Tags: IBM DB2
Related Articles
![How a Code Review Tool Can Help You Write Team-friendly PL/SQL [Webcast]](https://s38063.pcdn.co/wp-content/uploads/2025/09/fi-Ask_Toad_2020_Code_Reviews-300x200-1.jpg.optimal.jpg)
How a Code Review Tool Can Help You Write Team-friendly PL/SQL [Webcast]
Anyone writing PL/SQL code knows there’s a good chance other team members will have to read, interpret, alter and maintain that code at some point. That’s why it’s so important to use a good code revi...
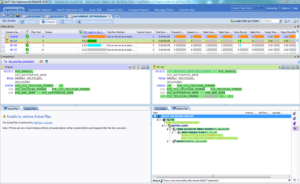
SQL Optimizer for Oracle – a success story
Here's a SQL Optimizer success story! SQL Optimizer for Oracle automates the SQL optimization process and maximizes the performance of our SQL statements. SQL Optimizer analyzes, rewrites, and evalua...

Oracle CREATE ROLLBACK SEGMENT Insights
A Rollback Segment records the old values of data that were changed by each transaction, whether committed or not. The information in a rollback segment is used to: Generate read-consistent database ...
