
The patch management process is an essential part of keeping your network secure. Regular, systematic patching ensures that your IT systems can repel common threats from viruses and cyberattacks like ransomware. But headline-grabbing data breaches have demonstrated that not all organizations run their patch management process diligently. Are they failing at the process? Or is the process failing them?
This post summarizes the steps in the typical patch management process. It also explores the future of patch management in an era when the process appears to no longer serve organizations effectively.
Steps in the typical patch management process
1. Identify and inventory systems and network
The first step involves building an inventory of all devices on your network. In organizations of any size, automated systems management tools provide the best way to discover what you have on the network and where it resides.
Because patch management reduces organizational risk in the security, stability and functionality of a network, you start by searching for the network’s weakest link. Every computer and device on your network must run the most recent security patches, and insight into all devices is the key to finding and patching any unmanaged or rogue endpoints. Finding those potentially dangerous blind spots keeps you from being vulnerable to attack due to poorly enforced security policies.
2. Scan systems
Once you know where the network endpoints are, the next step is to find out which applications are installed on them. The state of any device is the sum total of its software, so you’re looking for vulnerable devices whose software is out of date. Most systems management products run an agent on each device that scans against a list of known vulnerabilities.
Scanning computers to evaluate whether they are up to date is an ongoing activity, not a one-off. You should automate the activity to maximize the overall effectiveness of your patch management process. It’s important to scan systems regularly and assess the results of the scan so you can identify and manually address any issues that fall through the cracks of automation. That way, you can reduce wasted effort and focus on the areas that require attention.
3. Categorize assets by risk and set priorities for patches
IT administrators can prioritize patching by sorting updates according to levels of severity; for instance, critical, high, medium, low and none. Common Vulnerabilities and Exposures (CVE) data is also a useful source of information for determining which patches should be implemented first. When metadata accompanies the patches, it usually includes the severity rank; use that as a guide in deciding which vulnerabilities and patches require immediate attention. An organized system of priority patching allows IT administrators to better manage their workload and ensure that their systems are secure.
Note that not all patches should be treated the same. You may need to push out some patches immediately, depending on the urgency of whichever problem the patch addresses. Lower-priority patches can wait for the regular maintenance period, such as Patch Tuesday. And, depending on scope and severity, some critical patches apply only to specific servers or departments, while others need to be pushed out across an entire organization without delay.
4. Test the patches
As with any change in software, it’s good advice to test patches before deploying them on a large scale. However, with zero-day vulnerabilities, patch testing may not be an option due to the clear and present danger posed by bad actors. In these cases, IT teams must calculate the risk associated with the patch, accept the risk and move on to deployment without testing. If resources allow, IT can apply the patch to a test machine first and then study the change logs to see what exactly has been modified and ensure it won’t affect other applications.
The best practice for deploying patches is to first roll them out to trusted users, such as members of the IT team or users who have volunteered. That fills the patch testing phase with technologically proficient users who are better equipped to deal with any problems that arise and communicate them to IT for resolution. Later, you can roll out the patches to other user populations.
The goals are to identify any issues with the patches, reduce the blast radius of adverse events and validate the successful application of the patch. Whenever you test patches before implementation, you help avert disastrous consequences that may leave you vulnerable to attack.
5. Conduct phased patch releases
What prompts IT teams to delay or even avoid patching? In some cases, they are wary of introducing change and unintended consequences. The vendor’s release notes are intended to allay those fears, and if that assurance is still insufficient, IT may adopt a phased approach when rolling out the patch. That approach could entail starting with just a small test bed of five percent of the population of devices, or selecting particular user profiles, workloads and configurations first to gauge results. The result is a more accurate cross-section of devices in the organization that helps IT better anticipate any side effects from deploying the patch.
The best way for the IT team to plan and implement patch management is to centralize policies, define target populations and communicate regularly with users. That keeps the team in control of the process all the way through.
6. Automate patching
As noted above, automation can reduce the time and effort associated with patch management. Automated patch management solutions allow for the remote deployment of patches without manual scanning or packaging, which eliminates the risk of version drift that leaves organizations vulnerable to cyberattacks.
Automated systems also provide an inventory of the software and versions installed on each system. They download the latest updates from a repository or vendor website, validate their integrity and schedule deployments automatically or manually with just the push of a button. That makes it easier to keep systems up to date, while also freeing up admins from having to remember when they need to push out patches. As in all automated solutions, the side effect of automated patching is that it frees IT staff to focus on higher-value, less repetitive tasks.
7. Look at patching through the users’ eyes
When it comes to patch management, it is important to consider the user experience. Some patches cannot be installed transparently, and users may notice a drop in performance during installation; they may even need to restart their device. To minimize disruption for users, businesses should schedule patching after productive hours, when possible. Additionally, businesses should give their users scheduling options for installations and system restarts. For example, rather than forcing all updates at a given time on a given day, or saturating the network with installation traffic, IT can allow users to choose a more convenient time, or to schedule the update after hours.
To provide a better user experience, give users some control over when and how patches are installed. Set deadlines for installing patches, but allow users the option of postponing installation at any time between now and that deadline. Remote and mobile users have limited time on the network as it is; when a patch requires a reboot, offer them options that will help them avoid a loss in productivity.
8. Measure systems before and after patching
Patch management metrics can help you understand the success of your patching efforts and identify where you need to improve. Typical metrics include the total number of devices patched so far, a list of devices still to be patched and the percentage of successful/failed installations. With that information, you can initiate secondary efforts such as starting up forgotten devices in need of patching and directly contacting those users who procrastinate their updates.
9. Disaster recovery
Ensuring that you have a solid backup and disaster recovery strategy in place is an essential part of any patch management program. With reliable backups, you can recover your data and restart systems quickly, even if a security update goes wrong. Consider investing in cloud-based backup solutions to help provide an extra layer of protection for your critical data and systems.
Inefficiencies and shortcomings of the typical patch management process
The question persists: “If patching is so important for IT security, then why do so many companies stumble when it comes to the patch management process?”
What are the main inefficiencies associated with the traditional patching process?
For one thing, patching is about rebuilding things you’ve already built. You have to test, then patch, but it’s an event-driven, task-based process that doesn’t lend itself to streamlining or efficiency. You can’t look very far down the road with patching, because it’s not about the long term. You’re in short-term mode whenever it comes to patching.
For another, many organizations have fallen into a piecemeal approach to patching. The big software vendors push out their patches and make them easy to install, but enterprise apps that depend on software from multiple smaller vendors need patching too. If you’re using applications from a variety of vendors, you’ll find that most systems management solutions offer a limited subset of what you really need to patch in your environment. Be sure you’re covering the part of the spectrum that’s not provided by your management tool.
Finally, the trend toward the remote workforce introduces obstacles to the patch management process. Are you able to connect to all your endpoints reliably? Are you having to force remote users to connect via VPN just so you can get patching done? Do you have to pepper users with email and follow up so you can meet your patching milestones? Remote work tends to take a process that should be (and in some cases used to be) almost completely automated and turns it into a labor-intensive process.
What are the end results of these pitfalls in the patch management process?
As in any inefficient process, poorly managed patching causes morale to erode as people see that they can’t keep up and can’t be effective in their roles. Lower morale naturally leads to lower productivity and a decline in team culture because wasted time and wasted resources frustrate your IT team members.
The problem is that few IT workers would enjoy spending all their time patching machines; patching keeps them from spending time on higher-value tasks. There’s the financial aspect of spending five days of salary per week on work that could be done in three days per week. While it’s true that patching is a necessary task, is it necessary to spend that much time on it?
The ideal for each wave of patch management is a process that involves up-front time and human effort, then runs automatically on all the organization’s endpoints.
What are the main advantages to cloud-focused, policy-based patching?
To avoid the inefficiencies and pitfalls in the traditional patch management process, put in place repeatable and scalable processes that work for you instead of in spite of you. Go beyond the basics and implement a dynamic, policy-based approach to patch deployment that offers a way to approach testing in that scalable, repeatable way. It paves the way for you to expedite high-urgency patching while still enabling testing in small populations of users before rolling out to all users.
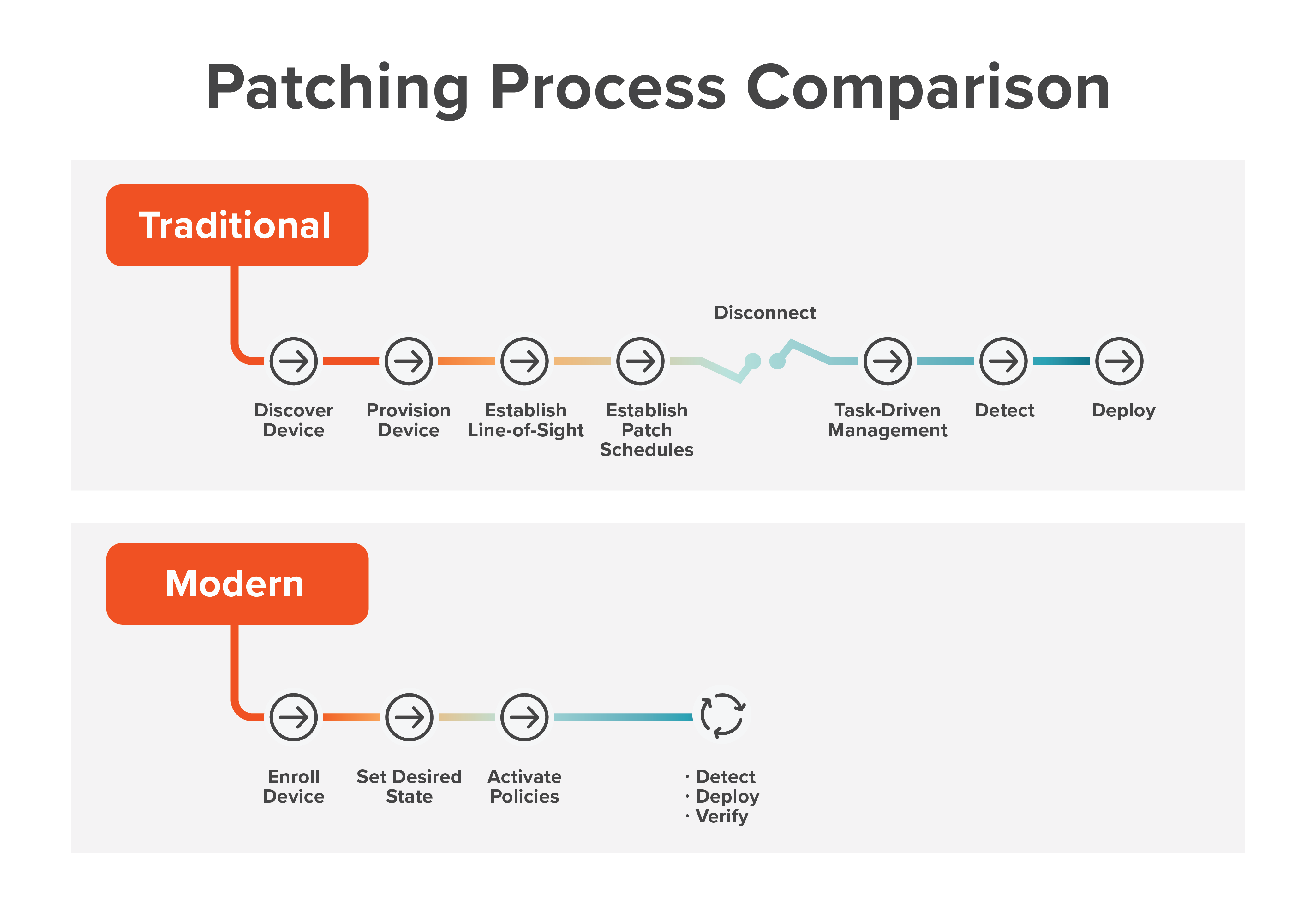 Policy-based patch management keeps labor-intensive tasks to a minimum and frees up time so IT staff can work on other, more strategic initiatives. By evolving from event-driven to policy-driven management, you take the crises out of patching and reduce the amount of firefighting you and your team engage in.
Policy-based patch management keeps labor-intensive tasks to a minimum and frees up time so IT staff can work on other, more strategic initiatives. By evolving from event-driven to policy-driven management, you take the crises out of patching and reduce the amount of firefighting you and your team engage in.
Conclusion
As long as vendors continue to issue security patches, IT teams will have to live with and perfect their patch management process. The traditional steps are well known, but that doesn’t make them any less burdensome and time-consuming. As a result, some IT teams don’t accord patching the priority and resources it requires to ensure that their networks remain safe from threats.
A bright spot in the landscape is policy-based patching that helps IT teams advance beyond event- and crisis-driven patching. Policy-based patching allows you to build repeatable, scalable processes that reduce your reliance on labor-intensive patching methods and free up your IT staff for higher-value tasks.



