Learn how to access and process data using the transformation and cleanse utility in Toad Data Point.
Related Articles
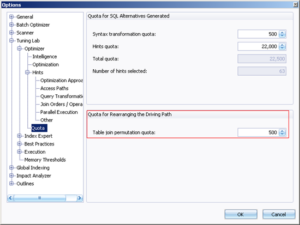
Rearranging the Driving Path
This tip covers the importance of finding the best “driving path” for retrieving rows from the database. We’ll use a simple illustration of a Nested Loop operation that retrieves data accessing 2 tab...
How to use external objects in Toad Data Modeler
Learn how to manage external objects in your models....
SQL SERVER – Error: 566, Severity: 21 – An Error Occurred While Writing...
Have you ever been in a situation where SQL Server shuts down by itself? It sounds strange but I met across a gentleman in flight who reported this issue to me. Since I was curious to know the cause, ...
