NIST CSF 2.0 is the upcoming revision to the Cybersecurity Framework (CSF) from the U.S. National Institute of Standards and Technology (NIST). It currently exists as a draft published on August 8, 2023, which is available for public comment until November 4, 2023. The final CSF 2.0 is scheduled to be published in early 2024.
In this post, we will review the key elements of the original framework and dive into all the details you need to know about what’s coming in NIST CSF 2.0. (Note that this post is based on the public draft of NIST 2.0 released August 8, 2023.)
What is the NIST CSF and how is it used?
NIST CSF is a voluntary framework designed to help organizations understand, assess, prioritize and communicate about their cybersecurity risks. It was created in response to a 2013 Executive Order that tasked NIST to work with the private sector to design a cybersecurity framework for managing cyber risk.
The resulting framework provides guidance based on established standards and best practices. It helps organizations assess their current cybersecurity practices and identify effective steps to take to improve cybersecurity and cyber resilience.
The NIST Cybersecurity Framework has three primary components:
- Core — The Core details a set of desired cybersecurity outcomes. These are organized into Functions, which are further divided into Categories and Subcategories. Note that the CSF does not mandate how to achieve the outcomes, which gives organizations the flexibility to implement the controls that meet its unique needs. It also enables the framework to remain relevant as technology advances and new cybersecurity tools and techniques become available.
- Tiers — Tiers help organizations assess how well their current cybersecurity risk management practices achieve the outcomes defined in the CSF. There are four tiers: Adaptive, Informed, Repeatable and Adaptive. Tiers do not necessarily represent maturity levels; organizations should determine their desired tier based on their goals, risk tolerance, skillset and budget.
- Profiles — Profiles provide organizations with a way of optimizing the CSF to best serve their unique needs. In particular, they can create a “Current” profile by mapping their cybersecurity requirements, objectives, methodologies and current practices against the outcomes detailed in the Core, and then detail their desired state in a “Target” profile. By performing a gap analysis between the two profiles, they can identify opportunities for improving their cybersecurity posture, prioritize them, estimate costs, and create a targeted action plan.
What are the key changes in NIST CSF 2.0?
NIST CSF 2.0 shares the same goals as the current CSF 1.1, but the framework has been refined based upon extensive feedback from public and private sector organizations over the past decade.
Specifically, the draft document includes the following major changes:
- An expanded scope
- The addition of a sixth function in the Core
- Expanded guidance around profiles
Let’s dive into the details of each of these changes.
Expanded scope
The original CSF was targeted toward securing U.S. critical infrastructure. However, the framework has been adopted far more widely and is now used by organizations across a broad range of sectors, both public and private, all around the world.
NIST CSF 2.0 has been updated to reflect this broad usage. For starters, the title has been shorted from the original “Framework for Improving Critical Infrastructure Cybersecurity” to simply “Cybersecurity Framework.” The draft also explicitly states that its guidance can be used by any organization, regardless of its size, sector or maturity.
NIST CSF 2.0 also provides increased guidance to help organizations adapt the framework to their unique needs. In particular, the implementation examples for the objectives laid out in the Framework Core are being updated to be relevant and useful to organizations beyond those concerned with U.S. critical infrastructure. A particular focus is enabling smaller businesses to use the framework more effectively. These examples are published in a discussion draft that complements the NIST CSF 2.0 draft document.
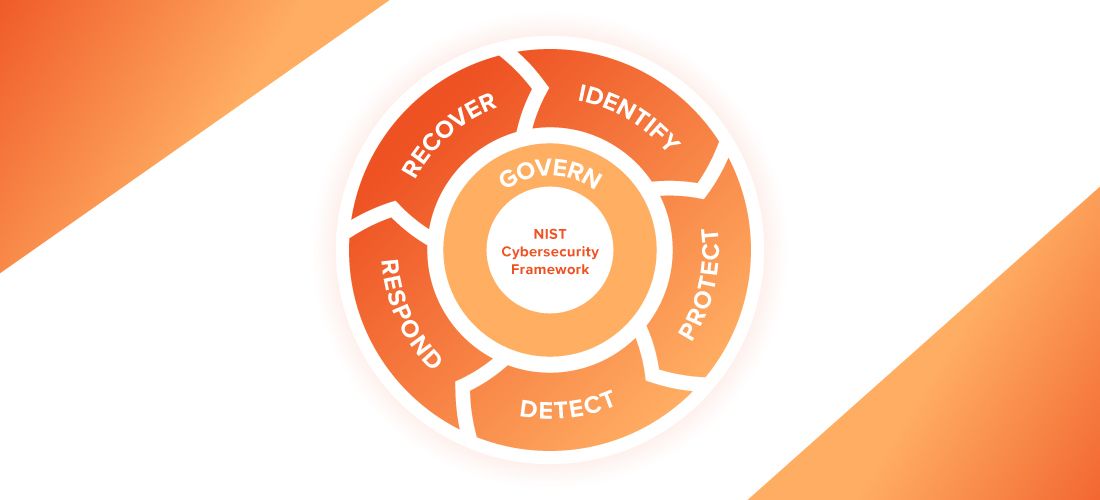
Changes to the core functions and the new function, Govern
The original CSF specified five functions (often called “pillars”): Identify, Protect, Detect, Respond and Recover. These functions were divided into 23 categories and 108 subcategories.
NIST CSF 2.0 includes these five pillars but introduces a sixth: Govern. Governance-related outcomes were removed from the original five functions to create this new cross-cutting function. The Govern function help an organization prioritize and achieve the outcomes specified in the five other functions.
It’s important to understand that the functions are not ordered steps, nor are they one-time tasks. Rather, they are core cybersecurity competencies that work together to provide a comprehensive lifecycle for managing cybersecurity risk over time. Accordingly, the functions should all be addressed concurrently.
Many IT pros are familiar with the original five categories and have been using them to structure their cybersecurity strategy for years. However, it’s worth reviewing how they have changed in NIST CSF 2.0, along with explaining the new Govern function.
Identify
Under the draft NIST CSF 2.0, this function now comprises three core goals for organizations: identifying their assets (from hardware, software, services to data to facilities and people); understanding the cybersecurity risks to the organization, its assets and individuals; and identifying improvements to its cybersecurity risk management processes, procedures and activities.
Multiple categories under the Identify in the original framework have been moved to the new Govern function, including Business Environment, Risk Management Strategy and Supply Chain Risk Management.
Protect
The Protect function covers a range of safeguards for preventing or reducing cybersecurity risk. They include managing identities and their access rights, requiring authentication, protecting data, securing platforms and ensuring infrastructure resilience, as well as promoting cybersecurity awareness among users.
The big change to this function is primarily a consolidation of the categories within it in the original CSF.
Detect
The Detect function covers the timely discovery and analysis of anomalous activity, indicators of compromise (IoCs) and other events that could indicate a cybersecurity threat in progress.
As with the Identify function, the key change to the Detect pillar in NIST CSF 2.0 is consolidating the existing categories to improve clarity and usefulness.
Respond
The Respond pillar addresses the need to take effective action when a threat is detected in order to prevent it from spreading, contain its impact and report the relevant information to the proper stakeholders.
Two of the original categories from the original framework are modified in NIST CSF 2.0. One of them (Response Planning) has been consolidated into another Respond category, and the other (Improvements) has been shifted to the Identify function.
Recover
The Recover function is focused on ensuring you can promptly recover the assets and operations impacted by a security incident. It also covers communication during recovery efforts.
As with the Respond function, the Improvements category of the Recovery pillar has been shifted to the Identify function.
Govern
Now, let’s turn to the new pillar: Govern. It is a foundational function that informs and supports the other five pillars of the framework. Its purpose is to help organization establish and monitor their cybersecurity risk management strategy, expectations and policies.
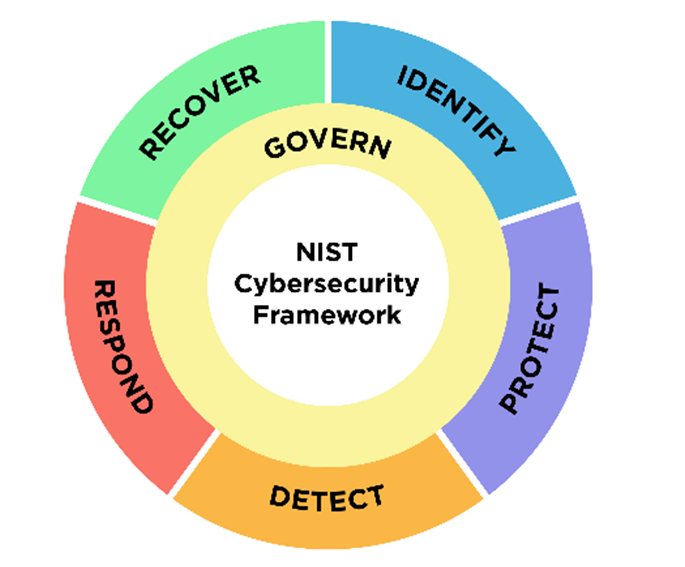
As noted above, Govern includes some outcomes that were previously under the Identify function. Some of them have been renamed. These Govern categories are Organizational Context; Risk Management Strategy; Cybersecurity Supply Chain Risk Management; and Roles, Responsibilities, and Authorities. The Govern function also features one new category, Oversight, which covers using the results of cybersecurity risk management activities to inform and improve the broader risk management strategy.
However, this list of categories does not do justice to the new Govern pillar. Although the original framework contained disparate guidance on governance scattered across its five pillars, NIST CSF 2.0 elevates and expands on the importance of governance. It emphasizes that cybersecurity is a major source of enterprise risk that should be considered by senior leadership as ranking right alongside legal, financial and other risks. It covers processes for establishing, communicating and evaluating a cyber risk management strategy, including identifying roles and responsibilities. It also addresses the need to maintain appropriate processes, procedures and policies for managing cybersecurity risk.
In short, the goal of the pillar is to help organizations establish and oversee a cybersecurity strategy that aligns with their mission and risk tolerance.
A good example is how NIST CSF 2.0 covers supply chain risk management. While this topic appeared in the original framework, it was under the Identify function. In moving it to Govern, the revised framework adds key outcomes, such as ensuring that suppliers are known and prioritized by criticality, performing due diligence before entering into supply chain relationships, and including provisions for activities that occur after the conclusion of a partnership or service agreement. Moreover, the category now recognizes that supply chain security practices must be integrated into the organization’s cybersecurity and risk management programs.

Reduce your AD attack surface.
Expanded guidance around profiles
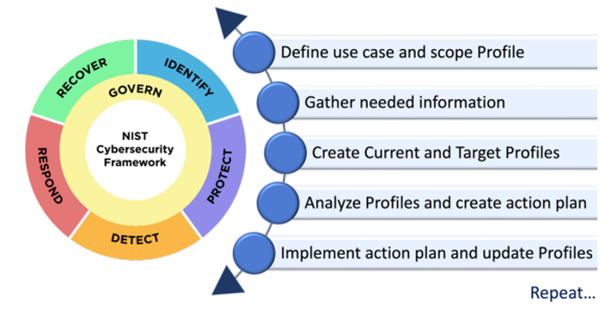
As noted earlier, profiles help organizations understand how closely their current cybersecurity objectives and practices map to the outcomes detailed in the framework’s functions, as well as lay out their desired state to identify gaps and create an effective plan for reaching their goal.
However, over the years, the cybersecurity community has requested that NIST provide more assistance in using profiles. NIST CSF 2.0 delivers that help. The guidance around profiles has been significantly revised and expanded, with many examples of ways to use profiles, as well as detailed steps for creating and using them (as illustrated in the figure below). In addition, Appendix A provides a notional template that organizations can use to create a profile, along with a list of additional elements that could be included in a profile. It also offers an excerpt of a notional action plan template, which organizations can customize to meet their needs.
Conclusion
For years, the NIST Cybersecurity Framework has been a powerful tool that organizations around the world rely upon to understand and improve their cybersecurity posture. NIST CSF 2.0 offers significant refinements and enhancements that will serve organizations even more effectively on their ongoing cybersecurity journey.