Ever since the advent of smartphones and tablets, enterprise IT teams have been required to evaluate Bring Your Own Device (BYOD) pros and cons, trying to strike a balance between corporate security and employee convenience. With BYOD, employees use their own hardware and software to access business-related systems, applications and data. Whether an organization opts for BYOD or company-issued devices, evaluation of the options have taken a new turn in the era of long-term remote work.
This post will review BYOD pros and cons now that employee-owned devices are often a given in the way companies do business.
BYOD pros
Simpler onboarding/offboarding
Users who take their own device to the workplace are already familiar with how it works and what is installed on it. That means a shorter learning curve which can result in improved productivity because less training is required.
Smart companies that implement BYOD through a Mobile Device Management (MDM) system and a solid identity provider to make it easier to on- and off-board employees. Since every employee will require access to data and applications on the network, it simplifies that access by creating a single user identity, trusted by select apps and resources. It’s more efficient than creating accounts for each application and network resource that new users will access.
That single-identity approach also pays off when users depart at the end of the employee lifecycle. By disabling identity in one place, IT terminates access for those users to all resources and apps, wherever they may reside on the network. Rather than managing dozens of systems individually, IT can zoom out and manage them uniformly, in a thorough, efficient process of onboarding and offboarding.
Employee convenience
Many employees consider using a single device — especially a smartphone — preferable to having separate devices for personal and occupational use. As a result of this convenience, team members can have improved satisfaction because they don’t have to juggle carrying around two devices.
Since working from home and BYOD policies have become commonplace, employees enjoy the flexibility of being able to get work done from anywhere at any time using their own smartphones, tablets and other devices.
Increased productivity
As employees bring their personal devices into the workplace, it’s natural for the business to see the trend as a competitive advantage. They think of the potential for increased productivity from users working on their personal devices. And, from the employees’ perspective, many workers believe that the option of conducting personal and professional business on the same device amounts to a boost in productivity.
Financial savings
Strictly from the perspective of capital expenditure (CapEx), BYOD looks to be a recipe for saving money. Every device that an employee takes to work is one less device the company needs to purchase.
A study conducted for Samsung by Oxford Economics examined the impact of smartphones in small to mid-sized businesses in the U.S. The study, titled “Maximizing Mobile Value — To BYOD or not to BYOD?” found that annual spend per employee for BYOD smartphones was about one-third less than the spend on employer-provided devices (EPD).
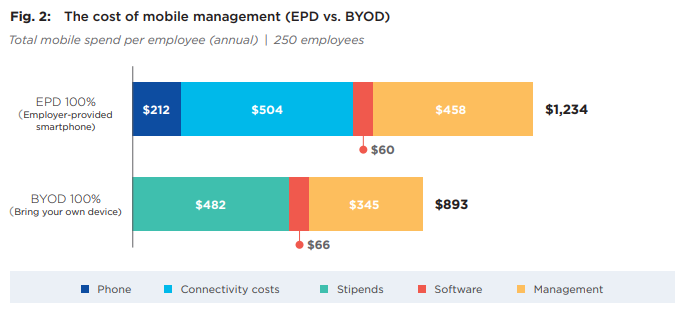
That analysis included up-front device acquisition, mobile service plans, stipends (compensation), management costs and mobile device management (MDM) software.
Naturally, those look like huge advantages to companies focused on reducing CapEx.
BYOD cons
Financial risks
Despite the potential savings presented by BYOD, organizations must evaluate the potential financial consequences of a breach that occurs due to a team member accessing work data and resources on their personal devices. In a BYOD program, organizations have no control over the other applications and data that an employee may download to—at the end of the day—an employee’s personal device. Even though the cost for a BYOD program is about one-third less than the spend on employer-provided devices, is that cost savings truly worth the potential consequences of a breach via a team member’s personal device?
Privacy and security risks
Permitting unmanaged devices to access corporate information tends to expand the attack surface of the business, bringing about new risks that IT teams must manage. Even before the BYOD era, IT knew about those risks, and employees still used their personal devices — whether approved by IT or not — for work purposes.
Endpoint devices like computers, smartphones and tablets access corporate data from both outside and inside the corporate firewall. The realistic approach is to assume zero trust; in other words, no network or user or application attempting to access company resources should be blindly trusted. Secure authentication is imperative.
The way to address security risks introduced by BYOD is through a companywide, zero-trust approach to endpoint security. With zero trust, all business systems must prove confidence in:
- The identity of the user
- The source device
- The communication channel over which the data will be consumed
Companies that embark on BYOD are enabling users to work outside the home office as easily, efficiently and securely as if they were inside the network perimeter, logged in and joined to the domain.
The first step in a zero-trust approach is to adopt sign-on and authentication methods sufficient to verify users. In the context of working from home and remote work, users often connect to company resources over a virtual private network (VPN). But when running across the corporate firewall, authentication needs to run deeper to verify users. The solution is a solid identity provider that provides authentication, ideally supplemented by a layer of multifactor authentication (MFA).
Separation of work data from personal data
Employees may not want to give the company access to their personal data. And companies, conversely, want to minimize the risk of unauthorized access or unapproved use of company data. The problem is that BYOD has the effect of moving (and sometimes storing) both kinds of data inside the employee’s device. The commingling raises issues of risk for the company and personal exposure for the employee, and company policy must address both of those issues.
Support burden
It’s difficult to anticipate the support costs that the company will incur as a result of BYOD.
Suppose that employees depend on their own device to get their job done, and they need help accessing an internal web application or Microsoft 365. Is it in the employer’s best interest to support devices they had no hand in selecting?
It’s a big leap from the casual technical expertise needed to navigate UI and apps to knowing how to troubleshoot configuration settings across diverse operating systems, like iOS and Android.
BYOD represents a huge departure from the traditional IT model of vetting, selecting, provisioning and managing all the endpoints that touch the network. Helpdesk staff lose the main advantage of predictability when they are called in to support devices that employees have selected, configured and personalized on their own.
Instead of troubleshooting the same device with the same configuration settings across an organization, BYOD introduces the complication of wildly varied devices, configurations and settings. Do organizations really want their IT support teams in a BYOD environment spending their time and resources troubleshooting users’ personal devices?
Excessive support costs are often overlooked in back-of-the-envelope calculations around CapEx savings.
Lost or stolen devices
There’s more to BYOD than employees simply using their personal devices for work. Loss and theft are perennial facts of life, and BYOD devices are subject to them. Losing a device due to human forgetfulness, or ordinary theft means more risk for data loss or potential breaches.
Unmanaged devices holding both company and personal data pose the risk of exposure of sensitive information. If a BYOD device has access to company data via a MDM system, IT admins can issue a wipe command to delete company data from a lost or stolen device remotely if the MDM is configured correctly.
Legal issues
The risk of lost or stolen devices is closely related to liability, and companies and employees are both responsible for keeping sensitive data from falling into the wrong hands.
Almost by definition, BYOD entails less corporate control over internal data. IT departments can put in place some guardrails that segregate business data and personal data from each other. The goal is to effectively containerize the data.
However, technical guardrails are not as important as the company culture when it comes to limiting liability. With the convenience of BYOD comes the responsibility for keeping sensitive data safe. Wise companies supplement technology with employee agreements and training about handling corporate data responsibly and preventing loss or theft of personal devices. Given that some devices will inevitably be lost or stolen anyway, the goal is to impress upon employees the importance of reducing the potential harm from data loss.
Work-life balance and company culture
Running company applications on personal devices represents a toehold into the employees’ technology-life. Does it also represent a toehold into their personal life? In other words, does BYOD give companies the right to expect employees to work longer and be more available?
At that point, BYOD opens new aspects of company culture and management style. When the company supports corporate apps and ubiquitous access on employee devices, does that mean employees are obliged to respond to their managers’ messages after business hours? When the technology is in place to hash something out now instead of waiting until the next business day, the overall employee-employer contract comes into play.
Like working from home, BYOD pries open a new door to work-life balance for both the company and the employee. It’s good hygiene for companies to set boundaries on their expectations for employee availability even if they offer an employer-provided device. It’s good self-preservation for employees to set boundaries on how and when they will respond to company messages after hours. Properly managed, the balance results in solid employee-employer relationships.
On the employer side, consider the difference in urgency between “Hey, found this data. Let’s talk about it now,” and “Wanted to get your eyes on this. I’ll follow up in the morning.” And, on the employee side, consider the difference in obligation between “Aw, geez, here’s another late-night message I have to think about,” versus “My boss just texted me, but it’s late. I’ll check it tomorrow.”
Financial obstacles for employees
What about employees who don’t have smartphones, or whose personal devices are unsuited to BYOD? Smartphones and high-speed connections cost money, so they are not a given for everybody. For some individuals in regions with a high cost of living, they are a luxury. Others simply select a flip phone to put limits on the time spent on their devices.
If company culture is one of “We’re all available on Slack,” can the culture extend BYOD policy to those who may not have a smart phone? Companies can offer stipends for employee-owned devices, but at that point, isn’t it just as sensible to plan on a certain number of EPDs?
Enlightened IT decision makers must realize that they cannot entertain a strict expectation of 100-percent BYOD. If that’s the proposed solution, there should be some frank conversations with the Human Resources department: “These employees make strong contributions, and we value them. But they can’t afford or don’t want smartphones. If our culture and requirement is 100 percent BYOD, we may need to help them out and provide them with corporate devices. Then they can maintain their productivity alongside their peers and colleagues, who are functioning just fine in our BYOD program.”
In some organizations, a small batch of EPDs may be the price of BYOD.
Conclusion
Taking a thorough look at the various BYOD pros and cons makes it clear that the choice is often a double-edged sword.
While the greater productivity, reduced cost and around-the-clock availability that BYOD provides is compelling, companies know that the risk from an expanded attack surface is real. At the end of the day, every organization must evaluate the various trade-offs and risk levels they’d like to assume when considering BYOD policies.