Software supply chain security is top of mind for organizations of all sizes and types today, and for good reason. Not only are high-profile supply chain breaches regularly in the headlines, these attacks show no signs of slowing down. In fact, Gartner estimates that by 2025, 45% of organizations worldwide will have suffered attacks on their software supply chains — a threefold increase from 2020.
But what exactly is a software supply chain and what puts its security at risk? And what best practices can organizations implement to improve their software supply chain security? This article answers all those questions and more.
What is a software supply chain?
Software supply chain security is the process of securing the components, activities and practices that are involved in the creation and deployment of software — the software supply chain.
The software supply chain includes anything that plays a role in the development of an application or plays a role during the software development lifecycle (SDLC). Examples include third-party and proprietary code, open-source libraries and tools, deployment methods and infrastructure, interfaces and protocols, and developer practices and development tools.
Accordingly, strengthening the security of your software supply chain is a challenging task that requires cooperation from multiple stakeholders.
Why software supply chain security is important
Software supply chain security is vital for virtually every organization, regardless of location, size or sector. After all, just about every organization today relies on computing and therefore on a wide variety of software suppliers and service providers. In fact, one study finds that the average small business uses 172 apps, mid-market organizations have 255, and large enterprises use an average of 664 apps. Another study reports that organizations use an average of 130 software as a service (SaaS) applications alone!
And that’s just the tip of the iceberg — you also have to consider all of the components that feed into those tools and services. Any weakness that’s exploited in the supply chain could result in a costly security incident for you.
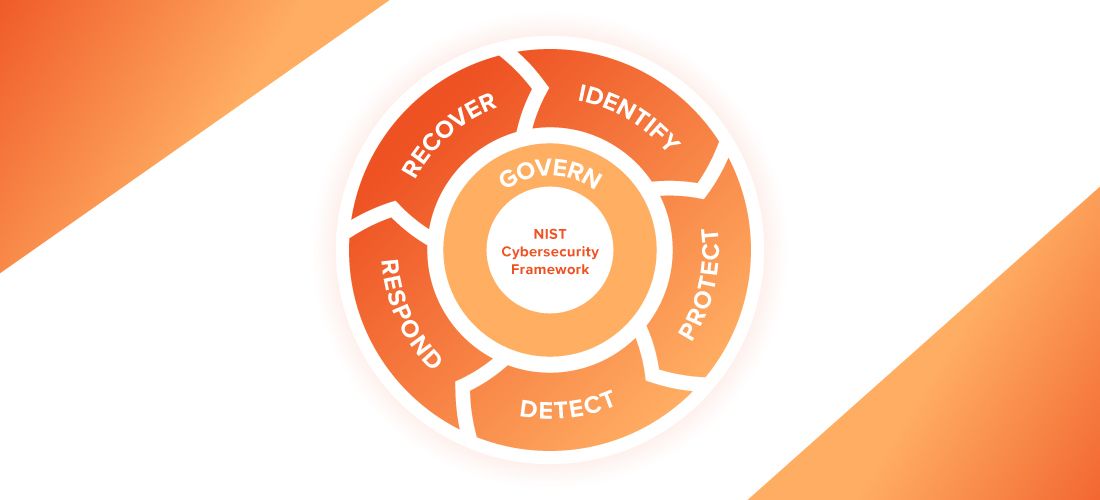
Moreover, many organizations today are subject to a variety of regulatory mandates and industry regulations, such as GDPR, NIS 2 and CCPA, or are required to apply an approved cybersecurity risk framework (CSF) like the NIST CSF or ISO/IEC 27001 and 27002. These standards often require a robust and well-defined strategy for securing the software supply chain.
Indeed, governments across the globe are stepping up to lead the charge to improve software supply chain security. One recent example is the secure-by-design development principles created by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), NSA and FBI, in partnership with security agencies from Australia, Canada, the UK and other countries. These principles are based on the idea that cybersecurity needs to be built into the design and manufacture of technology products.
NIST SP 800-161r1 lists a wide range of damage that organizations could suffer from a weakness in their software supply chain security, including:
- Theft of intellectual property results in loss of a major competitive advantage.
- A data breach leads to loss of valuable government contracts.
- A data breach at a government agency has ramifications for national security.
- Production of counterfeit products erodes customer trust and confidence.
What threats put software supply chain security at risk?
Software supply chain security is threatened by attacks in which adversaries compromise one of the elements of the software supply chain in order to compromise other elements of the supply chain that depend upon it. For example, hackers might insert malicious code in an open-source library that is used by popular software applications, undermine code-signing processes, or alter a fix or update that a vendor is issuing for its software product.
One of the most infamous breaches of software supply chain security involved SolarWinds Orion, a widely used IT monitoring platform. Suspected nation-state hackers managed to compromise the SolarWinds network and insert malicious code into the Orion software, which was distributed to SolarWinds customers. As a result, hackers were able to gain access to vast amounts of sensitive data and systems at 18,000 private organizations like Microsoft, Intel and Cisco, as well as government agencies like the U.S. departments of Homeland Security, State, Commerce and Treasury. But the breach has even larger potential ramifications: With the information gleaned about those SolarWinds customers, the hackers might have been able to compromise their customers and partners as well.
Systems like Orion are valuable targets for software supply chain security attacks because they require privileged access to IT systems. Consider Okta, an identity management platform that thousands of organizations use to manage employee access to applications and devices. The company has reported not just one but several supply chain incidents. They include the compromise of code repositories for its authentication service Auth0; use of Okta credentials to target messaging app Signal and bypass multifactor authentication (MFA); and a breach of its vendor Rightway Healthcare that exposed the personal and healthcare data of some 5,000 Okta employees.
What’s required for strong software supply chain security?
It might seem that achieving compliance with today’s strict data protection mandates or gaining certification with an approved secure software development framework (SSDF) would suffice for strong software supply chain security. But while compliance with established standards provides a critical foundation for securing you supply chain, should not be viewed as a finish line.
That’s because compliance or certification ensures you meet a minimum security threshold, but it does not necessarily equate to robust protection. Moreover, these standards are created with a broad brush, meant to serve a wide range of organizations and situations. They may not fully cover the unique risks, threats or complexities your organization faces.
For strong software supply chain security, your organization must go beyond compliance. It requires comprehensive supply chain risk management as part of a broader cyber risk management strategy. Tailoring a security strategy to your specific needs, proactively addressing your unique vulnerabilities and threats, and continuously updating your security posture are crucial to comprehensive protection against today’s rapidly evolving cyber threats.
Best practices for improving software supply chain security
Securing your software supply chain requires looking at all the steps involved. Here are the key areas to consider:
- Source code
- Third-party code that gets included in the build
- Build pipelines and infrastructure
- Artifacts created by the build pipeline
- Deployment to production
The preceding four areas are critical for any organization that creates software, whether for internal use or for the market, which includes most organizations. However, the final bullet applies to virtually every business, regardless of size or industry.
Let’s review the top best practices for improving software supply chain security in each of these areas.
Source code
Source code is the foundation of your software. If compromised, it can lead to vulnerabilities in the software itself. The following best practices can improve software supply chain security in this area:
- Make sure developers are trained yearly on secure coding best practices.
- Rigorously adhere to the principle of least privilege for developers — as well as all processes and agents accessing the source code. For example, enable MFA and use both client-side and service-side certificates to perform mutual authentication between systems.
- Make sure that no credentials are committed to the repository for any reason. Examples include SSH keys, API keys and access tokens. It’s best to scan periodically to identify and remove any that were accidentally committed.
- Build checks into your software configuration management process to prevent unauthorized data from being injected into the code base.
- Perform both dynamic and static application security testing on each build.
- Require at least two people to review each commit.
- Require use of short-lived access tokens to interact with source code.
Third-party code
Third-party code that gets included in the build is a potential weak point that is too often overlooked. Attackers focus a good deal of energy looking for vulnerabilities in open-source libraries and other third-party software that they can exploit, because this code is used in a wide range of commercial solutions, in-house tools and other software.
To secure this aspect of the software supply chain, follow these best practices:
- Validate code through checksums and cryptographic signatures.
- Leverage software composition analysis (SCA) software to detect vulnerabilities.
- Require a detailed software bill of materials (SBOM) and review it carefully.
- Build from source code whenever possible.
- Validate package managers and repositories to prevent unintentional packages from being included due to dependency confusion, typo squatting and other means.
- Keep all third-party code current with the latest security updates.
Build pipelines and infrastructure
Build pipelines are where the software gets its shape. A flaw in the infrastructure can open the door to serious issues like data leaks or unauthorized access. The best practices below will help you improve software supply chain security in this area:
- Assign each component in the build pipeline a single responsibility so that least privilege can be properly applied.
- Clearly define and document all input and output parameters.
- Ensure that the pipeline produces immutable artifacts that are stored in a secure location.
- Run the pipeline orchestrator separately from the processes that perform the actual build.
- Ensure that build agents are single use and that they write directly to storage using short-lived credentials that are rotated automatically.
- Create a repeatable build environment using best practices like documenting the environment thoroughly and automating setup.
- Ensure the environment has minimal or no internet connectivity.
- Monitor the environment for suspicious activity. In particular, periodically run an up-to-date security scanning tool to look for indicators of compromise (IaCs).
Build artifacts
The set of artifacts created by the build pipeline is what actually gets deployed. If they are tampered with, they can cause software malfunctions or become a point of entry for attacks. To improve software supply chain security in this area, use these best practices:
- Require signing for each intermediate stage as well as for the final product. During the final build, verify earlier components before they are added.
- Limit access to artifacts to what is needed for the shortest duration possible. Do not allow accounts that have unlimited access and infinite duration.
- Be prepared to rotate and revoke access to keys.
- Store artifacts in immutable storage so it’s impossible for anyone to tamper with them.
- Perform rigorous unit, functional and end-to-end testing.
- Complete both static application security tests (SASTs) and dynamic application security tests (DASTs).
- Publish code with verifiable signatures, hashes or both, along with a detailed software bill of materials (SBOM).
Production deployment
Code becomes accessible to users only after it is deployed to a production environment. Accordingly, software supply chain security also requires ensuring that your production environment is secure. The following best practices can help:
- Perform penetration testing of your environment. This step will provide the biggest bang for your buck.
- Apply any runtime security controls from the standards, certifications and frameworks relevant to your business.
- When deploying new software or updates, verify the SBOM and make sure signatures and hashes match.
- Validate on both first install and all updates that third-party vendors applied all the security standards you require.
- Ensure that your configurations are secure by design and follow the principle of least privilege.
- Validate that all your containers and operating systems have minimal components installed and are automatically kept up to date.
- Monitor for configuration drift and quickly roll back any unwarranted changes.
- Monitor for suspicious activity. In particular, closely audit your identity management system, which stores identity and privilege information and provides vital authentication and authorization services. For most organizations, that means ensuring robust Active Directory auditing.
Best practices for evaluating software vendors
More broadly, software supply chain security requires carefully evaluating the security practices of all of your third-party vendors. Here are some questions that can help:
- What strategies do you use for securing the software supply chain?
- What is your supply chain risk management process? Exactly how do you ensure your software is free from malware or other malicious code?
- What security standards does your company follow? Have you achieved certifications with ISO 27001/27002, SOC 2, HITRUST or other standards?
- In what countries is the software developed and built? Is there any foreign ownership, control or influence?
- Do you use an air gap architecture that provides physical separation of your software development environment in a secure facility, along with best practices like separation of duties and robust threat mitigation controls?
- Do you provide a data sheet that includes information about the software itself, the tools and technologies used to build the software, security standards and controls, and the tools and processes that govern the software?
- Do you publish a detailed software bill of materials with hashes or signatures?
- Do you provide notification about any modifications to your service level agreement (SLA) or changes to your software, so we can analyze how they impact our supply chain?
Conclusion
Software supply chain security isn’t just a best practice; it’s an imperative for all organizations today. A single breach in your supply chain can lead to catastrophic consequences, including extended downtime, massive data loss, and lasting damage to your brand and reputation.
Don’t wait for a disaster. Start securing your software supply chain today.