
In 2020, we’ll see NIST guidelines and MITRE ATT&CK security mitigation recommendations adopted by a growing number of enterprise organizations to safeguard their Active Directory and Office 365 data. Neither of these guidelines are required, but they sure provide best practices around 2FA, passphrases and Zero Trust as well as insight into the likely avenues of attack and how to defend against them.
This post is my first in-depth prediction for 2020 (see all 7 predictions here) , and I will outline what each of these organizations provide, how that impacts Active Directory security and where you can go to get more information.
What is the NIST Cybersecurity Framework?
On February 12, 2013, in Executive Order 13636, the National Institute of Standards and Technology (NIST) was directed to work with public and private stakeholders to develop a voluntary framework for reducing cybersecurity risks to critical infrastructure.
The resulting NIST Cybersecurity Framework applies to every organization, regardless of size, industry vertical and IT complexity. The standard is not mandated or compliance-focused; rather, it empowers IT organizations to establish an ongoing process for improving their cybersecurity posture.
In regards to Active Directory, there is no better place to apply the five cybersecurity functions of the Framework:
- Identify: Which assets need protection? i.e., identify highly privileged users and groups.
- Protect: Which safeguards are available? e.g., 2FA, Zero Trust on changes to objects in the directory, etc.
- Detect: Which techniques can identify incidents? e.g., endpoint monitoring, PowerShell monitoring, Active Directory changes, etc.
- Respond: Which techniques can contain the impact of incidents? e.g., automatic roll back of group policy changes or temporarily disabling the offending account or unauthorized PowerShell script.
- Recover: Which techniques can restore capabilities? i.e., how do you recover from a ransomware attack that takes down all of your domain controllers?
Shielding user credentials from attacks with NIST is a must do for every organization.
What is the MITRE ATT&CK Matrix?
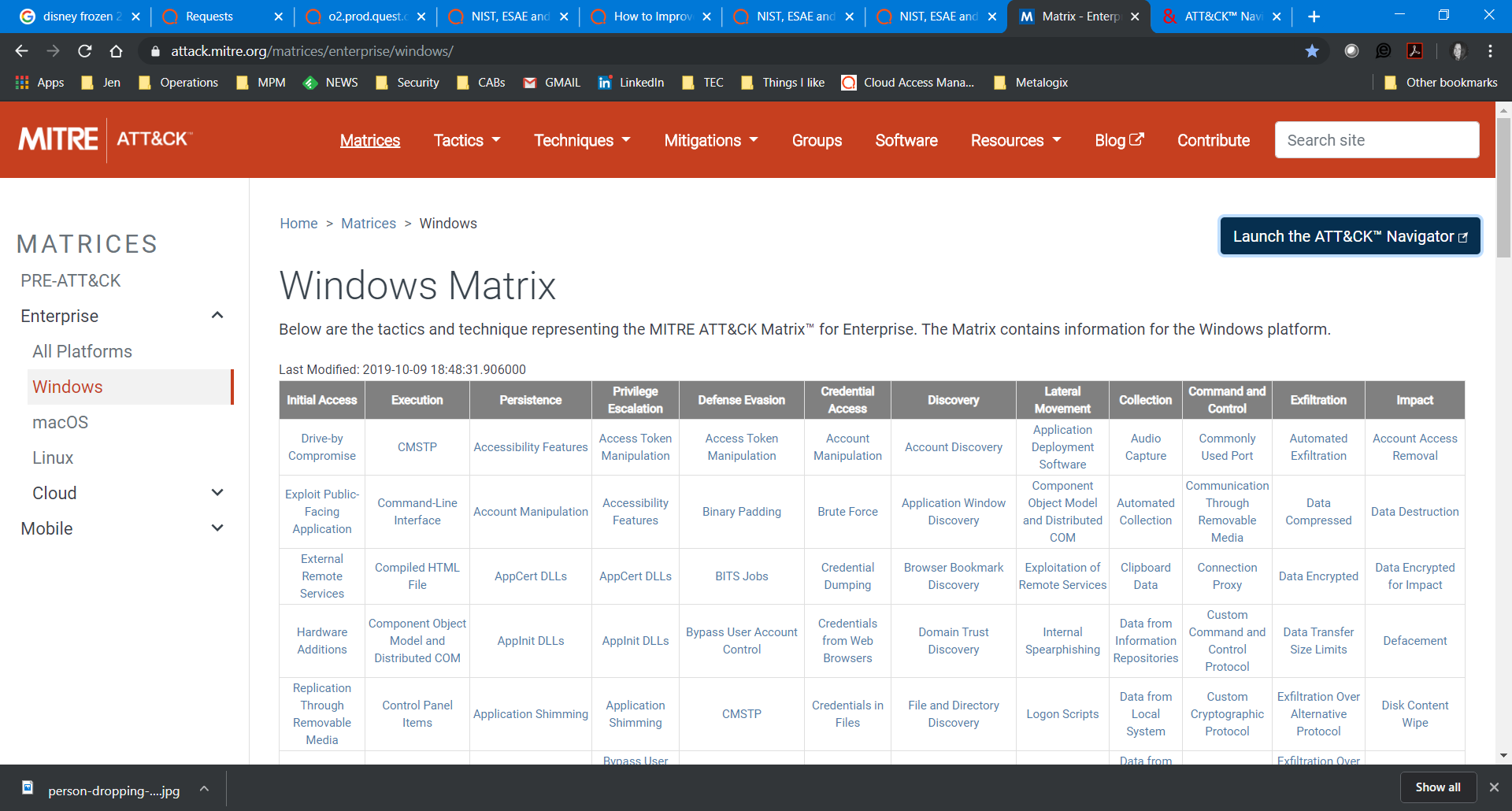
Another way to secure your environment is to understand the methods attackers employ from their tool box. Enter the MITRE ATT&CK , a “knowledge base of adversary tactics and techniques based on real-world observations.” This is a free resource built by the collective cybersecurity community.
Of particular interest to you is the Enterprise Matrix for Windows. Here you can dive into the various attack methods according to the attack tactics and learn more about how it’s used, what permission is required to run that attack, mitigations and how to detect the attack.
Every attacker has their methods and MITRE ATT&CK has quickly become the place to go to understand those methods and take steps to protect your environment.
Resources to help you get started with NIST and MITRE ATT&CK
To get started with NIST, I encourage you to read more about the framework and how it complements Microsoft’s ESAE (“Red Forest”) as models for protecting credentials, particularly those that reside in Active Directory in the whitepaper entitled How to implement NIST, ESAE and Red Forest Cybersecurity Principles in Active Directory.
- Domain groups and members
- Domain users
- Domain summary
- Active Directory permissions



