Recently I was giving a presentation and a slide was included that happened to show a 100% identity secure score. It wasn’t part of the presentation, but it stopped the show, and I was peppered with questions about whether it was real and in production. The answer to both questions is yes.
I’ll start by explaining that I work for an IT firm. Our philosophy is that we should be more secure than our clients. For this reason, perhaps my staff is a bit more tolerant when it comes to security restrictions because they know what’s at stake. But the reality is that we do roll our settings out to our clients. We go first, so they don’t have to live on the bleeding edge, but once everything is settled, the new setting becomes part of our standard deployment for clients.
What is an identity score and why should you care?
Microsoft tracks a number of secure scores for you to use as an indicator of a well-configured tenant. The identity secure score is of particular importance because most attacks begin with an account compromise or social engineering, leading to account compromise.
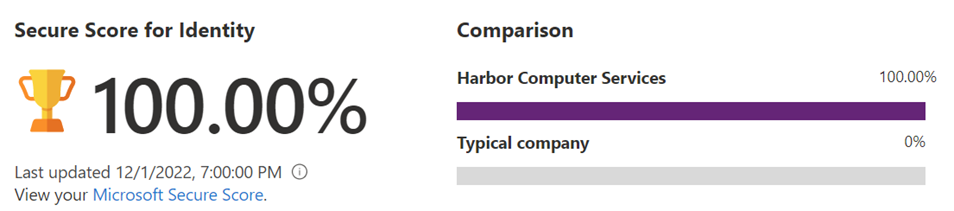
In the figure above, we see that Harbor Computer Services has a score of 100%, while the typical company of our size and business category has a score of 0%. Is that zero true? I doubt it. None of the other secure scores show a zero. But usually, they’re showing something less than 50%. Because of this, it might be that Microsoft isn’t yet tracking identity scores across their customers yet.
What does it take to get to a 100% secure score?
Quite honestly, we got here by accident. We were not striving to get a perfect score. We were instead striving to implement as many of the security features for identity as we could so we could protect our clients from us, their IT firm. IT firms are huge targets for good reason.
I will caution you that just because your secure score is perfect does not mean that you are 100% secure. I’m not sure what 100% means but we all know that there is no perfect and there is no 100% when it comes to security.
Invest in Azure AD P2
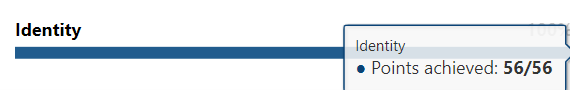
Perhaps this goes without saying but I doubt it. Azure AD P2 is essential to securing your identity. To get to a 100% security score, you’ll need to implement features that aren’t available in lesser licensing options. We also know from hovering over the identity line in secure score, that we need 56 points to reach that 100% goal. Since we didn’t do this on purpose, we’ll have to reverse engineer what we configured to help you reach that elusive perfect score.
You can find all of your secure scores in this portal. https://security.microsoft.com/securescore but if you just want to see the identity portion, that is available on the Azure AD portal main page.
Implement everything on the list
In the Azure AD portal, click the “Identity Score” menu item. It will take you to the is URL
On this page is the information that you need. It’s a list of items to be configured for identity security. Click the “Columns” item and add the “Current Score” and “Max Score” columns. Now you can see where your identity security needs work. To get to 100%, you’ll have to implement each of these items.
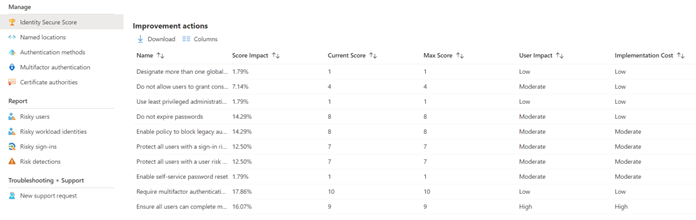
When it comes to implementation, you can sort by the column “User Impact” and see which items are going to disturb your users most.
Tips and suggestions
Here are a few things to know about implementing each of the items on the list.
Designate more than one global admin
This is usually not the problem that most tenants have. Most have too many global admin accounts. You should have up to three and one of those should be a break glass account with a 200+ character password and is exempt from most policies. If you lose access to your tenant, Microsoft cannot get it back for you.
Use least privileged administrative roles
Here it just wants to see that you’re using other admin roles besides Global Admin in some capacity. Last time I checked there were more than 50 administrator roles to choose from. Give those people who used to be global admin, just the roles that they require.
Require multifactor authentication for administrative roles
To earn the 10 points that this item offers, you’ll need to create a conditional access policy and set it to require MFA for all admin roles. This is one of the default security policies so unless you removed it, this should already be the policy for your tenant.
Do not allow users to grant consent to unreliable applications
I was quite surprised to learn that Microsoft only grants 4 points for this item. To me, it’s a high-impact security item. To implement this policy, you’ll configure the Enterprise Applications policy. If you really want to limit the impact of shadow IT, then include an admin workflow in the policy so that users have to request admin approval to add the application.
Do not expire passwords
This may be a tough one in some regulated businesses. Many regulatory requirements include mandatory password rotations but that’s no longer best practice because it’s been found that users tend to increment passwords making them easier and easier to guess.
Enable policy to block legacy authentication
This is another of the security defaults so unless you have removed it, this conditional access policy should already be enabled. If not, consider using the new conditional access policy templates. They are really easy to use. You’ll find template categories for devices and identity.
Protect all users with a sign-in risk policy
This one requires your P2 license and will protect your users from suspicious login attempts. This will occur when a non-typical event happens such as logon from a different location, using a different device, or being on public Wi-Fi with a known bad IP. Microsoft keeps the exact logic secret. My users do complain when they get prompted for MFA when they think that they shouldn’t but reminding them that it can occur when someone is trying to hack them and Microsoft just wants to verify that they are still really themselves, smooths over the annoyance.
Protect all users with a user risk policy
This is another one that requires your P2 license and another case where Microsoft keeps the exact logic secret. Here you’ll apply a conditional access policy that might block your users from authenticating or might prompt them for MFA a second time, when Microsoft detects that the user’s behavior is unusual and may not actually be them.
Enable self-service password resets
Microsoft scores this as a moderate user impact because you, as admin, must not only configure the settings in Azure but if you’re using Azure AD Connect to sync your on-premises AD, then you also need to enable password writeback. Once you’ve gone through that pain though, your users will thank you because now they will have one password for both ADs and with this policy, they can reset their own password. Your helpdesk, however, will be busy for a while helping people get alternative phone and email addresses registered into MFA.
Ensure all users can complete multifactor authentication
This is the only item listed as high user impact but since it’s the process of getting everyone to complete the MFA registration process, it really is a pre-requisite for successfully implementing MFA. Many users require some handholding and words of encouragement from the helpdesk but implementing MFA and removing 98% of the attacks on user credentials is 100% worth the time and effort.
Conclusion
That’s it! Once you’ve implemented these policies, you will have secured identity in your organization according to Microsoft’s recommendations, and you too will have hit that 100% secure score.