right combination will depend on several factors such as cost of implementation and the type of users in your organization.
Passwordless authentication methods differ from MFA methods as they do not require the knowledge of a memorized secret and typically require a public key cryptography infrastructure. During registration to the authentication provider, the public key is provided and the private key is stored on the users’ device. This type of authentication method uses a combination of something the user is (biometric data) and something the user has (physical device). Because Passwordless authentication eliminates the use of passwords, there is no need to worry about frequent password changes, password reuse or the risk of weak passwords which could compromise your environment.
It is imperative that the organization chooses an authentication method that integrates seamlessly with their Identity, Credential and Access Management (ICAM) system. Referencing the NIST architecture, there should be a “zero trust policy engine” which takes in requests, verifies signals from different sources and enforces controls that have been previously configured by an administrator. An example of organization controls could be to only allow users with Windows 11 devices or iPhone devices to log into the system. Some of the signals the policy engine should verify are:
- The location of the request coming in. This is essential for blocking any users logging in from countries your organization does not conduct business in.
- The type of device the user is logging in from.
- How likely it is that the sign-in has been compromised based on failed password attempts.
The engine should also use machine learning to detect and respond to any potential identity risks, such as unusual sign-in activities or compromised credentials, and provide organizations with real-time risk assessments and automated responses in situations where risky behaviors like password spray attacks are detected. This can be achieved by integrating the policy engine with threat intelligence tools to enable proactive management and mitigation of potential threats to users’ identities. Strengthening the identities provides the checks and balances that will make the environment more resilient against threats and ensures that only legitimate users gain access to sensitive information or resources.
2. Modernize and integrate applications
Modernize and integrate on-premises legacy applications and SaaS applications with a Cloud Identity Provider. Leverage Secure Access Service Edge (SASE), Cloud-Native Application Protection Platform (CNAPP) tools to secure applications and data governance tools to secure the data.
As mentioned earlier, applications are the interface by which data in organizations are consumed, so they need to be secured. These applications could be legacy on-premises or SaaS applications. Applications that use legacy protocols such as Kerberos, LDAP or Radius do not support MFA and can be easily compromised because of their incompatibility with modern security tools. As a result, they should be updated to modern authentication protocols such as OIDC, OAuth2 or SAML. After the applications have been modernized, ensure they can integrate seamlessly with the ICAM system you own. Seamless integration with the ICAM system provides users with a Single Sign-On experience, a uniform login experience for all applications, an automated user provisioning and deprovisioning, MFA capabilities as well as audit and reporting of user activities.
While working to modernize your legacy applications, a good transition strategy is to publish the applications via reverse proxy and federate it to the ICAM system. This will allow users to access the on-premises legacy applications through a remote client, which will provide them with all the security benefits of the Cloud Identity provider, such as MFA.
In 1999, Gartner coined a new term, SASE (Secure Access Service Edge), in their publication “The Future of Network Security in the Cloud.” SASE combines “Network as a Service” with “Security as a Service.” In other words, it integrates network security functions with cloud capabilities such as “Software Defined Wide Area Network (SD-WAN) and Zero Trust Network Access (ZTNA)”. SASE works from the principle of assuming breach and enables network segmentation. Integrating with a SASE provides secure access to the internet based on identity or device, and therefore can be used to provide or deny access to SaaS applications based on these conditions.
In addition to a SASE, Cloud-Native Application Protection Platforms (CNAPP) can be used to protect applications. It enhances the security of applications using advanced threat protection features and pro-active real-time security monitoring to detect threats and enable efficient incident response.
Finally, leverage a data governance tool to protect and manage the data handled by these applications. The tool provides a central hub to find, understand, govern and prevent data loss through compliance rules and uses artificial intelligence to give valuable insights to your security teams. For sensitive data in the applications, the organization can create checks and balances to prevent or allow views and downloads. Modernizing applications to run on the latest protocols and effective application management will ensure that crucial data is protected in your organization.
3. Adopt least privilege
For adopting least privilege, minimize user access with Just-In-time and Just-Enough Access (JIT/JEA) controls.
Adopting least privilege is one of the zero trust principles. This is about ensuring that users do not have long-standing permissions and that the right people have just enough access at the right time to data applications and infrastructure. In this step, Privileged Identity Management (PIM) and Privileged Access Management (PAM) solutions should be integrated with your organization’s overall IAM strategy. Here are a few recommendations for this step:
- Adopt a proactive approach where you apply this principle consistently across all your systems.
- Assign users the least permissions to do their day-to-day tasks and only allow them to elevate their permissions (JIT) when they need to perform privileged tasks.
- If required, use a solution that enables administrators to create workflows for approval from managers before permissions are elevated.
- Regularly review privileges to ensure that only the right people still have the right access and revoke access for users whose roles have changed.
- Send alerts about any changes in administrator assignments, audit and report all activity.
Most organizations currently have a multi-cloud infrastructure, which means that as the number of identities and permissions accessing this environment continues to grow, so does the risk they pose to the organization’s infrastructure. The risk is because there is inadequate granular visibility into the identities, permissions and resources across the entire infrastructure. In addition, every cloud infrastructure has its own access control operating model, which makes it difficult and very time-consuming for administrators to implement consistent security policies across cloud platforms. In such environments, several permissions are granted but not used.
This is where organizations need a CIEM (Cloud Infrastructure and Entitlement Management) solution: to provide a single view of all the permissions that have been assigned to the human and non-human identities in the different cloud infrastructures. With this data, administrators can easily identify areas of “permissions creep” where they can reduce risks related to the principle of least permissions.
4. Strengthen endpoints
For strengthening endpoints, implement a good device management strategy and leverage Mobile Device Management (MDM), Mobile Application Management (MAM) and Extended Detection and Response (XDR) tools.
With digital transformation, several endpoints and devices such as laptops, BYOD (Bring Your Own Devices), printers, mobile phones, virtual machines and IoT devices are used to access organizations’ resources. As a result, it is important that devices are constantly evaluated for their security posture using several endpoint hardening techniques such as firewall protection, patch management, antivirus software and device encryption.
A good device management strategy allows organizations to centrally manage virtual and physical devices, provide an inventory of all devices in their environment and create a policy to ensure that devices on their network are running the approved versions of operating systems (OS). This ensures that only known devices can access resources and that all devices have the latest OS patches with no known vulnerability to attacks. This in turn enhances your organization’s overall security posture. The strategy should comprise the following:
- An MDM strategy, which enables organizations to manage, monitor and secure mobile devices that will be accessing data in the environment. This enables IT administrators to monitor the health of devices, have an inventory of all devices so that their usage can be monitored, identify potential risks and enforce security policies such as encryption and remote wipe capabilities to protect data in case of device loss or theft.
- A MAM strategy, which focuses specifically on the management and security of mobile applications on mobile devices rather than the entire device. This is where administrators enforce organization policies such as application usage, ensuring compliance and data protection, monitoring of applications to gain insights and controlled deployment of applications to mobile devices.
- A combination of an MDM and MAM strategy.
MAM is centered around managing and securing mobile applications and their data while MDM extends to management of the entire device, such as settings and configurations.
In addition to a device management strategy, implementing an Extended Detection and Response (XDR) solution is essential for securing endpoints. An XDR analyzes data from multiple security products to detect and respond to threats across different vectors. It incorporates insights from networks, endpoints and emails among others, using machine learning and AI to provide a more holistic and proactive approach to threat detection and mitigation. It works from the principle of “assume breach” by analyzing anything that it deems suspicious and creating an alert in the system for security teams to investigate and remediate. It also proactively discovers misconfigurations in endpoints and isolates any untrusted documents to a container away from your entire network.
Strengthening endpoints is vital for the overall integrity of a network, as compromised endpoints can be potential entry points for attackers.
5. Use your log data
Establish a baseline of normal behavior and integrate with SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) tools for quick detection of anomalies.
For any enterprise, the amount of data that is received daily can be overwhelming. After a month, it is almost impossible to dig through all the data, especially if you do not know what you are looking for. That is why it is important to establish a baseline of what is normal in your environment to enable you to detect anomalies quickly. With a baseline, you can then create playbooks to send alerts when deviations are detected. Also, because you cannot solve all problems immediately, it is essential that you prioritize your most sensitive assets. A simple way to prioritize assets and calculate your risk exposure is to first determine how critical the assets are to your business, how likely it is that the data can be compromised and what that impact will mean for your business.
Ensure that the log files from the Identity provider can be exported into a SIEM solution for further analysis and integrated with a SOAR to remediate incidents rapidly. The SIEM and SOAR systems should provide a portal that shows administrators a view across the entire enterprise of your organization’s security and insights and confers the ability to detect and remediate incidents rapidly using built-in orchestration. Data from all the pillars (users, devices, applications etc.) from the multiple clouds and on-premises devices should be displayed in one view to make it easier for administrators to investigate any incidents. Timely detection of anomalies will help control the overall damage in case of an attack.
Conclusion
Bringing everything full circle, these are practical projects you can implement in your organizations to secure a zero trust environment and create a zero trust strategy. The five main steps described are: strengthening your identities, integrating your applications with your preferred identity solution, adopting a least privileged access principle in your environment, strengthening your endpoints and reviewing your log data. To simplify this for your team, pick one of these steps and focus on implementing the strategies for that step first and then move on to another step. In each of the steps, ensure that the chosen solution integrates seamlessly with your ICAM system to ensure a holistic implementation and avoid security gaps and implementation costs.