With the adoption of flexible work and the demands of a modern workforce, having an endpoint management strategy has become a critical aspect of organizational security. A study by the Ponemon Institute found that 68 percent of businesses have faced at least one endpoint attack resulting in compromise to their data or infrastructure. The same study cites 68 percent of IT professionals also observed an escalation in the frequency of endpoint attacks.
As attacks on endpoints continue to increase in both frequency and sophistication, organizations are needing to adopt a proactive, agile and resilient endpoint management strategy that ensures the security and integrity of their endpoint devices.
In this article, we will discuss the biggest mistakes organizations are making when it comes their endpoints and the key steps to take when creating a modern endpoint management strategy for your business.
What is endpoint management?
So, let’s start by talking about what endpoint management really means. Endpoint management is the process of setting up and overseeing access to endpoint devices, as well as enforcing security regulations to mitigate the risk of cyberattacks. This practice enables authorized users to connect to the main network, whether on-site or remotely, while also providing organizations with complete visibility of their endpoints across a distributed IT landscape.
The importance of endpoint management
Working from home and remotely is common practice today for many businesses, requiring devices to access apps and data remotely from the corporate network. However, each of these devices and network endpoints are potential targets for an attack. An endpoint management strategy offers a dependable approach to monitor and protect all your endpoints, particularly with the increasing popularity of Internet of Things (IoT) devices and bring your own device (BYOD) policies.
Controlling an abundance of device types
As organizations experience a surge in both the quantity and variety of managed devices, the task of tracking and securing endpoints becomes even more challenging. Endpoints can range from servers and gateways to laptops, tablets, smartphones, printers, and IoT devices.
Maintaining control over these endpoints ensures that devices accessing corporate data—even in potentially unsecured environments like public clouds—are authorized and equipped with the appropriate access credentials. This enables users to perform job responsibilities in a secure and reliable manner, while also giving organizations complete oversight of all devices.
Managing a diverse array of platforms
As the number of endpoint devices grows, so does the need for varied software platforms to support and connect a dispersed workforce. An endpoint management strategy identifies everything connected to the central network, regardless of the platform or operating system they use. It speeds up procedures like updates or migrations and enables automation to reduce the burden on manual resources.
Facing heightened cybersecurity risks
The increasing number of devices and platforms provides additional opportunities for bad actors to exploit endpoint vulnerabilities. There are several security threats to consider, including phishing, insufficient patch management, loss or theft of devices, and software exploits. To reduce exposure to cyber threats, robust policies are put in place to protect against potential attacks.
Endpoint management challenges
The prevalence of personal devices within the workplace is undeniable. This proliferation of devices poses challenges, particularly in managing BYOD programs. Regardless of whether there’s a formal policy in place or not, the reality is that someone within the company has likely introduced a personal device into the work sphere. Whether the devices are known or unknown, they are present in your environment. Employees may be using them in various capacities, from transferring files to connecting to the network in some manner.
Dealing with unknown devices is a tough nut to crack. You can’t secure what you’re not aware of. The challenge lies in finding a way to recognize the existence of personal devices and incorporate them into your system. So, how do you manage the intersection of personal and corporate devices in the workplace effectively? To start, let’s dive into the most common mistakes to avoid.
The most common endpoint management mistakes companies make
Not having a solid BYOD policy
Oftentimes, companies adhere to traditional policies for matters like equipment protocols or return policies, but an area that can get overlooked is BYOD.
A well-crafted BYOD policy involves properly identifying risks and integrating them into the policy framework. It allows employees to use devices they are comfortable with, while ensuring protection against security threats and vulnerabilities. With guidelines on how to properly use personal devices and clearly defined boundaries for device usage, it becomes easier to enforce policies and address any issues that arise.
Not having license compliance
License compliance is a critical area that demands attention. If you’ve ever faced issues with compliance, you understand its seriousness. Violations can result in substantial fines, sometimes amounting to millions of dollars, which could bankrupt a company.
There are three main types of licenses to consider:
Cloud-based licensing – Typically user-based and allows access from various devices. Often involves subscription models.
Traditional workstation applications – Covers software like AutoCAD and ArcGIS, which primarily operate on-premises and may involve perpetual licenses.
Database licensing – Involves complex considerations, such as CPU core counts or specific database tiers, and requires careful tracking and management.
For both cloud-based and traditional licenses, tracking usage versus purchased licenses is crucial. Without proper monitoring, situations can arise where software is installed on more devices than licensed for, leading to compliance issues. It’s essential to utilize systems for reporting, metrics and compliance standards to manage licenses effectively. By consolidating data into comprehensive reports, organizations can stay informed about license usage, anticipate renewals, and address any discrepancies.
Over-purchasing licenses
In many companies, it’s typical for different departments to have the autonomy to purchase software on their own. For instance, an IT department may procure their own set of software tools, while an accounting team obtains their own separate set of software tools. Oftentimes, these departments tend to overestimate their needs. Accounting might buy licenses for their 10 team members and add a few extras just in case, and other departments follow suit. This collective purchasing approach can lead to unnecessary excess. After multiple departments make similar overestimations, the organization may find itself with a surplus of licenses that are not actually required. This situation occurs frequently, which is why meticulous tracking is needed to limit over-purchasing.
Not keeping track of inventory
To maximize security, companies must have a comprehensive understanding of their environment. This includes knowing what assets are on the network, who is using them and their status. Without awareness of all your endpoints, device security becomes a challenge, especially with the prevalent threat of ransomware.
Relying on spreadsheets to track assets is not sufficient. Each department may have their own method of tracking, resulting in fragmented and unreliable data. This lack of a centralized system becomes problematic during compliance audits or when the company undergoes changes, like a sale.
Not tracking the lifecycle of devices
It’s important to take care of the company’s assets, and inventory serves as the foundation for efficient lifecycle management. From the moment items are ordered, tracking begins. This provides a seamless connection to endpoint devices, regardless of their location — be it remote work setups or office environments. In instances with frequent employee turnover, devices are often reassigned, making robust tracking systems indispensable to prevent misplacements.
Monitoring device usage and lifecycle stages also delivers information on warranty status and remaining lifespan. This data informs decisions like extending usage beyond warranty dates or retiring a device at its end-of-life.
Steps for creating an endpoint management strategy
1. Assess current IT assets
Inventory devices: Conduct an audit of all current IT assets used throughout the organization. This can include non-traditional IT assets such as smartphones, kiosks, or any device with potential access to an organization’s network and data. Typically, asset management software can be used to help track these devices. Be sure to select a software solution that offers device discovery. This will help automate and speed up the initial and ongoing device inventory.
Assess needs and requirements: To create an effective strategy, an understanding of the organization’s goals and needs is paramount. It is critical for IT to align with business needs and goals to gain stakeholder sponsorship and support. Understanding the organization’s needs will lead to understanding the requirements for hardware, software and network connectivity. Various stakeholders should provide input to ensure alignment with goals and strategies. These stakeholders can be anyone from department heads, legal to leadership.
2. Define management objectives
Once you have determined the needs for the organization, it is time to define the management objectives to align with those needs. The common denominator for every endpoint management strategy is securing access and integrity of the company’s data. Establishing security objectives is arguably the most important step, as other’s objectives are subordinate to that need.
Security: Establishing effective security protocols is key to protecting data from cyber criminals and securing sensitive data. However, cybercrime is not the only threat to an organization’s data. Natural disasters, accidents, misconfigurations or anything that can cause loss of access to or integrity of data needs to be considered. The steps to protect IT assets and data are many, such as encryption, backups, software updates, network security, and multifactor authentication.
Compliance: Any organization that has customers and associated data is subject to regulations or compliance policies. The costs of failing to meet these requirements could range from fines to criminal prosecution. With the widespread IT technology use within the economy, no company can afford to design a strategy without compliance in mind.
Efficiency: For an organization to be effective, it must allocate its time and resources appropriately. For IT, this means having the right type of devices configured properly, with the right software and safe access. Without these in place, users cannot access the data necessary to conduct commerce, and any impediment has a direct financial impact on that organization. Take, for example, if Amazon went offline for 10 minutes. Surely, it wouldn’t go out of business, but it could sustain losses in the millions of dollars.
3. Leverage a device management solution
Evaluate solutions: It’s important to choose a device management solution that aligns with your organization’s goals and strategies. Ensure it checks the boxes to align with security, compliance and efficiency. Consideration of tools can be complex as there are all-in-one tools, point solutions, various “free” software tools and open-source tools. Carefully consider the use of free or open-source tools, as support may not be available or may suddenly stop when relying on free development. Evaluate how support is accessed—is it only forums, chat or blog articles? Ease of use should also be considered; matching the skill set of admins with the software is very important. There are some very powerful tools available. However, you must have the right set of skills available to fully utilize them. With the wide uptick of cloud and SaaS offerings, as well as traditional on-premises software, the choices are many. Be sure to align with your organization’s goals for this as well. For example, maybe due to regulations, the cloud is not an option. When evaluating cloud solutions, be sure to look into the hidden costs, such as costs for consumption or bandwidth, which may cause a cloud solution to be more expensive.
Scalability and flexibility: Nothing stays the same, as we have recently seen with the move to cloud by many, due to the COVID pandemic. Ensure the software your organization uses is flexible enough to scale or change as needed. Acquisitions or sudden changes due to remote work can greatly impact the need for flexibility.
4. Focus on policy development
Device usage policies: Define acceptable use policies for devices to guide users on security practices, software installations and internet usage. Various stakeholders will also be involved in this process. Typically, the organization’s legal team is part of this to ensure legal requirements are met. Ensure each organizational user is aware of your best practices and signs off on any device usage policy.
Security policies: Develop comprehensive security policies covering device encryption, password protocols and data protection measures. Written policies help ensure that device administration understand and properly configure all devices in their charge. If written policies are not in place, it is easy for security measures to be misconfigured, or at worse, not implemented. These policies are there to help ensure the safety and security of an organization’s assets and data.
5. Plan for implementation and device configuration
Deploy the management solution: Once the decision has been made to implement a chosen software, careful planning must happen. Ideally for each tool, a pilot group should be chosen to make sure any unforeseen issues, technical or otherwise, are uncovered. This could be an integration between other tools, or even the capability of staff to leverage the software. If proof of concept or trial had occurred before purchase, many of these items can be addressed. Regardless, careful planning of the implementation is key to a successful rollout.
Configure devices: Once the supporting software is chosen and implemented, the devices themselves need to be configured. More than likely, devices are already deployed and in use. So, make sure implementing a management solution to existing devices in the field doesn’t disrupt ongoing operations. Newly purchased devices can be fully configured and managed prior to deployment in the organization. Some key technologies to consider would be light touch or zero touch enrollments for devices, such as Autopilot Windows or a Device Enrollment Program for Apple. This allows devices to be shipped directly to end users and provisioning occurs at the time a user enrolls or logs on for the first time, thus saving cost and time over traditional device imaging.
6. Prioritize training and support
User training: Both users and administrators need to be trained on the software, operating systems, policies, and procedures pertinent to the organization. Without this training, their implementation will not be optimal. Training should be considered as an ongoing investment and not a singular occurrence. In addition to onboarding training, a quarterly or monthly training calendar should be established. It is not necessary to host a traditional classroom style training to be effective. Various methods based on user needs for training should be utilized, as each person learns differently. The type and scope of training also needs to be considered; experienced users may need less frequent rudimentary training. While they may benefit from quizzes or newsletters to keep things fresh of mind, the key here is for the training to be consistent and ongoing to align with business needs.
Technical support: No matter how well thought out and planned, the need for technical support, much like training, should be formalized and ongoing. Metrics should be tracked to ensure the outcomes align with business goals for uptime and performance. Depending on the type of requests and location of users, different types of technical support must be implemented. Some may choose to keep support in-house or potentially leverage partners to outsource technical support. Different software vendors will also offer different levels of support, often times with higher levels of support requiring a higher financial cost. Consider these aspects carefully when choosing how technical support is implemented.
7. Monitor actively and prioritize maintenance
Continuous monitoring: Once your systems are in place, they need to be monitored to ensure smooth operation, uptimes, and security. There are many tools to monitor and maintain your systems; these should also align with your organization’s goals and strategies.
Regular updates: Schedule and enforce regular software updates and security patches to protect against vulnerabilities. This is a basic tenant of device management but is often overlooked. It should also include all device types — often overlooked is mobile devices, such as cell phones and tablets. Ubiquitous devices are commonly used in business today, as much or more than traditional desktop operating systems. Don’t overlook the need to keep these devices and their software patched. Another common avenue for cyber criminals to attack is unpatched third-party application software. Ensure both the operating system and application patches, as well as BIOS and firmware, are updated to help prevent a software breach.
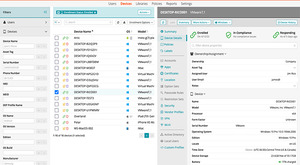
Patch, secure, and manage every endpoint
8. Review and make adjustments
Performance reviews: Regularly assess the endpoint management strategy’s effectiveness in meeting your organizational objectives and compliance requirements. Change is inevitable, and with the rapid pace of changing economic times and technology, a strategy must be regularly reviewed to ensure it’s effective.
Adjusting strategy: Once changes are identified, be prepared to make adjustments to the strategy based on evolving technology trends, organizational needs, and feedback from users and IT staff. Without adjustments along the way, the strategy may become ineffective or inefficient, neither of which is optimal moving forward. Continuous improvement, however, will align with business strategies and goals as they change to meet the future.
9. Don’t overlook disposal and replacement
Lifecycle management: Plan for the end-of-life of devices with secure disposal practices and a replacement strategy that considers the latest technological advancements and organizational needs. Not only does this ensure the data on those devices is cleaned or removed, but it also aligns with any green policies your organization has. Some regulations require proper disposal of e-waste and confirmation or a certificate of disposal; keep these in mind when doing end-of-life device planning.
Conclusion
The evolving landscape of endpoint attacks necessitates a proactive approach to endpoint management. Organizations must acknowledge the rising threat and take decisive action to protect their endpoints. Through careful assessment and strategic planning, organizations can establish a robust endpoint management strategy that strengthens security posture and mitigates risk. With continuous monitoring and maintenance, businesses can adapt their strategies to meet evolving needs and consistently maintain control and security over their endpoints.