
Security has become a top concern for organizations around the world. And as content continues to move into the cloud, organizations are doubling down on how they can ensure the safety of their sensitive and personal information.
Why? If we look at the numbers, over 1.9 billion records have been leaked, lost, or stolen during the first half of 2017, which significantly surpasses the number of total incidents in 2016. While many perceive that only public brands are at risk of data breaches, occurrences in 2017 proved that hackers can and will target large organizations, such as HBO and Equifax, as well as SMBs like CloudPets.
How do security breaches tie into Office 365?
Let’s jump back to Office 365. In light of the increasing rate of data breaches, what exactly is Microsoft doing to ensure that Office 365 is as secure as possible?
First of all, Microsoft deploys a defense-in-depth strategy to protect data through multiple layers of security. The image below showcases the Physical, Logical, and Data layers of security.
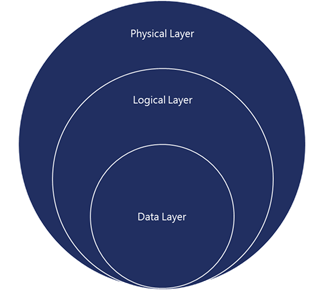
The Physical Layer
The Physical Layer is how Microsoft prevents people from physically getting into the data center and accessing data. Microsoft data centers are designed to protect data against unauthorized access by employing strict protocols and security features, including:
- Multiple authentication protocols: Badges, smart cards, biometric scanners, and on-premises security.
- Constant surveillance: Motion sensors, video surveillance, and security breach alarms.
- Restricted access: Access is restricted by job function, meaning data center employees lack access based on their responsibilities.
The Logical Layer
The Logical Layer comprises the controls and processes to secure the physical hosts and applications from administrators, including:
- Automated operations: Human intervention is reduced to a minimum, reducing the risk of malicious activity or inconsistent configurations.
- Monitored admin access: Data is controlled via multiple layers of security, including a Lockbox process, which allows:
- Just-in-time accounts with high-entropy passwords.
- Access for a limited amount of time.
- Access to take specific actions based on the role.
The Data Layer
The Data Layer is how Microsoft secures data both at rest and in motion. While Office 365 is a multi-tenant service (i.e. multiple tenants share the same hardware), the data storage and processing for each tenant is segregated through Azure Active Directory and capabilities that are specifically developed to help build, manage, and secure multi-tenant environments.
How Do Organizations Begin to Safeguard Their Content?
Despite the levels of security that Microsoft employs, organizations need to implement extra layers of security to safeguard their content. In other words, whatever Microsoft does to secure their service is useless if users leave their login information and their laptop at a local Starbucks.
Microsoft offers multiple ways to add extra security (like Multi-Factor Authentication), but these are not enabled by default. Microsoft’s Office 365 Secure Store allows admins to enable security configurations for a more secure environment. To access the Office 365 Secure Store, navigate to the Office 365 Admin Center, or directly to https://protection.office.com.
Assessing Your Office 365 Security Risk
It may not be a guarantee, but following security best practices can decrease the chances of exposing sensitive content to a breach.
Upon accessing the Office 365 Secure Store, click on the “Go to Secure Score” link to get more details into your Office 365 security risks. In the following image, you can see my current score of 68 out of 452.
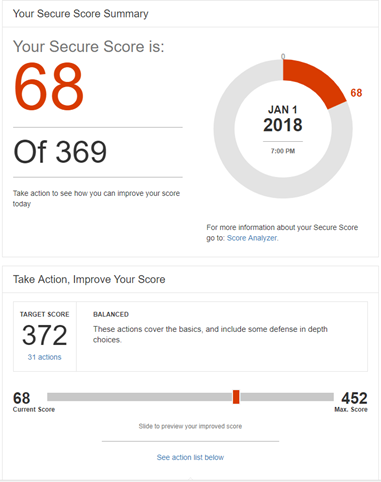
Note that I’ve set myself a target of 372. A target of 289 to 372 is considered “Balanced” between user impact and the security measures that I need to implement. It also recommends 31 actions that I can implement in order to reach my goal.
Let’s take a look at some of those actions.
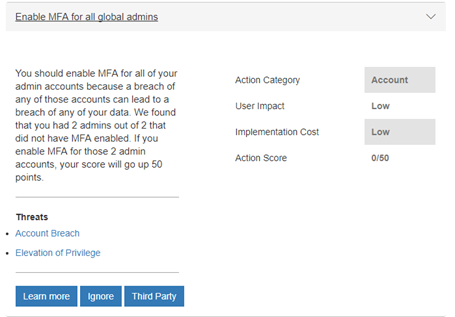
Multi-factor authentication
Some actions can be worth a lot more than others. For example, one of the first things that I can do is enable multi-factor authentication for all the Global Administrators in my tenant. Currently, 0/2 of my Global Admins have it enabled, so if I enable it for both of them, I would gain 50 points on my score!
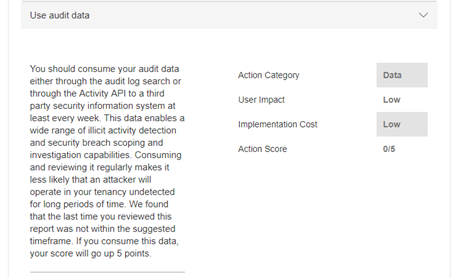
Audit data
Some of the actions are also things that you would need to do on a regular basis, like reviewing audit data information on a weekly basis. Once I review it, I will get five points added to my score; but if I don’t review it again in a week, it will go back to zero.
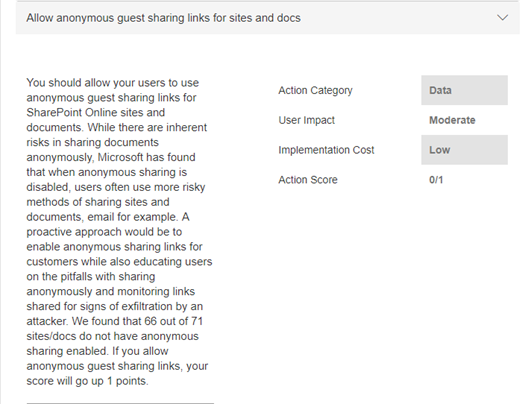
Guest sharing links
Some actions are recommended based on Microsoft best practices, rather than your initial impression of a feature. For example, Microsoft recommends enabling guest sharing links for sites and documents because their research has shown that when these are disabled, users will resort to a less secure way of sharing data.
This action may not worth a lot (i.e. 1 point), but it’s something to consider. If users need that feature, would you rather have them use it in a controlled way in Office 365 or via a service that you have no idea about?
Where Shadow IT comes into play
This brings us to the topic of Shadow IT, or better yet, finding the balance between security and productivity.
One of the major problems that organizations face with locking down their collaboration environments is that their users will introduce consumer-level tools to achieve their daily tasks and stay productive. This puts the organization at more risk of data breaches than opening up certain features, and this is where recommendations like anonymous SharePoint sharing links arise.
Conclusion
Office 365 is one of the most secure collaboration suites in the world, and it’s proven and certified by numerous compliance areas, such as HIPAA, FedRAMP/FISMA, ISO 27001/ 27018, and more.
While Microsoft provides their users with plenty of tools to decrease the risk of data breaches, it is your duty to ensure that logs are audited, tasks are reviewed, and security configurations meet the level of security that your organization needs.



