This video on managing database security is part eleven of an overview of key DBA features in Toad for DB2 z/OS.
Related Articles
Database as a Service using Enterprise Manager – Part X
In our article series, we are exploring the capabilities of Oracle Enterprise Manager Cloud Control 13c for the private Database-as-a-Service (DBaaS) cloud – including the setup of such a cloud. In t...
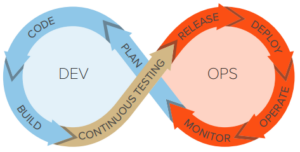
Get More Agile: A Toad DevOps Toolkit Primer
Hi, This article will focus on a new set of tools from Quest called Toad DevOps Toolkit. The Quest people are providing useful Toad functionality that is easily integrated into today’s continuous-flow...

Toad for SAP Installation demo
This video walks users through the download and installation of Toad for SAP Solutions....
