As I do each year, I recently got together with a number of my very talented colleagues at Quest to think about key trends and lay out our IT predictions for the coming year. Since we specialize in Active Directory and cyber resilience, we were particularly interested in uncovering and exploring the latest trends related to those areas.
That might seem odd for a predictions blog; after all, Microsoft Active Directory (AD) is over two decades old. Shouldn’t we have been focusing on the latest cutting-edge technologies and Azure AD instead? Wouldn’t they be more important for the coming year than on-premises Active Directory?
Actually not. The truth is, Active Directory remains the primary authentication and authorization system for most organizations today, even as cloud adoption continues. Accordingly, a breach of Active Directory security can spell disaster for the organization.
Indeed, Gartner, for one, is mentioning AD more and more in its IT security research of late. Here is one recent example that captures the central role AD still plays in modern cybersecurity:
Active Directory is one of the fundamental pieces of an organization’s IAM program and enables identity management and authentication. But while organizations understand the criticality of AD, the security of AD is often overlooked. If AD is breached, an attacker gets virtually unrestrained access to the organization’s entire network and resources. This makes AD a prominent high-value target for threat actors.
- Gartner, Inc. “Emerging Technologies and Trends Impact Radar: Security,” 12 October 2021, https://www.gartner.com/en/documents/4006795.
The threat to AD is not merely theoretical — Microsoft confirms that AD actually is a core target of malicious actors. At The Experts Conference (TEC) 2022, Alex Weinert, VP of identity security at Microsoft, put it succinctly: “on-premises is where we’re being attacked.”
With that background about why my colleagues and I approached our brainstorming session with our AD security goggles on, let’s dive into our six key IT security predictions for 2023.
1. Inflation will increase security risks.
I’ll open with my own top prediction, not because it is the most important but because it relates to one of the hottest topics in the news today: inflation. We all know that inflation is affecting individuals, organizations and governments around the world — but my colleagues and I were interested in analyzing exactly how inflation is likely to affect IT security. We identified multiple scenarios that are likely to play out in the coming year.
First, we’ve already seen ransomware brokers emailing users at organizations and asking them to deploy their malware. Of course, cybercriminals looking for disgruntled employees willing to sabotage their employers is hardly a new development. But with more people hurting financially due to soaring inflation, malicious actors in 2023 will have a larger pool of potential accomplices who just might succumb to temptations like a bribe of $1 million in Bitcoin for unleashing ransomware.
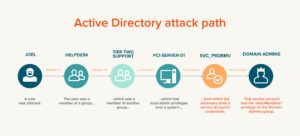
Misuse of insider access is not limited to ransomware. Users feeling the pinch of inflation can also sell their credentials. And while it might seem that an ordinary user’s credentials would not provide a great deal of value to an adversary, the truth is far different. Quest security assessments often find that a huge percentage of user accounts in an IT environment — usually a staggering 70–100% — have rights that could be escalated in a handful of steps to give an adversary access to Tier Zero assets, including control of the entire Active Directory domain. What’s more, open-source tools will lay out these attack paths in clear detail, without the need for administrative permissions. As a result, organizations will need to implement attack path management.
At the same time as cybercriminals are ramping up their attacks, IT teams will be struggling with their own inflation challenges. In particular, budget cuts combined with unfunded IT mandates are likely to be a particularly vexing reality in 2023. With no shortage of issues to be addressed, IT teams will need to stay sharply focused. In particular, they will need to ensure that they have a robust disaster recovery strategy and automated solutions that speed the restoration process. After all, the key to becoming more cyber resilient is not magically ensuring that you’ll never suffer an attack; it’s being prepared to get the business back on its feet as soon as possible if a disaster does strike.
2. Security will be a bigger factor in growth and M&A strategies.
Inflation, of course, will also be affecting the growth strategies that organizations adopt in 2023. Indeed, after boasting a record year in 2021, the M&A market ebbed in 2022. The relatively slower pace, which seems to be matching healthy pre-pandemic levels, is affording companies more opportunities to be selective in their choices. Bert Skorupski, senior manager of sales engineering at Quest, expects that in 2023, security will be a big factor in M&A planning, as well as in organizations’ broader growth strategies.
For starters, executive teams will inquire more deeply into the IT security posture of potential acquisitions, and choose not to acquire companies that are a risk. When M&A deals do happen, the focus of the IT integration process will likely shift away from migrating everything as quickly as possible and toward making security far more of a consideration. For example, as Bryan Patton recently explained, organizations today are still migrating SID History when they haven’t cleaned it up, which is a serious security risk. In 2023, we expect to see IT teams given the latitude required to deliver a more secure IT integration effort.
Slowing down the migration process will have knock-on effects. In particular, organizations will need to establish co-existence between the two (or more) IT entities involved from Day 0, and maintain it longer. Therefore, a truly effective co-existence solution will become even more important.
On a slightly orthogonal note, IT integration efforts will be affected not just by security but by compliance. Because of the significant changes in exchange rates and the increased buying power of the US dollar, we anticipate a ramping up of international mergers and acquisitions. As a result, US IT teams will need to pay increased attention not just to federal and state mandates, but to regulations from around the world.
3. Supply chain risk management (SCRM) will come into its own.
Daniel Gauntner, director of product marketing at Quest, zeroed in on what the risks in the supply chain will mean in 2023. He noted that recognition of just how connected organizations are to one another today has been growing steadily. One big jolt of awareness came in 2020, when hackers compromised the private networks of dozens of US companies and government agencies and spied on them for months — without having to infiltrate any of them directly. Instead, they broke into software vendor SolarWinds and added malicious code to its Orion software, which the other organizations were using to manage their IT resources.
However, this is but one example of a supply chain attack in recent years. To help organizations mount effective defenses, Section 4 of Executive Order 14028 in 2021 directed NIST to work with a wide range of organizations to identify existing or develop new standards, tools, best practices and other guidelines to enhance the security of the software supply chain. NIST began steadily releasing guidance and submitted its progress report to the President in May of 2022. In addition, version 2.0 of the Cybersecurity Maturity Model Certification (CMMC) framework from the U.S. Department of Defense (DoD) introduces strict supply chain requirements. In the coming year, we anticipate that organizations will up their commitment to meeting these standards in order to avoid becoming the next breach headline.
However, their efforts will not be in the name of cybersecurity alone. Cyber insurance is becoming more expensive and harder to obtain. Vendors will increasingly be asking organizations to prove not only their own cyber defenses, but those of their supply chain. Therefore, organizations will be highly motivated to comply with the NIST guidelines and CMMC framework so that they become valuable partners to others.
Then there’s the United States Trade Agreements Act (TAA) of 1979. I know, you’re thinking, Jen, 1979?? I thought this was a blog about predictions for 2023! Well, the fact is, TAA compliance is actually a hot topic right now, so stick with me! The TAA limits U.S. government procurement, including GSA Schedule Contracts, to products made in the US or designated countries. Therefore, if you want to sell goods to the government, you need to make sure your products are TAA compliant. That can be a real challenge today, since a number of major manufacturing centers, including China, India and Indonesia, are not on the list of designated countries. Also absent from the list are Russia, Iran and Iraq. With geopolitical tensions high and the US government wary of state-sponsored threats, organizations should expect increased scrutiny of TAA compliance and will need to pay even more attention to supply chain risk management.
4. Organizations will broaden their thinking about IT skills.
Jason Jacobo, senior product manager at Quest, pivoted our discussion from corporate strategies and legislative mandates to a deep discussion of the IT professionals who deliver on those priorities. He noted that the recent Great Resignation resulted in a significant movement of IT pros to organizations that provided better rewards, in terms of both compensation and flexibility. But he pointed out that we cannot let that shift obscure a critical underlying fact: We still face a global IT skills shortage, and, in particular, a lack of qualified cybersecurity professionals.
As a result, organizations will need to shift their staffing strategies in 2023. They will begin to look for individuals who have a growth mindset rather than a fixed mindset, and who are eager to expand their expertise rather than rest on their laurels. In particular, they will need people who are willing and able to adapt their existing skills to cybersecurity, and to keep up with the rapidly evolving threat landscape. And, of course, organizations everywhere will need to take steps to retain their most valuable talent.
5. Organizations will focus on efficiency and automation.
Patrick Ancipink, senior product marketing manager at Quest, brought together two of the predictions discussed above: High inflation is making everything more expensive, and challenges around IT cybersecurity staffing are leaving organizations vulnerable. Patrick observed that organizations can address both by improving their effectiveness through strategies like process refinement and automation.
Accordingly, in 2023 we expect to see a higher priority on process management and better utilization of labor-saving tools. Organizations can do more with less while dramatically strengthening their cyber resilience by executing a holistic cybersecurity strategy that takes advantage of the available automation in proven practices like risk identification and remediation, auditing, threat detection and response, and backup and recovery.
6. Zero Trust will move from hype to reality.
Our last prediction comes from Bryan Patton, principal strategic systems consultant at Quest and a Certified Information Systems Security Professional (CISSP). He expects that the benefits of the cloud will only become more attractive in 2023. Faced with economic uncertainty, organizations will value its quick scalability, and their worries about IT skillsets will be mitigated by being able to reduce their on-premises footprint in favor of managed services. And, of course, the cloud enables organizations to better support the modern hybrid workforce, so they’re better able to attract and retain top talent.
But cloud adoption also erases the traditional perimeter, when everything “outside” is suspect but everything “inside” is assumed to be trustworthy. This change will drive Zero Trust from the realm of hype into widespread practical application. In a Zero Trust model, no user, service or other element gets authenticated once and then given a free pass. Instead, continuous verification is required: Real-time information from multiple sources is used to make access decisions and other system responses.
Success will build upon success. More mature organizations will adopt Zero Trust, and their success will build confidence in others. Organizations will build, refine and share best practices for implementing a Zero Trust model, providing practical guidance that will drive adoption and improve results.
Wishing you success on your path to cyber resilience in 2023!
Now you have the Quest team’s top six predictions for 2023. We hope you’ll find them useful in enhancing the security, productivity and cyber resilience of your organization in the coming year.